For this tutorial we will be using kali Linux iso which can be found on their official website and wce(windows credentials editor) which can be found at
Download the universal version if you don’t know the target system architecture (32 bit or 64 bit).
Windows Credentials Editor (WCE) is a security tool to list logon sessions and add, change, list and delete associated credentials (ex.: LM/NT hashes, plaintext passwords and Kerberos tickets).
First of all make your pen drive bootable with kali linux (you can choose any other linux distro) and then copy the wce.exe to the pen drive and then boot up the kali linux with the PD on target system and from the boot menu choose Live boot option and hit enter.
Now after OS boots up go to File Manager and browse to other locations and choose the 16 GB volume (size of the windows installation which will be different in your case).
Now browse to the Windows/System32folder.
Now rename the Utilman.exefile to any other name and then rename the cmd.exeto Utilman.exe.
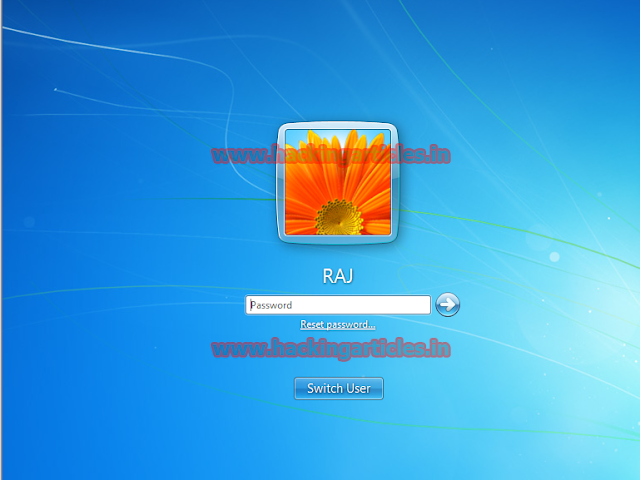
Now restart the system but this time doesn’t boot the system to kali Linux, let it boot to the installed windows and you will be presented with password screen after choosing the user.
At the password screen to lower left side a blue icon named ease of access will be present, click on it and a command windows will be opened
Now you have to execute the wce.exefile in the pd so type the following command to know the external devices connected:
diskpart (a windows command line utility which enables us to manage disk and partitions)
and then on diskpart prompt type command:
list volume (show all the connected drives)
Now choose the FAT32 Fstype drive (to be sure also confirm the drive name with the size of your pen drive)
In my case it is F. Now exit the diskpart by pressing ctrl^c.
So now browse to the pd by typing the following command: f: (Here f is the drive letter name In your case it could be different) and then execute the wce.exe file which you copied previously with command:
wce.exe –w (-wis used to dump all the passwords in clear text)
As you can see it has successfully dumped the password in clear text.